Updates on Kazakhstan Internet Censorship

Two weeks ago we announced the use of deep packet inspection to censor the Internet in Kazakhstan. Over those two weeks we've continued working on how they are blocking native tor connections. The good news is that our obfsproxy bundle continues to work well in country. Thanks to wanoskarnet, ann, and others for their help.
We have some network-level data captures at both ends to help us assess what is occuring. It seems the Kazakhstan firewall finds something unique in the TLS "Server Hello" message as sent by the Tor relay or bridge and therefore blocks subsequent communications. IP address and TCP port are irrelevant to the censorship. Research continues. Anonymized network flows are available here:
.kz client to relay: https://media.torproject.org/misc/2012-02-28-tor-kz-client-flow.txt
and
the relay view of that same conversation: https://media.torproject.org/misc/2012-02-28-tor-kz-bridge-relay-flow.t…
Here's a graph of what this censorship looks like nationwide. The red dots are probable censorship events.
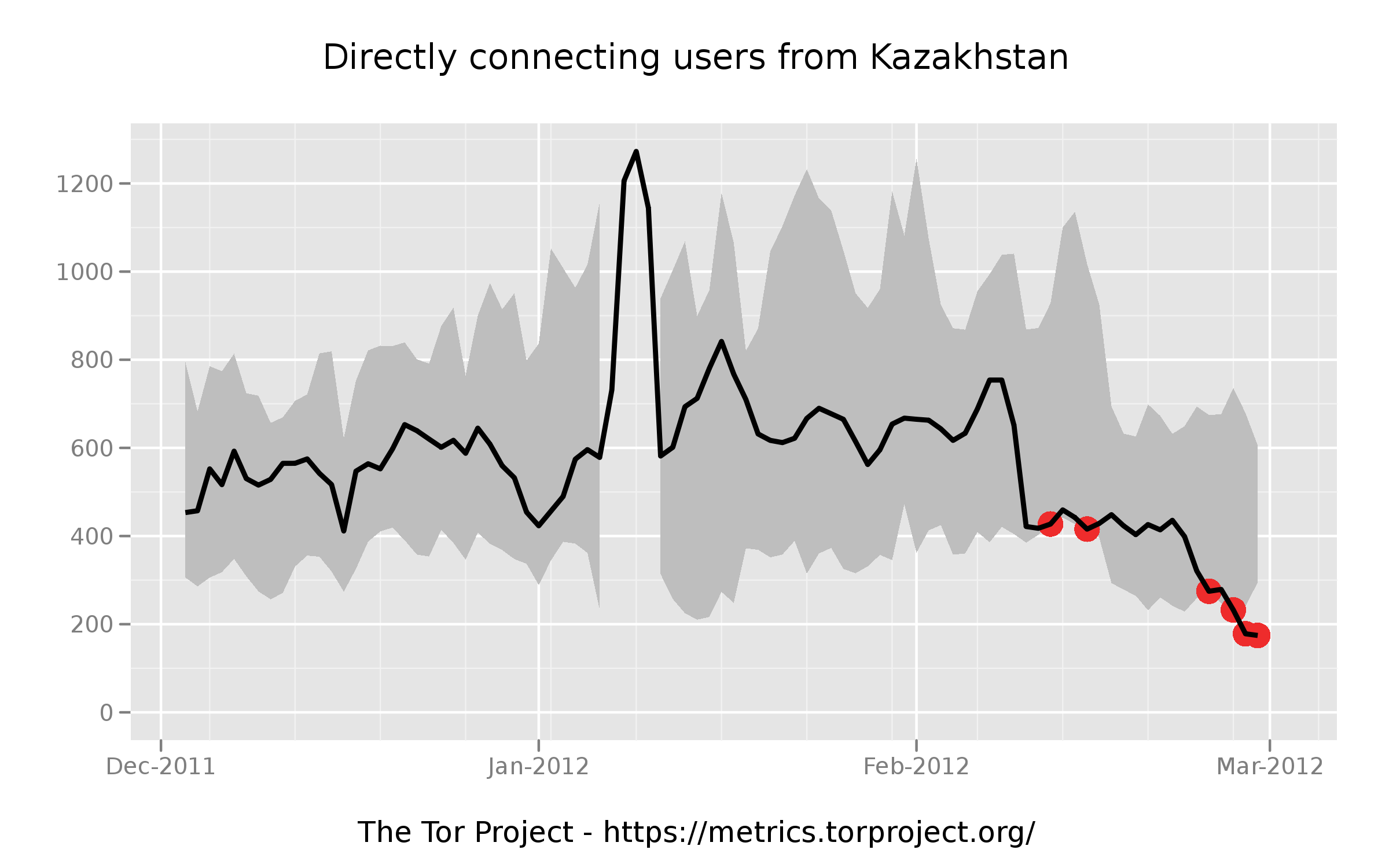 . The full image is here, https://media.torproject.org/image/blog-images/direct-users-off-2011-12…
. The full image is here, https://media.torproject.org/image/blog-images/direct-users-off-2011-12…
Comments
Please note that the comment area below has been archived.
Approve the comments
Approve the comments here:
https://vbdvexcmqi.oedi.net/blog/new-tor-browser-bundles-linux#comments
or are you a cowardly lion?
i thought so
Offtopic, but I have a bit
Offtopic, but I have a bit of a question.
Are there any security risks/is is plausible to set up a web-based proxy? I'm saying to set it up similarily to Glype(You visit a url, and it serves your webpages. It acts as your browser for you, and it acts as a proxy. Websites see this glype'd website's IP instead of yours), but instead of it serving the server's IP, it takes advantage of TOR relays. Anyways, is it plausible, and would people use it?
~Jarwain
Do you mean like a reverse
Do you mean like a reverse proxy for the tor network?
What about filering on
What about filering on certificate on the server hello ?
I think about Subject commonName of Certificate used by tor.
Example:
- A simple rule: does the commonName resolve to DNS ? (and not wildcard)
- A more complex: what is entropy of commonName ? (as Tor use strong alea fo generation of commonName, with www.XXXXXXX.net)
Or more simple using length of certificate, as Tor certificate are simple (the issuer is not a chain a certificate) and so, there are short: certificate length < 500.
A wireshark rule like: "ssl.handshake.certificate_length < 500" report only tor connection for me (but not test on a big connection pool).
Hope that help.
Hello Tor project. Im user
Hello Tor project.
Im user from Kazakhstan, i cant use Tor, because my ISP block this.
I downloaded obfsprohy, but it did not help. Please contact me, please. Those who can help me.
E-mail: millermax34@gmail.com
I downloaded obfsprohy, but
I downloaded obfsprohy, but it did not help. Please contact me, please. Those who can help me.
e-mail: millermax34@gmail.com
Tor check told me I wasn't
Tor check told me I wasn't using Tor with this IP:
93.114.43.29
A search led me to your Tor's Dec 2011 status report comments section where another user posted the same error.
This IP does not appear at blutmagie's tor node listing site as of this posting date, it too said I wasn't using Tor, but I am.
Please backlist this IP address: 93.114.43.29
As it appears something, "funny" is going on here.
Thanks a lot for the tip
Thanks a lot for the tip (and your work for developing essential for us software). Downloaded the obfsproxy bundle and it works.
Our gov's cencorship struggle sucks.
In Kazakhstan, completely
In Kazakhstan, completely blocked Tor and bridges!
Works only obfsproxy-bundle.
Nazarbayev - fu...ing fascist, destroying their own people!!!
Hi. I'm from Kazakhstan.
Hi. I'm from Kazakhstan. Seems that tor 0.2.2.29-beta works !
I'd like to try this bundle from another place, but can't find win32 distro...
(i wrote this using tor right now ;)
For Kazakhtelecom users:
For Kazakhtelecom users: simple tor bundle 0.2.2.29 is working at some business networks, but not in home adsl. At "home adsl" network "tor obfuscating bundle" (0.2.3.13) working ok. Good news, but we need more obfs2 bridges in future.
Hi! ( Privet bratan! )
Hi! ( Privet bratan! )
Where did you find the version (obfuscating bundle) (0.2.3.13) ?
The site has only version (obfsproxy-browser-bundle-2.3.12-3)
Obfuscating bundle also
Obfuscating bundle also working here for me (in Astana). Note: I have also noticed some business connections (one through KazTransCom, though they feed into KazTelecom's network) are NOT censoring some sites like Wordpress, Livejournal, etc. where home connections through Megaline still ARE. Some selective censoring going on? "Technical problems." That excuse didn't fly well in Tajikistan recently....
Today, GFW in china was
Today, GFW in china was updated either. I have tried obfsproxy, but it did not work. I can ping through all ip address in that bundle, yet still can't connect to the tor network.
Here is the message log:
Mar 21 19:27:07.285 [Notice] Heartbeat: Tor's uptime is 0:00 hours, with 0 circuits open. I've sent 0 kB and received 0 kB.
Mar 21 19:27:09.658 [Notice] Bootstrapped 5%: Connecting to directory server.
Mar 21 19:27:09.658 [Notice] Bootstrapped 10%: Finishing handshake with directory server.
Mar 21 19:27:13.108 [Warning] Problem bootstrapping. Stuck at 10%: Finishing handshake with directory server. (DONE; DONE; count 10; recommendation warn)
Mar 21 19:27:13.108 [Warning] 11 connections have failed:
Mar 21 19:27:13.108 [Warning] 10 connections died in state handshaking (TLS) with SSL state SSLv2/v3 read server hello A in HANDSHAKE
Mar 21 19:27:13.108 [Warning] 1 connections died in state handshaking (proxy) with SSL state (No SSL object)
Mar 21 19:27:13.201 [Warning] Problem bootstrapping. Stuck at 10%: Finishing handshake with directory server. (DONE; DONE; count 11; recommendation warn)
Mar 21 19:27:13.201 [Warning] 12 connections have failed:
Mar 21 19:27:13.217 [Warning] 11 connections died in state handshaking (TLS) with SSL state SSLv2/v3 read server hello A in HANDSHAKE
Mar 21 19:27:13.217 [Warning] 1 connections died in state handshaking (proxy) with SSL state (No SSL object)
Obfsproxy doesn't work in
Obfsproxy doesn't work in china.
Here is the message log:
Mar 21 19:40:58.570 [Notice] Heartbeat: Tor's uptime is 0:00 hours, with 0 circuits open. I've sent 0 kB and received 0 kB.
Mar 21 19:41:01.021 [Notice] Bootstrapped 5%: Connecting to directory server.
Mar 21 19:41:01.021 [Notice] Bootstrapped 10%: Finishing handshake with directory server.
Mar 21 19:41:05.282 [Warning] Problem bootstrapping. Stuck at 10%: Finishing handshake with directory server. (DONE; DONE; count 10; recommendation warn)
Mar 21 19:41:05.313 [Warning] 12 connections have failed:
Mar 21 19:41:05.313 [Warning] 10 connections died in state handshaking (TLS) with SSL state SSLv2/v3 read server hello A in HANDSHAKE
Mar 21 19:41:05.313 [Warning] 2 connections died in state handshaking (proxy) with SSL state (No SSL object)