We Launched a Live Brand Styleguide

As much as The Tor Project focuses on the quality of our code, our crypto, and our infrastructure, making trustworthy software that is usable and useful depends on more than just technical details. As our tools become popular with an ever-larger group of people around the world, we also have to focus on the User Experience (UX) that these tools present.
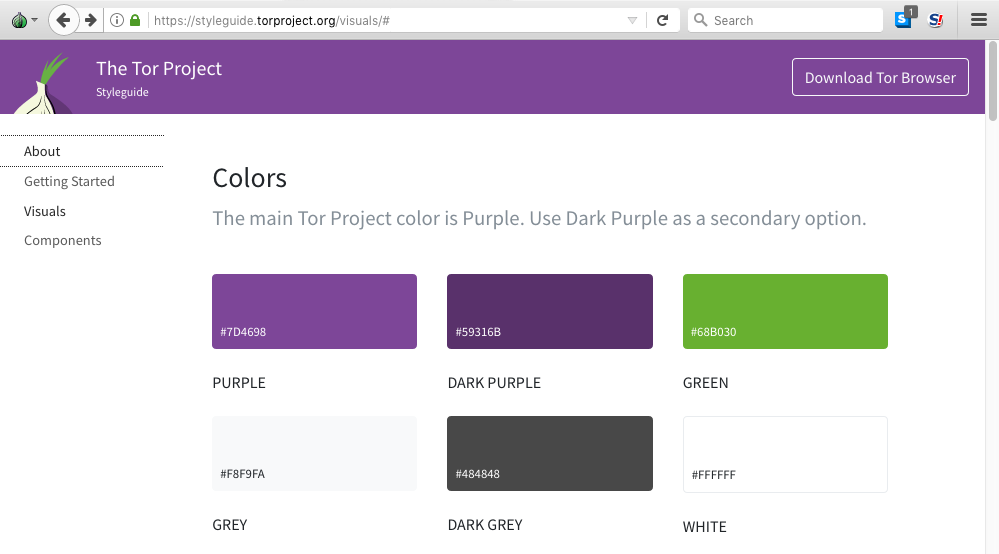
Early in 2017 the Tor UX Team received support from The Open Technology Fund's Usability Lab to create a basic visual styleguide, with the help of Ura Design and Simply Secure. This styleguide has allowed us to begin the work of creating a consistent visual look and feel across the entire project's ecosystem by standardizing fonts, colors, and logos. This consistency is important because it reinforces community identity and helps us to build user trust by identification. By making sure all our tools "look like Tor", we also build users' confidence; when a tool looks professional on the outside, it's easier to believe that the insides are high-quality as well.
Visual consistency never happens overnight. We have been implementing the guidelines across platforms, and there are still many big changes to come (a redesign of our website is underway). But the Tor community and ecosystem is vast, and more than just a few people utilize Tor's style for their work.
So to help guide us all in our contributions, we are proud to announce the launch of our first live brand style guide.
The live Tor Styleguide is based on Bootstrap, an open-source toolkit for developing with HTML, CSS, and JS, and it's ready to integrate into your project today. As with all our work, we believe that making high-quality resources open and available to everyone makes all of our efforts more successful.
To use the Tor styleguide, you can download our CSS style and import it into your project. Alternatively, you can also clone this repository and use our SASS files. The guide takes Tor Browser users in high-security mode into consideration; only a few elements are affected if you disable JavaScript.
The styleguide is a living resource, and we are updating it often. If you have ideas and want to get your hands dirty, or you just have any suggestions, please join one of our UX meetings, check out our repo, or DM us at ux@torproject.org.
We at The Tor Project are passionate about empowering all sorts of users to protect their privacy and their identity online. We are excited at this latest development and its potential to help our community in its efforts help people around the globe.
Comments
Please note that the comment area below has been archived.
Hi…
Hi.
issue found in the article.
The link "live brand style guide. " point to a wrong url: "https://vbdvexcmqi.oedi.net/styleguide.torproject.org"
should be: "https://styleguide.torproject.org/"
Greetings!
Thanks for the tip!
Thanks for catching that!
Oi quero entrar
Oi quero entrar
I am very happy that Tor…
I am very happy that Tor Project has gotten around to redesigning the website! And I agree that in this day and age, visuals are important.
On the visual side, I request that the re-designers test the site before it goes live to ensure can be used (perhaps with somewhat reduced functionality)
o by Tor users who have chosen higher settings in the security slider,
o in particular, who have chosen to disable javascript,
o provide easily spotted drop down menu or links leading to available translations,
o consider choosing large fonts to help people with poor vision,
o consider choosing a scheme which can be perceived by someone with one of the three major types of color blindness (R has a package which can help you there),
o try to keep the design "uncluttered", keeping in mind that many newbies may be highly stressed by frightening events where they live which have prompted their strong interest in ensuring their own privacy/safety.
On the content side, please try to ensure that
o in the main page, the most important stuff comes first
o pages (at least those linked from the home page) have "last modified on aa/bb/cc" types dates
o if possible, regularly review the most important pages to make sure they are up to date
o if possible, provide a clear, thoughtful page similar to "telegraphic advice" from sources such as Tails Project, Micah Lee (The Intercept), EFF, Wired, on "how to use Tor safely", which takes account of information in the Snowden leaks, at Citizen Lab, and other sources of how state-sponsored attackers think and how they operate, and links to further resources (e.g. signal home page, how to request accounts at Riseup)
I suggest that the "opsec advice" page might also link to a FAQ style page which attempts to systematically debunk false assumptions which many people have, with links to news stories reported by The Intercept, NYT, Wired, The Guardian, Bloomberg, etc. or reports from HRW, Amnesty, Citizen Lab, etc., on state-sponsored cyber-espionage/cyberwar. In particular, an excellent recent example debunking the myth "I am too innocent/too poor/too insignificant to be hackworthy" is the report that alleged RU hackers stole the identities of US citizens who happened not to have Facebook/Twitter accounts for the sole purpose of obtaining Facebook/Twitter accounts for their "influence operations", aka "election meddling". It would be helpful to try to include examples of FVEY/EU/RU/CN and various African nations (e.g. Ethiopia, Kenya) and Latin American nations (e.g. Mexico targeting soda tax advocates) where appropriate, to drive home the point that many governments to do this--- not just inside their own borders--- and that TP is not aligned with any nations self-defined--- and usually secretly defined--- "national interest".
Another dedicated webpage might address the difficult topic of state-sponsored "influence operations" (e.g. FVEY, RU) which have been revealed by the Snowden leaks (GCHQ's JTRIG toolbox) and exposes in the Guardian/NYT/Wired/etc of RU operations.
Another topic worth covering in a dedicated webpage is the difficult issue of TP's historic ties to certain USG agencies such as NRL, the US State Department, arma's summer internship at NSA decades ago, and public-private entities such as NED, etc., and grants from less objectionable governments. Also important to explain here: TP's attempts to move away from the USG funded model to a user-donation funded model.
One myth which can be debunked with great care is that "there is no defense against NSA"; the Snowden leaks show pretty clearly that as of 2012 NSA/GCHQ were having great difficulty breaking Tails and even recent editions of Tor Browser appear to have been hard to target. Obviously these sources are hard to interpret and may not accurately describe the situation in 2018, and it should be explained as clearly as possible how our estimates of the current ability of a "near-global adversary" to deanonymize Tor users depends on many factors, such as how many people regularly use Tor in your geographical area, how often/carefully you use Tor, etc. Also the significance of visibility of connections to the Directory Authorities should be explained.
Another dedicated webpage could try to explain how the various kinds of bridges work and what anonymity protection and censorship evasion capabilities they are thought to have, e.g. against GFC, SORM, FVEY's global surveillance/cyberwar "implants" in IXs, telecom networks, Google, Amazon, CDN networks, etc.
Another dedicated webpage (possibly) could try to explain clearly and simply
o what role cryptography plays in ensuring
+ communications privacy
+ data integrity
+ authentication
o what kinds of crypto are currently used in Tor,
o what kinds are being considered for the future (e.g. elliptic-curve cryptography, quantum cryptography).
Also, if possible get EFF's permission to use their excellent picture explaining the onion concept. USG documents are public domain, so you can probably also safely use figures NSA prepared for slide presentations which were leaked by Snowdwn!
Oh yes, also very useful would be a "bulletins page" where TP can promptly announce suspected DDOS or other attacks (as per FBI/Carnegie Mellon) on the Tor network or on the website or on the blog, and give some information about "emergency fixes" for the most urgent flaws (e.g. Shellshock, Meltdown/Spectre).
> what kinds of crypto are…
> what kinds of crypto are currently used in Tor,
crypto on the network or on the tb ? it is not at all the same thing , both are not oriented security in mind, it is not the goal of Tor.
>TP can promptly announce suspected DDOS ... (e.g. Shellshock, Meltdown/Spectre).
- dos blackmail or subpoena ?
- meltdown/spectre have nothing to do with tor and are undetectable (intel launched a bluff policy/politic since at least 20 years without to be able to built only one good processor , that's the purpose of an aggressive publicity campaign : sell iron at the price of gold) ; i do hope that china, russia, or another founder not yet known will produce a safe product built with intelligence & competence in mind (it is not at all the case of intel).
> what kinds of crypto are…
> what kinds of crypto are currently used in Tor,
>> crypto on the network or on the tb ?
I meant, crypto currently used in Tor products, including Tor client/server, Tor Browser, Tor Messenger. This could get rather complicated rather quickly, so I'd settle for just Tor client/server (the basics underlying most Tor products).
> TP can promptly announce suspected DDOS ... (e.g. Shellshock, Meltdown/Spectre).
>> dos blackmail or subpoena ?
You mean DOJ (US "Department of Justice" [sic]), not DOS, right? If so: yes, that too.
DDOShttps://en.wikipedia.org…
DDOS
https://en.wikipedia.org/wiki/Denial-of-service_attack
* in the context, one cannot know that the site is voluntary censored by an agency, a group or an individual and why.
https://en.wikipedia.org/wiki/The_Spamhaus_Project
vulnerability
https://en.wikipedia.org/wiki/The_Million_Dollar_Homepage
extortion (blackmail : ransom)
https://en.wikipedia.org/wiki/Creepware
ddoss intrusion
https://en.wikipedia.org/wiki/ProtonMail#2015_DDoS_attacks
protonmail is working with different military consortium which israeli and therefore is untrusted (ddoss protection).
ddoss pressure
https://en.wikipedia.org/wiki/BlackVPN
blackmail
subpoena (blackmail : ransom)
https://en.wikipedia.org/wiki/Subpoena
* in the context, one cannot divulge that the site or the keys are compromised
* subpoena is often used for making a pressure.
>> meltdown/spectre have…
>> meltdown/spectre have nothing to do with tor
I fear that you are wrong about that, and with the indulgence of the moderator I'd like to explain why. Please bear with me.
For over a decade, LANL and other Military/Surveillance/Industrial Complex entities have been building and running supercomputer models of dozens of US cities in which the financial/physical/mental health status and near real-time movements of every resident, and their interactions with other people, with the government, and with the environment generally--- is individually modeled (with a caveat to be briefly explained below).
Supercomputer models? Of individual Americans and all their neighbors, their friends and relations? Yes.
Don't believe it because I say it, believe it because some of the people who have been running such simulations for decades are finally starting to talk.
This has never even been a secret, not really. LANL has always been happy to talk about such models when their putative goal is to model citizen movements (whether by car, bus, train, bike, or foot) in order to improve traffic flow in US cities. Because they know that most citizens will fail to perceive how the same kinds of modeling can be used for more problematic predictions.
Like trying to predict who may in future "do something wrong"--- according to the governments algorithmically specified definition of "wrong". Which can change over time. Which means that things you do today in the belief that they are not only not criminal but would not even be considered in any sense "wrong" by most of your peers, could in future be used to harm you, on the grounds that alleged dangerous consequences have become apparent (to some neural net) in the years since you innocently did the non-criminal and "not even wrong" deed. Or could be used to harm your friends. Or your children. Because algorithms love assocation, and harbor no ethical scruples about declaring guilt on the basis of association.
About a decade ago, some people involved in such supercomputer simulations began to discuss in obscure engineering publications the fact that USIC has built such models of entire nations (e.g. Iraq and Afghanistan), seeking to predict which individual citizens of those nations may be "susceptible" to ISIL/Taliban recruitment drives or to act as "lone wolves". The modelers would try killing a particular potential "problem person", and run a new simulation to see whether that decreased the effectiveness of ISIL more than it increases the ability of ISIS to recruit fresh blood by posting pictures of the "martyr". So supercomputer models not only could potentially be used to decide by algorithm who lives and who dies, they have been used that way for some time. Literally. To decide who lives and who dies. By algorithm.
Don't believe it because I say it. Believe it because Michael Hayden said it: "we kill people using metadata". He meant: using metadata fed into supercomputer simulations, with algorithmic decisions made according to the government-defined utility function value at the end of each simulation.
It ought to have been apparent that this such revelations have tended to confirm our repeated warnings that USG is targeting its own population with the same sort of modeling. Which it was.
@ LANL scientists: You know who you are. You know what you have been doing. And you surely know that things have progressed well past the point where you need to speak up, regardless to the risk to your career or your personal freedom. Think of the children. Aged 2-7.
And indeed, more recently, some of the people who have done this kind of modeling for decades are starting to talk about some of the more, shall we say, suggestive, supercomputer modeling of the US population, modeling which they have been doing for so many years:
https://www.wired.com/story/scientists-know-how-youll-respond-to-nuclea…
Scientists Know How You’ll Respond to Nuclear War—and They Have a Plan
Using an unprecedented level of data from more than 40 different sources, researchers can now make synthetic populations of entire cities.
Megan Molteni
13 Feb 2018
> The science of prediction has changed a lot [in the past decade]. Now, researchers like [former Los Alamos National Lab scientist Chris] Barrett, who directs the Biocomplexity Institute of Virginia Tech, have access to an unprecedented level of data from more than 40 different sources, including smartphones, satellites, remote sensors, and census surveys. They can use it to model synthetic populations of the whole city of DC—and make these unfortunate, imaginary people experience a hypothetical blast over and over again.
> ...
> You can think of Barrett’s system as a series of virtualized representation layers. On the bottom is a series of datasets that describe the physical landscape of DC—buildings, roads, the electrical grid, water lines, hospital systems. On top of that is dynamic data, like how traffic flows around the city, surges in electrical usage, and telecommunications bandwidth. Then there’s the synthetic human population. The makeup of these e-peeps is determined by census information, mobility surveys, tourism statistics, social media networks, and smartphone data, which is calibrated down to a single city block.
LANL is quite proud of the somewhat ingenious notion of "synthetic populations", which they introduced to avoid a public outcry, because even nuclear bomb designers could appreciate that Americans would consider the revelation that they are being individually modeled inside repeated supercomputer simulations to be "creepy" and even dangerous to their civil liberties. As Molteni explains, the modelers construct populations of fake people, closely based upon real data on real people, which behave statistically just like the real populations. But as any data scientist can confirm, modelers always have to "validate" claims such as "behave statistically just like the real populations" by running side by side comparisons of simulations using the synthetic populations with simulations using the real populations.
And as I keep trying to warn Americans, LANL has all the real data on all the real people, and has
literally been running vast precrime simulations of The People (the real people) for more than a decade, at the request of the FBI. Literally. Pre-crime models. At the request of the FBI. In supercomputers. Models with model you and you and you--- and even more dangerously, your children.
> So say you’re a parent in a two-person working household with two kids under the age of 10
It's not even a secret that NCTC's target group for precrime algorithmic predictions consists of American preschoolers aged 2-7 y.o.
> living on the corner of First and Adams Streets. The synthetic family that lives at that address inside the simulation may not travel to the actual office or school or daycare buildings that your family visits every day, but somewhere on your block a family of four will do something similar at similar times of day. “They’re not you, they’re not me, they’re people in aggregate,” Barrett says. “But it’s just like the block you live in; same family structures, same activity structures, everything.”
> ...
> That’s where Barrett’s simulations really start to get interesting. In addition to information about where they live and what they do, each synthetic Washingtonite is also assigned a number of characteristics following the initial blast—how healthy they are, how mobile, what time they made their last phone call, whether they can receive an emergency broadcast. And most important, what actions they’ll take.
It's unfortunate that Molteni failed to even mention the civil liberties implications of such detailed precrime modeling, but as someone who has struggled for years to explain to reporters how "synthetic populations" work, this is a really good brief description :-/
> Not everyone is convinced that massive simulations are the best basis for formulating national policy. Lee Clarke, a sociologist at Rutgers who studies calamities, calls these sorts of preparedness plans "fantasy documents," designed to give the public a sense of comfort, but not much else. "They pretend that really catastrophic events can be controlled," he says, "when the truth of the matter is, we know that either we can't control it or there's no way to know.
I have a lot to say about nuclear war too, but that may not be relevant to Tor users (although presumably of interest to anyone who does not wish their family to be vaporized in a nuclear detonation). But precrime modeling is certainly relevant to Tor users, because if you use Tor, you are probably worried about protecting your privacy and your freedom of choice. And what could be more inimical to privacy and freedom of choice than these activities?
o collecting vast amounts of detailed information (telecommunication/websurfing/travel/financial/medical/educational/employment/family histories, social media postings and other writings, responses to "surveys" (some written under a false flag by the spooks themselves) from hundreds of government/corporate data banks,
o using this data to construct detailed supercomputer models modeling every citizen and their interaction with the environment
o "tweaking" some governmental action against some targeted group (everything from changing the timing on a particular stoplight through changing zoning laws to sentencing some child to juvie prison), rerunning the simulation, and looking for those actions which most increase the government's "utility" (as measured for example in tax revenues)
o using the results to decide how to design "influence/suasion operations" targeting Americans.
Returning to
>> meltdown/spectre have nothing to do with tor
please look back at what Chris Barrett told Meghan Solteni about
> unprecedented level of data from more than 40 different sources, including smartphones... remote sensors... the electrical grid, water lines... surges in electrical usage
Consider these facts:
o many US cities have constructed electrical power "smart grids", most of them using "smart meters" made by the Swiss multinational Landis+Gyr,
o the most popular model, the AXR-SD smart meter, has features including the following
+ two-way "gridstreamRF" radio operating at 902-928 MHz, aka "the WiFi mesh", which uses spread spectrum frequency hopping (but not encryption, apparently) to tranmit all the utility "customer energy use data" (CEUD), i.e. your power usage, to a data center,
+ two-way Zigbee radio operating at 2.4-2.5 GHZ, which apparently does use garden-variety AES encryption; this is the IoT interface which field technicians or (sometimes) residents can use to monitor their own energy use
+ can store "instantaneous" Wattage use,
+ can accept shutoff commands from the Command Center,
o technicians in the L+G Command Centers (L+G has two, in FL and KS) operate most of the grids remotely as a "managed service", including processing the data and issuing shutoff commands
o the Meltdown flaw may be particularly tempting for would-be "election meddlers" because
+ someone with any presence in the Command Center can potentially bypass all protections to issue malicious shutoff commands, to particular meters or to all meters,
+ Meltdown flaw is said to particularly affect cloud computing servers, such as the L+G Command Center servers,
+ forensics experts warn that no known forensic methods can prevent/detect/confirm a meltdown attack,
+the only reliable method for mitigating Meltdown would be to buy new CPUs once new chips become available from Intel, but many utilities have straightened budgets are may not be able to afford "remedial" purchases,
+ RU sponsored hackers in particular need not reach very far to reverse engineer L+G gear, because Mosenergo (the Moscow power utility) is one of L+G's customers, and thus have a legitimate need to know all about the cybersecurity protocols used (or not used) in L+G smart grids.
o You know that (for making/receiving voice calls) your cell phone or smart phone sends signals to nearby cell phone towers, but did you know that (for websurfing) your smart phone, laptop or other device using 2.4-2.5 GHz WiFi most likely sends out "probe request" packets several times a minute to any and all nearby "access points" (APs)?
o The Zigbee interface in the AXR-SD meters which was mentioned above can apparently be configured to act as an AP, and possibly can log the MAC identifiers of every nearby device sending probe request packets.
o USG has made arrangements with large telecoms to perform dragnet surveillance on websurfing, and can force telcos to cough up which phone connected when to which cell phone tower, but in response to customer outcry, many companies are beginning to resist offering the vast amounts of data they hold on their customers to USG, and even many local governments (e.g. West Coast cities) are resisting demands from USG for various kinds of data they hold on their own citizens.
o USG can serve L+G with NSLs etc demanding all their data, with a gag order forbidding L+G from warning their customers (the US city utilities), or even ordering L+G to secretly enable some of the more dangerous capabilities of the smart meters in order to secretly "dual-purpose" the smart grids as dragnet surveillance systems, completely bypassing local ordinances which forbid dragnet surveillance or offering information to agencies such as ICE without a warrant signed by a judge.
o You may remember the infamous NSA presentation which laughed at Americans for being so stupid as to become addicted to devices (smart phones) which NSA had happily dual-purposed for incorporation into their dragnet surveillance systems, but do you see the difference from the smart grid? USG won't have to worry about "pushback" from telcos if they replace the private systems which they have already dual purposed (in secret until the Snowden leaks) as dragnet surveillance systems, because US cities have been constructing "city owned" [sic] systems which are actually operated remotely from out-of-state command centers subject to USG warrantless dragnet subpoenas--- that's why the spooks love the smart grid.
o West coast citizens of sanctuary cities in particular should note that FL and KS are not exactly known in the US as centers of progressive politics.
My point in brief: things you assume are not dangerous or relevant to civil liberties concerns or to your children's future well being might actually be very dangerous and very relevant.
I felt obligated to thank…
I felt obligated to thank you for this post due to the mere size of it... Super informative :))))))
love, Nan
This post was really long so…
This post was really long so I just wanted to redirect attention to and second the request that testing ensures the site is still usable without javascript. Especially since in the post it's mentioned that the new style will be all bootstrappy, and bootstrap is lousy with JS.
JS-free design should be prioritized, with JS added after the fact to add a little polish, rather than functionality.
The Tor website still links…
The Tor website still links to
https://trac.torproject.org/projects/tor/wiki/TorRelayGuide
not the recent revision
https://vbdvexcmqi.oedi.net/new-guide-running-tor-relay
And it this video up to date?
https://decvnxytmk.oedi.net/getinvolved/relays.html.en
Here is a suggested reply to the FAQ "How do I join Tor?"
https://vbdvexcmqi.oedi.net/join-tors-summer-privacy#comment-274216
(Links should be updated of course to point to appropriate pages in the new website.)
"Privacy is a right not a…
"Privacy is a right not a privilege"
Indeed, let this be our motto! But the font should grow louder, stronger, and more rainbow colored from top to bottom.
Ironically, this reminds me of the old Cossack fight song ("Out of a Forest of Lances and Swords") whose refrain is "Let's say it again!".
Hear *that*, IRA :)
Pugachev lives!
Re this comment…
Re this comment
https://vbdvexcmqi.oedi.net/comment/274167#comment-274167
in a recently closed thread, agree that these are becoming more common
o "mic long range"
o "call[ed] number shared"
o "phone set in restricted area with multiple redirection"
o "mail stolen"
o cell-site simulator ("Stingray") semi-localized dragnet surveillance
o aerial surveillance (with multispectral cameras, LIDAR, etc)
o networks of human neighborhood informants
In the past, Tor Project has defined itself as offering software products, which would preclude helping citizens defend against parabolic microphones, poor cybersecurity of smart phones, or stolen snail mail. But you have hit on something here: as the Tor user base grows and as cybersecurity (we hope!) improves in coming years, state-sponsored spooks (and other snoops) will increasingly be force to adopt more expensive and even more invasive methods, such as scooping up "stray electromagnetic emanations" (the methods against which a Faraday cage and other TEMPEST techniques can defend), legally mandated in-home surveillance (Google or Amazon IoT re-purposed as an Orwellian "telescreen", perhaps), through-wall RF motion detectors and through-wall radar targeting systems (now being adopted by many of the larger US police agencies), spike microphones, etc. It follows that TP should probably advise Tor users against voluntarily using Google Nest, smart TVs or other products which apparently contain an always listening hidden microphone which relays speech inside the home to a central data center, and TP should perhaps consider (even if only as a media stunt) providing not just T-shirts but also Faraday sleeves to citizen donors.
I have also urged TP to consider a brainstorming session which seeks to start developing counter measures to these threats. In particular, a spyplane detector is very doable with current technology; see the Buzzfeed article cited approvingly by one of Snowden's tweets.
The link cited spoke about…
The link cited spoke about encryption (illegal/it is not a right) and processor (legal/patent).
*Stingray is a good example (ireland/uk).
* Through-wall radar is a switzerland technology not an us one , that means that the u.s dept of technology looks for any weapon that it needs whatever the sources.
- how someone could avoid parabolic microphones ?
- a T.V. works like a radio : emission/reception so every home transmit all you say.
About counter measures, i know that someone created a stingray radar and it works and i read that snowden implemented a counter-measure (on a i-phone if i remember well) stopping the signal.
A spyplane detector ?
i heard a project that the e.u industry would like make : keeping safe every area by an army of drones , an eye, an ear, a mic , a weapon at every 10 km , some will fly the others will be put on the road. A spyplane is a toy , they plan an electronic wall ...
How Tor could be involved in a brainstorming session about counter-measures for a state-project at the scale of a country ?
> snowden…
> snowden
You are probably thinking of Haven:
https://theintercept.com/2017/12/22/snowdens-new-app-uses-your-smartpho…
Edward Snowden’s New App Uses Your Smartphone to Physically Guard Your Laptop
Micah Lee
22 Dec 2017
https://developers.google…
https://developers.google.com/recaptcha/docs/faq#my-computer-or-network…
GOOGLE RECAPTCHA BLOCKING TOR ON ALL LEVELS!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Stops using Google's search…
Stops using Google's search engine and switch to StartPage. I too am fed up with the f**king recaptcha so I decided to switch. Besides, StartPage is using Google's search engine (without the tracking).
Users of Tor Project (and…
Users of Tor Project (and similar security projects) need agressive enforcement of visual trademarks so that the consistent style can't be legally imitated. Also every page needs a little trademarked icon that is heavily advertised to mean "This icon always appears on Tor project software and recommendations. Absence means we didn't write it. Presence might mean we did." Clicking the icon triggers some validation process that needs constant development and lots of support. Perhaps this icon should belong to an independent project devoted to protecting its members' users from malicious imitators.
How would this be different…
How would this be different form the Norton Secured Seal? (And why doesn't torproject.org have a Norton Secured Seal?)
> Users of Tor Project (and…
> Users of Tor Project (and similar security projects) need agressive enforcement of visual trademarks so that the consistent style can't be legally imitated
You mean, with lawsuits? I don't think TP should waste its time with that except perhaps in the most extreme cases. Further, I think TP should adhere to the general principles of open-source, which means encouraging other projects to reuse code and such. Going after alleged infringers doesn't fit with that.
> "This icon always appears on Tor project software and recommendations. Absence means we didn't write it. Presence might mean we did."
That might be a good idea, but it doesn't require TP filing any lawsuits against alleged "infringers".
Let's just hope the new…
Let's just hope the new website doesn't have the same path as the older blog.
White background that kills the eyes on header, center and right which doesn't help separate things neither, oversized pixellated images for 2-3 lines of paragraphs, inconsistent character padding and size, huge gaps between comments number and "join the discussion" etc.
Old blog design maybe looked aged but was much more sharp and looked far more serious. This one does look like its just from a default wordpress theme with Tor brand CSS colors over it.
I agree with preferring the…
I agree with preferring the old blog style better.
Hello Tor Team…
Hello Tor Team
Please enable Bitcoin donations.
Thanks.
any way to set tor os specs…
any way to set tor os specs as default win10 or something similar? or may win 8.
Neo: I see a promising…
Neo: I see a promising vision on the horizon.
The year is 3001.
The Tor Project finally deploys a public web forum, where users can share tips and tricks with each other. Indeed, a place where they can frequent and call home.
Not sure whether you were…
Not sure whether you were being sarcastic, but what you describe sounds more like Facebook than like Tor Project.
I tend to think that what The People need most is not an on-line "home" (even if it is nicer than the real world), but privacy. That will require eliminating agencies such as NSA, CIA, TSA, HSI, FSB, GRU, Voice of China (the newly created propaganda giant), etc, etc, and putting out of business their contractors, such as Gamma, Hacking Team, SCL, Cambridge Analytica, etc, etc.
No-one ever said democracy was going to be easy. But the less you struggle the faster and the worse things get. We've seen this dramatically illustrated over the past 17 years.
"Privacy Is Right Not A…
"Privacy Is Right Not A Privilege"
Making The Web Great Again!
some sites you enter…
some sites you enter initiates a download. is this to disclose your ip? it seems like it. no download link found anywhere but activated once you enter the site. can you ip be disclosed by this type of download hack?
> some sites you enter…
> some sites you enter initiates a download
Without more detail, it is impossible to know what you encountered or whether Tor Project can help protect you from it.
It's possible that you detected something fairly innocuous like a video which loads automatically when people visit some site, e.g. a news organization. If that sounds like what you encountered, https://vbdvexcmqi.oedi.net/comment/reply/node/1511/comment_node_articl… increasing the security slider in Tor Browser.
What the hell is going on…
What the hell is going on thos tor browser I dont know,
From last 10 days I am unable to access my files nd all files r infected by ransomware virus named as .CRAB. All my files have been corrupted. And now I unable get my files. All my hardwork, my project details and all my data have been affected. All my project , design, nd evwry files have been corrupted.I sharing everywhere to be aware of these browser.
Could you all feel that what is going on me now. Finally they are asking money to recover my files.
What is going on here!! You people don't have humanity to do thid kind of things.
You've been hit by…
You've been hit by ransomware? That's awful, but why are you blaming Tor Project?