Update on Internet censorship in Iran

Here's a quick update on what we're seeing from Tor clients in Iran. This is an update to https://vbdvexcmqi.oedi.net/blog/new-blocking-activity-iran. It appears that one of the five Iranian ISPs is experimenting in blocking censorship circumvention tools; such as Tor, Freegate, Ultrasurf, and Hot Spot Shield. There have been reports that this update to censorship technologies was coming soon, https://www.azadcyber.info/articles/1560.
Previously, we had data suggesting that ssl-connections were being throttled or experiencing a forced reduced-throughput. It seems this is no longer the case. A simple IP address access list is used to stop access to the public Tor nodes, as well as many Tor bridges. An example of this blocklist on the Iranian Tor users:
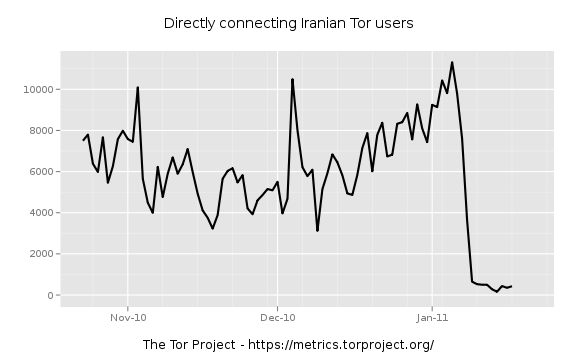
and
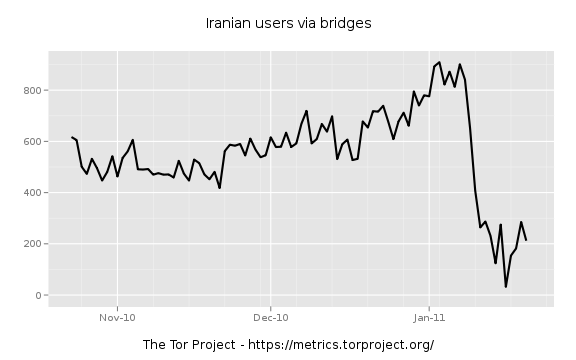
We are seeing success in users choosing to configure their Tor clients to use a socks or https proxy and then connecting to the public Tor network. The trick here is that Iranian tor users now look to be coming from wherever the open proxy is located. A few volunteers in Europe and SE Asia have setup proxy servers restricted to Iranian IP space.
On a more technical level, here's what we were seeing last week for ssl manipulation, https://vbdvexcmqi.oedi.net/files/https-traffic-flow.txt. What's interesting is the tor-server to client communication is with a TTL of 40. The TLSv1 Encrypted Alert is from the tor-server, except the TTL is 39. Unless the tor-server suddenly jumped one hop further from the client, something intercepted the connection and injected that packet on behalf of the tor-server.
This week we're seeing straight IP blocking after the ssl handshake starts, https://vbdvexcmqi.oedi.net/files/ip-blocking.txt. In both cases, this is to the same tor bridge from the same tor client as before.
In a short few months, Iran has vastly improved the sophistication of their censorship technologies. Right now, the best option is to use tor through open socks/https proxies. A risk is the open proxies can see you are using tor, but cannot see the traffic passing through the open proxy, for everything is wrapped in layers of encryption by Tor. However, it appears the Iranian Potato Wall can detect Tor or not in any case by analyzing the traffic on the wire. We have reports this is true for other circumvention tools as well.
I thank the many people that have taken risks to share data with us.
Comments
Please note that the comment area below has been archived.
yeah that unfortunate is
yeah that unfortunate is happening
I don't know why they try to do this stupid work instead of more useful works they can do
please email me any result
I'll be happy to know why tor doesn't work and what's the solution ! :(
lizadel.lucaus@gmail.com
Here is the solution for
Here is the solution for Iranian usres:
http://douran.wordpress.com/2011/01/24/aol9-6_and_tor/
(a Persian guide: How to access TOR from iran)
I tested and it worked like charm ;)
ایرانیان عزیز میتوانید از آدرس فوق، روشی جدید برای استفاده از فیلترشکن تور که در ایران مسدود شده را بیاموزید
Hi Phobos, I'm trying to
Hi Phobos, I'm trying to use Tor inside Iran, so this is very relevant and useful for me. Thanks for working on this. However, the Iranian authorities have blocked the list of proxy servers mentioned in your post (www.inet.no/dante/), and unfortunately I haven't been able to find an alternative list of proxy servers that works and isn't blocked. I'm getting a friend to email me the contents of the Norwegian website, but in future it might be really good if you could list the proxies in your blog.
Any idea? here in Iran we
Any idea?
here in Iran we don't have more access...just ur httpS torproject.org is accessible!
So they're blocking Tor
So they're blocking Tor itself but not comments to vbdvexcmqi.oedi.net? Gee, I wonder why...
Can't you do something about
Can't you do something about this? , I think you do
there is a question : how to
there is a question : how to use tor through open socks/https proxies???
As the post said,
As the post said, https://decvnxytmk.oedi.net/docs/proxychain.html.en
It seems that Tor has a
It seems that Tor has a serious flaw that makes it possible to deactivate it by "a simple IP address access list" that "is used to stop access to the public Tor nodes, as well as many Tor bridges." I should correct that by saying that none of the Tor bridges worked. In fact except for once, the request for Tor bridges from withing Gmail didn't work any more right about the same time as the new censorship.I wonder how they could stop tor from sending bridges by email.
One wonders why this could not be done by the Chinese before and they could never block Tor altogether as the Ira nians did. Nevertheless it has been done now and measures to overcome the flaw should be taken ASAP. Being very important by itself and without intending to downplay the Internet censorship in Ira n, this is a clear indication that an ingenious solution to this "ingenious" problem needs to be found otherwise tor will lose its viability in not so distant future.
Using tor from different pc's gave exactly the same line:
[Notice] No current certificate known for authority moria1; launching request.
Blocking the public list of
Blocking the public list of relays is easy, we've always known this. Enumerating all of the bridges is difficult, we've always known this. It seems the Iranian government has decided to not play the game of whack-a-mole with IP addresses, but rather take the next step in the arms race: deep packet inspection and stateful inspection of traffic flows. This is more advanced than nearly any other country in the world to date, and more so than many corporate firewalls.
Further testing indicates they are not merely detecting "SSL or not" but rather able to detect "Tor's SSL or not" and "freegate's SSL or not" and "ultrasurf's SSL or not" and handle each individually. They are able to do this for their entirety of Internet traffic in real-time. This ability to snipe traffic is both impressive and depressing at once given the scale involved.
We are working on solutions to this exact problem. Rather than play a shell game with the censors as to which technique we're going to use, we will implement platform enhancements to thoroughly camouflage Tor's traffic on the wire. Any other technique we choose is going to accelerate a tangential arms race. Millions of bridges and relays, changing Tor's SSL utilization, and other shell games simply arbitrage the speed with which Iran can deploy counter-efforts.
An ultimate end to the arms race is to make a country choose to either disconnect or not. Iran has not shown a willingness to disconnect, for it may harm their economy and anger a vastly larger portion of their citizens. Therefore, we take advantage of their need to be on the Internet and camouflage Tor accordingly.
The Iranian government has,
The Iranian government has, in less than a year and starting from scratch, caught up and now surpassed the Tor project in technical ability. Tor will now start down the cat and mouse road, which means it has already lost.
This SSL fingerprinting in fact just the beginning. Tor traffic sticks out like a sore thumb on the wire in many different ways. You've known this for years, unfortunately your progress in the matter has been hijacked by academics who care more about publishing (results which vastly underestimate the accuracy and efficiency of these attacks because of their incorrect math) and their salaries than they do the Tor users.
Tor is a ghost of what it could have been. All that's left is a source of income for paper pushers and code monkeys who cannot innovate and actively work against those who do.
Good luck to some poor Iranian kids who will go for something like Haystack instead and end up in Evin...
الإيرانيون
الإيرانيون المساعدة من الروس. وقد الروس مساعدة الايرانيين خوض حروب الأفيون ، في حين أخذ تلك الأدوية لإعادة البيع للأميركيين.
حجة الخاص بك هو ان الحكومة الايرانية قد تجاوز القدرة التقنية للتور. وأعتقد أن هذا غير صحيح. وقد أظهرت تور مرارا على مدى السنوات قدرة ذكية جدا للتغلب على مثل القط والفأر والالعاب الانفجار تماما العدو للخروج من الطريق لسنوات.
حقيقة أن مجموعة من الايرانيين غبي مع مساعدة من الروس يمكن أن تفعل ما ينبغي أن جميع هذه الشركات الأميركية والأوروبية لا يستطيع قول الكثير عن عجزها الصارخ للغرب. اخترع العرب الرياضيات الحديثة ، وحساب التفاضل والتكامل ، واستمرت إلى مهندس الأشياء الرائعة في حين أن العالم الغربي كان مشغولا جدا الماعز sexing في العصور المظلمة.
والمشكلة هي مؤقتة. سوف تور التغلب بمساعدة من العديد من العرب مساعدة لها في الوقت الراهن. العالم الغربي حمقى ولن تجد حلا.
That's hilarious. In which
That's hilarious. In which countries is torproject.org blocked? The ones whose people are too busy sexing goats, I guess...
Well, well, well. Look at
Well, well, well. Look at the cats fight now. Rather than offering help to keep the citizens of Iran from being oppressed, let's all feed on a temporarily weakened tor. Idiots and inbreds the lot of you. This is how dictators maintain power as you people fight over the scraps of a dying American Empire.
Wake up. Tunisia made progress. Iran is slipping behind. Time for another failed CIA plot to kill a leader and put another dictator in power.
You can all fight amongst yourselves or join together and defeat Iran forever. History shows you'll choose to fight amongst yourselves rather than mature and cooperate for the greater good.
Offering to "help"? As in,
Offering to "help"? As in, also receiving a salary from the US State Department? Sure, where do I send a CV? :) You speak as if Tor is an open, collaborative project. It's not, Tor is made up of *employees* who work for money, not passion. Otherwise they'd be volunteers, not professional students demanding donation money.
Tunisia made progress? Give me a break, torproject.org is currently blocked there, classified as pornography.
Good luck with that "greater good" stuff.
You seem to have a healthy
You seem to have a healthy self-defeating world view going there. I'm curious about all of the fully-unpaid "passion-only" software you run on your computer?
You seem to be saying all hope in the world is lost, because the best shot we had in terms of an open source option for censorship resistance happens to be the recipient of some government grants designed to enhance the public good (for once)?
AFAIK, no one ever sent a CV in to TOR to work there. All the names I recognize on https://decvnxytmk.oedi.net/about/corepeople.html.en were volunteers for years. At least half of them still are.
So, because of some gov't grants, people who volunteered for years were able to quit their day jobs (probably taking a 30%+ pay cut: http://www.nten.org/blog/2008/04/09/are-you-paid-what-youre-worth-nonpr…) just to put a few more than 24 hours per day into something they love.
And it's blocked now, so just give up? Just laugh at them and go back to staring at the wall? I guess you're right. Sure would like a shot or two of whatever you're drinking to pass the time though.
Sure seems to help you accomplish a lot.
I much rather my taxes spent
I much rather my taxes spent on Tor than on warmongering control freaks. Funding Tor is the best thing the State Dept has done in the past 50 years. BILLIONS are sent to shady contractors selling snakeoil getting soldiers killed globally. Tor gets a measly $500k from the State Dept and everyone bitches at them. I want Tor to get the millions spent on this stupid trusted identity crap rather than the other way around.
Anonymity sets you free. Identity is used to control you. Until you live under a dictator, you will not understand.
PLEASE HELP US IN IRAN TO
PLEASE HELP US IN IRAN TO SOLVE THIS PROBLEM BY UPDATING THE TOR PROGRAM FOR SAFE INTERNET USING.
WHAT DID YOU SAY??? I CAN'T
WHAT DID YOU SAY??? I CAN'T HEAR YOU!!! YOU HAVE TO TALK LOUDER.
I can hear the screams from
I can hear the screams from Evin prison. Can you?
خواهر کسده روزی
خواهر کسده روزی که ایران آزاد بشه تو رو مثل موش کثیف از ایران میندازیم توی فاضلاب کره شمالی
the only working program now
the only working program now is Ultrasurf and it doesn't work properly.
please help in any way you know!
thank you for your time
First Tor. Next Ultrasurf.
First Tor. Next Ultrasurf. Then freegate. Then everything else. What if Iran gets tired of the shell game and whitelists the Internet? Then what? Fools.
UltraSurf records your
UltraSurf records your traffic and sells it. Iran has bought the data. See http://rconversation.blogs.com/rconversation/2009/01/circumventing-c.ht…
use yourfreedom. you can
use yourfreedom. you can also use ssh services like the one that shell.cjb.net provides.
I've tested the tor program
I've tested the tor program in computer that was ipm (Theoretical Physics and Mathematics) client network.
Although the IPM does not apply filtering in iran, tor Can not connect to server.
Hi, what are the names of
Hi,
what are the names of the four iran isp's and which isp is experimenting with new blocking technics?
thanks in advance
Hi I'm from Iran & I have
Hi
I'm from Iran & I have serious problem to work on the net without Tor!!!
Please Help all of us in Iran
Thanks
So what we suppose to do in
So what we suppose to do in Iran?
If u could solve this problem please tell me what i must do ?
siizdah@gmail..com
hey, is there's a way to
hey,
is there's a way to spread non-published TOR BRIDGES to help these people ?
We have been using human
We have been using human social networks to spread non-published bridges. The risk is the age-old problem of an adversary discovering everyone in the network by identifying a few.
And you think those groups
And you think those groups are not entirely compromised? Heh.
We assume they are. Which
We assume they are. Which bridges get blocked and how fast has been interesting to see.
If Tor use is able to be
If Tor use is able to be identified by traffic shaping hardware, then why would it be difficult to identify unpublished Tor (bridge) nodes? I suspect the only reason this may not presently occur is that they have not found it particularly necessary to do so. If Tor communications can be identified, then it should prove irrelvant whether a bridge connection is ever published or not.
If you're unable to run through the middlemen unseen, then you have a big problem with regards the viability of the Tor system.
I've had an unpublished Tor bridge node running for a good while now and would love to be able to advertise it to those needing it, but how? I need an ability to be able to pass my details on to only a very few people. I've grown tired with trying to reestablish working bridges these days as they're always blocked so very quickly as soon as I publish to the Tor network (specifically with regards China).
I sincerely appreciate the Tor effort, but I feel the people behind it really should start to entertain more radical changes in how the network operates if they truly do wish to create what they say they do. As it stands now, Tor as a network exists only at the behest of controlling governments, a comical position considering its stated goal.
It may not work for
It may not work for everybody. That doesn't mean it fails to work for others. And thus Tor is a successful project. Ideally things will get better for those it doesn't currently work for or has stopped working for. Tor has many users and not all countries which have inhibited the free flow of communications has blocked it. Many countries have laws ensuring the free flow of information and then block certain communications. What that usually means is that they can't block anti-censorship projects like Tor even though they have a mandate to censor some things. In effect users are able to by-bass the censorship if they use Tor (which as I said can't be blocked being a general anti-censorship tool). Until the world which claims to be free decided anti-censorship tools are illegal and can be blocked the censorship they do have can be bypassed.
maybe we could just publish
maybe we could just publish a bridge one time only ?
ultrasurf is working
ultrasurf is working well
but tor is not working
ultrasurf is not working in
ultrasurf is not working in tehran anymore
from data captures made from
from data captures made from zombies, all isps are doing this today. only botnets work now.
--russian blackhat
ارتش سایبری
ارتش سایبری ایران شکوهمند شما ساعتهای نزدیک. آیا نمی شود فریب داده ای. ما پیروز خواهیم شد. شما از دست بدهند.
Google Translate: "Your
Google Translate: "Your glorious army of cyber watches closely. A Do not be fooled. We will win. You lose."
What a great society now, that threatens its people.
Workers of the world unite: Those who betrayed the revolution shall burn in hell!
it has no meaning in
it has no meaning in farsi.google translate is wrong
salam'help,pls
salam'help,pls
ultrasurf is working
ultrasurf is working well
but tor is not working
تور در ایران
تور در ایران تهران از کار افتاده است
Dear employees of the Tor
Dear employees of the Tor Project,
I fear for your future. There are adversaries and friends for which you have never even believed to exist. These exist in such an alternate world one cannot fathom the depth, money, and power they wield. Should the US Department of Defense truly wish to tackle Iran in a cyberwar, protecting assets such as yourself should be priority one. Cyberteams of the US military should be giving you money to bolster and improve your software and designs. Billions of dollars are being thrown around for technologies that are ineffective and dangerous in the hands of the untrained soldiers now wielding these cyberweapons.
Now is the time to strike. Either use these fancy tools or destroy them all. For an unrealized cyberwar fantasy is the dream of a teenaged bed-wetter.
Posit I, that your lives are in danger, both from your own government's ineptness with computers and the passion of the Iranian's. Arm yourself now, for judgment day will come upon you all too soon at the hands of those you fear the least.
Aren't you the poet.
Aren't you the poet. "Employees," "money," "billions"... pretty much sums up the Tor project. You hit the nail on the head: "passion" is why Iran has now defeated Tor. Their people don't dream of money (or traveling around the world courtesy US State Department to present some variation of the same old, ugly slides). They do it for personal reasons, whatever they may be. Tor lost the second the US Navy open sourced it.
Billions.....ha. As for
Billions.....ha. As for passion, every tor employee was a volunteer first. However, it must be the millions in salary each person makes, the beach-front properties in exotic locales, and massive hush money we all get that keep us looking like "40 and out" corporate drones who don't care. I mean, Mike Perry slipped up and exposed the vast conspiracy, so it must be true, http://archives.seul.org/or/talk/Aug-2010/msg00090.html
Hi phobos!!!!!!!!!!!! I
Hi phobos!!!!!!!!!!!!
I understand the message!!!!! There is something of very true in what the Anonymous said!!!!!!!!!!!!!!!! For example my BEEFREE addon for firefox or AdBlock Plus (Wladimir's addon, i didn't made it!!!) are free for real!!!!!!! Both are made to fight against multinational companies and to improve people's privacy!!!! There is a lot of free software, free for real!!!!!!!
Writing software or more generally doing things, with LOVE is the most important thing!!!!!!!!!!!!!!!!!!!!!!!! This is what, i think, the Anonymous wanted to say you, using the word "passion"!!!!!!!
When money are involved, people turn biased and their work becomes based on the money they can obtain from it!!!!!!!!! Capitalism is evil!!!!!!!! And, many developers don't want to lose the money once they had the opportunity to get them!!! So, they are no more independent!!!!!
They'll do what they're told and paid for, rather than what is useful for real!!!!!!!!!
People driven by the money and no more by the love in what they're doing!!!!!!!!!!!!!
I think that, when you like what you're doing, you should do it with love!!!!!!!! YEAH!!!!!!!!!! And discarding the money!!!!!!! This is what makes you being pure!!!!!!!!!! It's very important!!!!!!!!
I think that if all donations, or at least big donations (i call them "bribes"!!!) from non-real-persons and companies, were refused the TORPROJECT would benefit!!!!!! You've the example of Firefox itself, a free and open source software, corrupted by Google!!!! Where the default web search engine set in the Browser, is the one from the worst and most anti-privacy company ever!!!!!!!!!!!!!!!
https://adblockplus.org/en/ has no "DONATE" button!!!!!!! Wladimir is super very good!!! he has a website with millions of hits (people downloading the subscription lists!!!) and he never said anything about money or bills to pay, nor expensive servers!!!!!!!!! So, it's possible to being pure if you only want it for real!!!!!!!!!!
For example, you know that i very dislike the fact that even TOR is together with Google for the "summer of code projects"!!!!!! Where Tor, another open source (and also pro-privacy and anonymization) software is together with the most anti-privacy multinational company ever!!!!!!!!!!!!!!!!!! Misconception?!! Why is the "summer of code projects" important?!!!!! FOR THE MONEY!!!!!!!!!!!!!!!!!!! this is the answer!!!!!!!!!! for the corruption!!!!!!!!!!!!!!!!!!! money are the lack of passion and the lack of real love!!!!!!!! and this sounds a bit like prostitution!!!! lololol!!!!!!!!!
I also lost a bit of interest in TOR after having had so many of my super very good suggestions rejected because of somebody else jealousy!!!!!!!! and after having read so much in the blog comments here and elsewhere about TOR!!!! i think it's a open source yet a too closed project!!!!!! A group very similar to a clique at times!!!!!!!! I don't know why you and Erinn don't do anything about this!!!!!!!!!!!!!!!! i'm sure you also noticed what i'm saying!!!!!!!
The TORPROJECT should't work after what donators want!!! but after users' suggestions and what users want!!!!!!!!!!!! (YEAH!!!!!!!! if the purpose of the TOR-Project is to make a software for the users!!!!!!! isn't it?!!!!!!!!)
bye!!!!!!!!!!!!!!!!!
~bee!!!!!!!!!
hi please run my tor again
hi please run my tor again we help you from iran
با سلام از زحمات ومهارت فوق العاده شما در ایجاد این شبکه اکنون که مسئله امنییت در ایران به حالت فوقالعاده
بحرانی رسیده و هر 8 ساعت یک نفر را بدون حق دفاع کردن اعدام میکنند حداقال بما بگوئید چگونه میتوانیم دسترسی مجدد به شبکه شما را عملی کنیم با تشکر مجدد از زحمات شما
I am using Neda Ghostar Saba
I am using Neda Ghostar Saba Net. A month ago there was so much problem with the internet connection to the ISP but now its alright. I suspect this is the ISP that is experimenting with these methods. The other one is Pars Network I think which is the same.
a very interesting thing is that the ips that were shown in https://bridges.torproject.org/ were different from inside Iran and indeed the bridges website was not filtered. When I checked the bridge website using other anti filtering methods, the ips were different...
If the government of Iran
If the government of Iran can identify encrypted traffic belonging to Tor versus other encrypted traffic, that's a serious problem for Iranians using Tor. Not only can users not have access to the Tor network, but they've broadcast themselves as users of "subversive" technology -- ripe for repercussions.
My advice to Iranians is to stay far away from Tor until this issue is resolved properly. Speaking of which -- why is there no talk of all this on the or-dev mailing list? Is the fact that Tor users can be identified so casually by random governments not considered an important enough issue?
In fact, I'd advise Iranians to stay away from Tor entirely. This issue was never even on Tor's radar until Iran deployed this new firewall. Pitiful. What assurances do users have that Tor is investing in research of future and unknown attacks against its network? The traffic fingerprinting attack cash cow has been generous (hundreds of papers rehashing the same results -- we get it), but it's time to move on to less trivial research, don't you think? The Iranian government seems to think so.
We've known about this
We've known about this attack for years. In fact, there are far easier ways to identify Tor on the wire than the methods Iran is using. This shows that trying to guess which attack will be successful isn't worth the effort (same as trying to predict a black swan event). Having plans to respond to successful attacks is where the effort lies, and where our research is focused.
As for or-dev, I don't know why others didn't bring it up years ago. However, we can now discuss it in the open, see http://archives.seul.org/or/dev/Jan-2011/msg00029.html for a start. We expected many "enterprise security" companies to figure this out 5-6 years ago, however none did. Or at least, none deployed their attacks in their products. We've said repeatedly that we're trying to have an arms race as slow as possible. A fine question is whether to deploy every countermeasure possible at once to blow everyone out of the water, or wait for a successful attack and respond to just that one.
The good thing is that Tor is at first an anonymity network, second a circumvention tool. If Tor is temporarily blocked, then use a technology that isn't blocked and run Tor over it to protect your traffic from snooping by the lower technology (vpns, proxies, etc).
The anonymous network communications field as a whole is small. Please join and help further the field.
Tor is at least open and
Tor is at least open and honest about what it does, how it does it, and its failings. I don't see any other circumvention tools doing this. Sure, temporary setbacks happen. Even if China shuts off the Internet, I worry about tracking, human flesh search, and everything else. See http://donttrack.us/
See
See http://subgraph.com/NetNeutralityIran.pdf. What happens in Iran will happen in Europe. We all lose.
As you know, governments in
As you know, governments in iran, sudan,... unable to block torproject.org. i think it's because torproject.org uses ssl (security socket layer) technology to encrypt data between user and server.
So why not using this technology to bypass internet censorship?
For instance, Torproject.org creates a page with a text input, users type the web address in that input then a php script appends that url at the end of torproject.org domain, like the way google does in search result. the tor server loads that page, encrypts it using ssl and sends it to the user browser and the browser decrypts it.
What's your opinion?
It is utterly trivial to
It is utterly trivial to block torproject.org. That they don't do so is likely to be purposeful, eg, so they can monitor who then continues to access it, and what they are saying, if not specifically who said it.
Bare in mind that everything said here will be read.
یاحسین
یاحسین میرحسین
for mirhossein mousavi
TOR still not working in
TOR still not working in iran it sounds iran great firewall has beat us IT technology
Download one of these
Download one of these programs from here:
http://www.voanews.com/persian/programs/proxy/
Confirmed reports that the
Confirmed reports that the latest 0.2.2.22-alpha is working in Iran.
The 0.2.2.22-alpha shows
The 0.2.2.22-alpha shows major improvements in comparison to the previous versions. Unlike the others in which my bandwidth graph showed no data reception, I received some data using this version. The only defect is that it sticks at the "Establishing a Tor circuit" level, and the data reception is not continuous. It tends to go on and off.
OFF TOPIC. Why have you
OFF TOPIC.
Why have you disabled comments on other blog posts like new releases? Do you not care for feedback anymore?
We care, but don't have time
We care, but don't have time to sift through the 7000:1 ratio of spam to user comments. We don't have, nor want, a web forum. People who need support should email tor-assistants, not post comments from blog posts 3 years ago.
Where is the link for
Where is the link for Tor-assistants then? I don't see it mentioned anywhere from the front page. It's not mentioned in the Tor package docs either.
7000:1/3 years -- get real, phobos.
It's right here,
It's right here, https://decvnxytmk.oedi.net/about/contact.html.en. We get roughly 7000 spam comments per 1 actual comment. Making our CAPTCHA too difficult ends up driving away people, but not spam bots. So we leave an easy CAPTCHA and deal with the spam on select posts.
Spam bots and users alike post comments to any blog post they happen to find via a search engine; even if the comment is totally irrelevant to the post.
HI I HAVE DOWNLOADED TOR
HI
I HAVE DOWNLOADED TOR 0.2.2.22 FROM YOUR WEBSITE FOR SEVERAL TIMES BUT I CAN NOT INSTALL IT CORRECTLY IT DOES NOT WORK.I AM IN IRAN AND I NEED TO CONNECT TO TOR NETWORK.
PLEASE HELP US!!!!
Please contact
Please contact tor-assistants.
I have a suggestion tor
I have a suggestion
tor developer can develop a PHP proxy (ip tunneling): client version and server version.
every body can upload server version in free php host or buy php host for himselfe. they can use this proxy to connect to tor network!
it's not working :(
it's not working :(
I'll have you know Tor works
I'll have you know Tor works perfectly fine in countries where the governing regime permit it.
Tor also works in countries
Tor also works in countries where the governing regime does not permit it.
my tor did hang on handshake
my tor did hang on handshake with directory server, but then when I used tor with fechdirinfoearly, I could connect. I've been using 2.2.20 alpha.
connection from iran v
connection from iran v 0.2.1.29 connection stablishment took about an hour.it is very strange because i could not even connect with bridges for about 20 days.
is it safe?
Tor 0.2.2.22-alpha works.
Tor 0.2.2.22-alpha works.
but i can not install it in
but i can not install it in windows 7
please upgrade tor browser
please upgrade tor browser that needs not to installation
We would like to test some
We would like to test some iranian filter bypass techniques using multiple AET (Advanced Evasion Techniques) at TCP level.
We think that there are very strong way to put anti-detection system just by tweaking at Layer3 the stuff, requiring the counterpart (iranian censorship systems) to install X100 hardware to be able to detect it.
Is there any availability of a linux box IN IRAN to install our stuff and TOR (prior than 0.2.2.22-alpha) and make some tests for 1-2 days?
Pls contact privacyresearch at infosecurity.ch as we would like to experiment ability of bypass but don't have access to a linux box in iran.
Privacy Research Team (and TOR exit node maintainer)
the website
the website http://www.linuxbox.com/tiki/ is open in iran. what do you want us to do. please explain in step by step.
ultrasurf works but latest
ultrasurf works
but latest version of tor dosent work in my city in iran
Others are saying this works
Others are saying this works because the Iranian government is able to buy the records and see what you are doing. It is simply not safe to use.
Tor 0.2.2.22-alpha DOES not
Tor 0.2.2.22-alpha DOES not works. it was good for some days though!
UPdate: only windows 7 has
UPdate: only windows 7 has problem.
I just stumbled upon your
I just stumbled upon your blog after reading your blog posts wanted to say thanks.i highly appreciate the blogger for doing this effort.
today my tor browser 1.3.17
today my tor browser 1.3.17 connected successful in Iran (with IPM isp)
I've been connected via tor
I've been connected via tor 0.2.2.21 from Iran-Mashhad.(ISP: ictشرکت مخابرات ایران)
It seems that the problem is resolved.
Does TOR confirm this?
it seems the problem
it seems the problem resolved in recent days. I can connect via tor 0.2.2.21 in Iran. Does Tor confirm this?
Tor writes:@...However, it appears the Iranian Potato Wall can detect Tor or not in any case by analyzing the traffic on the wire. We have reports this is true for other circumvention tools as well.@ DOES IT MEAN THAT USING TOR IS NO LONGER SAFE IN IRAN?
We made a change on the
We made a change on the relay and bridge side that makes Tor work in Iran again:
http://archives.seul.org/or/talk/Jan-2011/msg00305.html
I don't expect this change will make things work forever, but it will buy us some more time for a better solution.
And no, one of the features of Tor's design is that while sometimes they can *block* it, that doesn't make it unsafe to use it whether they are blocking it or not.
(But remember that Tor's main security goal is to prevent somebody watching you from learning what you're doing online. There are still ways they could learn that you are using Tor -- just not what websites you're going to. This risk is present for all circumvention tools. Whether this risk is dangerous for you depends on your situation.)
Thanks a lot. Very clear.
Thanks a lot. Very clear.
From your reply (here and
From your reply (here and somewhere in this page), I get that it is just Tor 0.2.2.22 that can work now. So I must mention that I could connect via portable Tor 0.2.2.21 and installable Tor 0.2.1.28-Polipo version on linux (that never been upgrated) as well.
Thank you Tor. God bless x
Thank you Tor. God bless x OM xx
Dear assistants of tor Thank
Dear assistants of tor
Thank you for delivering tor software
I live in Iran,Tehran
I use farsi version of tor(I earn it by sending an email : tor-browser-bundle to gettor+fa @ torproject.org)
but i can't watch streams on you tube and other similr websites
so i enable plugins on Tor Usage in torbutton Options but i can't watch streams yet
I use vidalia version 0.2.10 and tor version 0.2.1.30, and i can't download and install new version of tor , may you send it to my email inbox?
By the way i want to use my own firefox or IE9,can i?
No, you can't use Adobe
No, you can't use Adobe Flash apps with the Tor Browser Bundle, https://decvnxytmk.oedi.net/torbutton/torbutton-faq.html.en#noflash.
You can use your own firefox, but beware that you may leak all of your saved cookies, cache, and other information unless you install torbutton.
iranians can buy endless
iranians can buy endless socks5 and vpn's from elitevpn or vip72 and other providers to watch youtube junk. don't bother streaming through tor
an enterprising local iranian could buy a vps, make his own proxy and sell it to other local ppl for use