Reflections from Our Stockholm All Hands

This month, the Tor Project held our biannual all hands meeting, this time in Stockholm, Sweden. During our all hands meetings, we bring together staff, key volunteers, and collaborators from partner organizations like Freedom of the Press Foundation, Tails, the Guardian Project, and Mozilla. Our goal at our all hands meetings is to reflect on the last six months, address challenges and successes, plan our work for the next six months, and have important in-person conversations that are only possible when all teams are in the same location.
For this meeting’s location and venue, we relied on one of Tor’s biggest strengths--our people.
On the first night in Stockholm, one of our local volunteers organized a ‘do it yourself’ welcome dinner for all attendees at Kafe 44, a long-standing nonprofit co-op cafe operating as a cultural social center in the heart of Stockholm.
We were also blessed with an amazing donation from KTH Royal Institute of Technology, which let us use their facilities for our three day meeting where we spread out across classrooms and engaged in back-to-back sessions organized and led by peers.
During these three days we had a local collective, Kafé Ingenstans, responsible for our lunch. They only cook vegan food with local ingredients and we had the most amazing food. We were even able to give them a big tip that we heard they will use to buy bicycles for their delivery. They also got connected with Kafe 44 after our welcome dinner and now will be serving food there.
Through partnership with our community and our community’s broader connections, we turned limited resources into a safe space to cultivate connections, collaboration, and progress toward the vision and values that we are all working towards at Tor.
We are looking forward to continuing to organize our future meetings this way. We wanted to share a taste of it, so we put together some highlights from each day for you:
Day 1 Highlights
We roadmapped for multiple teams the first day. This year, the teams were able to do an initial roadmap for projects the first day, aiming to review project plans the last day. Some of the teams held roadmapping sessions together, with the goal of building more collaboration between teams and ensuring that our work is more efficient and effective.
Day 2 Highlights
We talked about meaningful addresses for onion domains. One of the biggest usability barriers to onion services are their difficult to remember URLs. We are hoping to reduce this barrier by building a proof of concept for making these long addresses human-memorable. During this meeting, we brought together various different groups working on solutions for this problem. We watched a couple of demos of three different solutions and decided to continue with our plan to use HTTPSEverywhere to share rulesets for onion addresses.
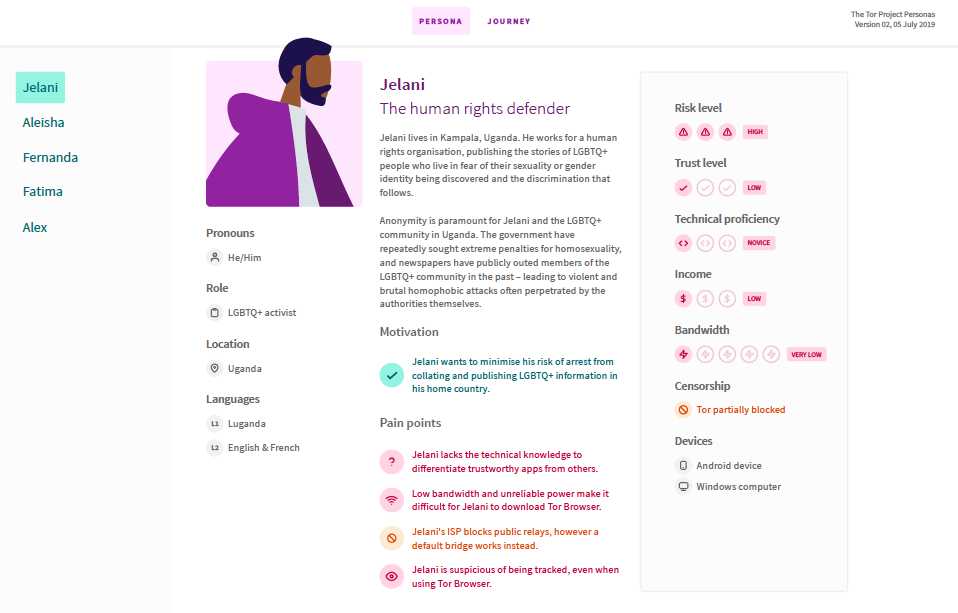
We rolled out Tor personas. As part of our travels in the Global South during 2018 and 2019, we got the chance to meet hundreds of Tor users: from activists to journalists, from highly technical users to those who only use mobile phones, all with different motivations for needing a usable private and secure tool to access the internet. The Community and UX teams have been working on collecting and mapping real user stories and finding patterns across them, and during this meeting, we shared the result--the Tor user personas--with the group.
We talked about organizational systems and processes and how to make them more efficient. With the founding of our sysadmin team, we are formalizing our efforts to improve, monitor, and maintain the internal tools and systems used by the Tor Project’s dispersed team. This important work helps all teams communicate better with one another and improves organizational security. (meeting notes)
Day 3 Highlights
We clarified our next steps in Tor network scalability. Making sure that the Tor network can handle an increase in users while improving the quality of the connection is no easy task, and it requires the hard work of multiple teams. We are working on the growth and stability of the Tor network. During this meeting we clarified the next phases in the project to scale the Tor network and started drafting how we will present this work to funders.
We discussed ways to address questions and dispel myths about the so-called dark web. Although this term is sometimes used to talk about metadata free communication online, it’s become a dangerous catchall for bad activity on the internet, and it does a huge disservice to an underappreciated technology. We talked through common misperceptions, how to address them, and how to guide the conversation towards the multitude of benefits and use cases of onion services.
We reflected on Tor’s place in the climate crisis. The climate crisis is a challenge we are all facing. It was clear we’re making an important impact in this work by making it safer to be a climate activist, training climate and environmental activists who need privacy tools to do their work, and creating a pool of open and free training resources. But we see there’s more work to do in evaluating our carbon footprint and making organizational choices to reduce it.
We roadmapped fundraising and grant activities for the next six months. After hearing from all of the teams and understanding where their work will take us in the next year, we plotted our grant and fundraising activities more strategically than ever before. Instead of creating new work or inventing new projects, thus overextending our teams, we matched our roadmap to identified opportunities and sponsors.
We closed the meeting by asking ourselves, “What are we taking away from this meeting?”
Several themes appeared: clarity, reinvigoration, gratitude, and the importance of coming together in person so we can return to our homes, ready to tackle the next six months of our roadmaps.
Comments
Please note that the comment area below has been archived.
flygskam is a reason i…
flygskam is a reason i elected not to try to attend this meeting
Instead of trying to find…
Instead of trying to find patterns for personas, why not assume the worst in all categories at once? Murphy's law. Worst cases for non-theoretical personas might be a Uyghur in Xinjiang, a Rohingya in Myanmar, a merchant in North Korea, or a journalist in Acapulco.
I am so glad you are…
I am so glad you are thinking about how Tor Project can help combat climate, because some of the most critical regions from which the people of the world need uncensored reporting also happen to be among the most dangerous regions for reporters. In Brazil, Amazonia in particular is perhaps the most importance place in the world if you are a reporter writing about what's happening on the front lines of climate change:
https://www.theguardian.com/world/2019/jul/25/amazonian-rainforest-near…
https://www.theguardian.com/world/2019/jul/26/bolsonaro-amazon-tribes-i…
The dangerous countries where many vitally important environmental degradation stories are going unreported or underreported include Iran, China, Cuba, and Russia. Too few people in "the West" who are concerned about climate change are even aware, I fear, that there are local environmental movements in all of these countries.
Wildfires pose a danger not only in California but also in Siberia:
https://www.themoscowtimes.com/2019/07/26/wildfires-engulf-siberia-spar…
Urban flooding poses a danger not only in New Orleans but also in Moscow:
https://www.themoscowtimes.com/2016/08/15/200-people-rescued-from-mosco…
Honeybees are endangered not only in the American midwest but also in Russia:
https://www.themoscowtimes.com/2019/07/26/what-killing-russia-honey-bee…
As mentioned in several of these stories, all of these phenomena appear to be linked to human-caused climate change.
The governments of CN and RU are all trying to downplay the magnitude of the danger from climate change. The governments of BR and US trying to deny that climate change is happening at all.
Just one more reason why the whole world needs Tor more than ever!
> The governments of BR and…
> The governments of BR and US trying to deny that climate change is happening at all.
theguardian.com
Brazil space institute director sacked in Amazon deforestation row
Far-right leader Jair Bolsonaro calls satellite data showing rise in deforestation ‘lies’
Dom Phillips in Rio de Janeiro
2 Aug 2019
> The director of Brazil’s National Space Research Institute (INPE) has been sacked in the midst of a controversy over its satellite data showing a rise in Amazon deforestation, which the far-right president, Jair Bolsonaro, has called “lies”. Ricardo Galvão, who had defended the institute and criticised Bolsonaro’s attack, was dismissed on Friday after a meeting with the science and technology minister, Marcos Pontes.
Interestingly enough (former US VPs, CIA torturers and NSA drone-assassins take note), DE has just declared that it has the authority to prosecute any war criminal regardless of where the crime was committed. This is a very significant step which should be very helpful in bringing the persons responsible for war crimes to justice.
It seems to me that the next step, which some governments which prosecute war crimes are seriously contemplating, is to declare that policies such as those of Bolsonaro which encourage genocide against an environment (the Amazon rain forest) must be regarded as war crimes just as much as a policy which encourages genocide against humans (the indigeneous inhabitants of the Amazon rainforest). Bolsonaro openly advocates both of these things and I hope an international arrest warrant will soon be issued naming him, Cheney, and others who must be brought to account, under the rule of law, for their homicidal actions.
> We discussed ways to…
> We discussed ways to address questions and dispel myths about the so-called dark web. Although this term is sometimes used to talk about metadata free communication online, it’s become a dangerous catchall for bad activity on the internet, and it does a huge disservice to an underappreciated technology. We talked through common misperceptions, how to address them, and how to guide the conversation towards the multitude of benefits and use cases of onion services.
I hope Tor Project is organizing to push back in the media and in the political arena against the Wraybarr Mafia, which may pose the most dangerous political threat to the continued existence of Tor Project (which is officially based in the US and subject to US law including any mandatory backdoors which the US federal congress may well enact if we do not push back hard well before a bill comes to the floor).
UK publications have long enjoyed laughing at US political antics, a harmless pastime which unfortunately just became much harder with the anointment of Boris Johnson as PM ("it would be funny if it weren't true", as on Brit put it):
theregister.co.uk
Give it a Wray, give it a Wray, give it a Wray now: Big Chris steps in to defend blowing a hole in personal crypto
Iain Thomson in San Francisco
25 Jul 2019
Unfortunately US publications hardly cover speeches by Wray and Barr at all, and never offer any explanation from Tor Project of why anyone using the term "dark web" is engaged politically motivated fear based misdirection, not factually based intelligent policy discussion. The result, I fear is that US technologists tend to dismiss the possibility that Wray and Barr might get their way. If they do, that would be the end of Us.
> I fear is that US…
> I fear is that US technologists tend to dismiss the possibility that Wray and Barr might get their way. If they do, that would be the end of Us.
But not all US technologists dismiss Wraybarr fear-mongering as so too technologically counterfactual that anyone might take it seriously:
Here is an editorial warning that the Drump administration is serious about requiring backdoors in all software products which use encryption:
eff.org
DOJ and FBI Show No Signs of Correcting Past Untruths in Their New Attacks on Encryption
Andrew Crocker
31 Jul2019
And here is a series of tweets from a leading American cyptographer, Matt Green:
https://mobile.twitter.com/matthew_d_green/status/1153684919434055680
Green points out that Barr's speech mentions three proposals for mandatory backdoors: from the "lovely people!" at GCHQ, a harebrained non-coherent "proposal" from Ray Ozzie, and an old paper from Matt Tait which led nowwere. He reminds us of the Jupiter Netscreen fiasco, in which a "legal access" backdoor was hijacked by unknown actors who used it to spy on... wait for it... US corporations and agencies. He reminds us that fiascos such as the OPM breach (I would add the recent breach of facial id images of US citizens from a CBP contractor) show that the USG is unable to protect sensitive information.
> How do US government agencies protect themselves? Using custom encryption developed by the NSA? No. They use COTS products they buy from corporations
Oh, it's much much worse than that. Some of the most sensitive information is transmitted between doctors and low income patients or lawyers and low-income clients and their USG funders by unencrypted fax machine. Or in unencrypted phone calls. USG is so anxious to make it supereasy for their own warrantless access to the lives of American citizens that they are practically begging foreign actors to spy on us. And those foreign actors have proven happy to take advantage of the opportunity offered by insanely self-destructive policies, of which the Wraybarr hysteria is only the latest example.
> There is no safe backdoor solution on the table. Barr and the Trump administration have nothing new to offer here except for a creatively terrifying interpretation of the 4th amendment and a desire to minimize risks. But what they do have is time, and the inevitability that given enough of it, something terrible will happen to America on their watch. And they’ll be able to push these proposals without the need for debate. That’s where we are, and it should scare you.
I hope Tor Project is paying attention to all this.
Many fine quotes from…
Many fine quotes from cryptographers and technologists who, not surprisingly, uniformly decry the Wraybarr anti-encryption hysteria:
arstechnica.com
Barr says the US needs encryption backdoors to prevent “going dark.” Um, what?
"The FBI says they're 'going dark.' Well yeah, because they've been staring at the sun."
Sean Gallagher
4 Aug 2019
The quote which might surprise some is from Gen. Michael Hayden, former DIRNSA, who has also rather bluntly stated that encryption per se is not a problem, given the vast opportunities for spooks and LEAs to freely access information in other ways.
Speaking of partner…
Speaking of partner organizations and network scalability, have a look at Battlemesh, Freifunk, Guifi.net, and other non-commercial open community wireless mesh networks.
I have no knowledge of those…
I have no knowledge of those specific projects, but also hope TP will brainstorm how future Tor products might evade internet crackdowns by providing tools based upon
o WiFi mesh for local communication in cities
o micro-satellite swarms
o other wireless communications schemes
It would also be useful to encourage entrepreneurs interested in offering to the general public such useful consumer electronic-self-defense devices as wide-band RF scanners and spectrum analyzers, RFID readers, card readers, to help citizens check up on what their "own" [sic] consumer electronic devices are doing. (In a free market, entrepreneurs have surely noticed that the Cambridge Analytica scandal has created a demand for ordinary citizens who want to protect themselves and their families against dragnet surveillance--- by Facebook, NSA, whomever--- and psyops--- by CIA, IRS, whomever?)
Example: suppose that alert consumers in Our City have noticed Ugly Telco putting covert putative "open access points" in every home WiFi router they foist upon their mostly unknowing customers, covert devices which do not function as open APs at all but as devices which map and track in real time every WiFi capable device which can be tricked into connecting to the alleged APs. This discovery would naturally prompt questions such as this: if there is an RFID tag in our clothing, does Ugly Telco (or another actor) appear to be using that to covertly track everyone in Our City (including people who avoid doing business with Ugly Telco)?
Example: suppose that alert mass transit riders have noticed audio surveillance of mass transit riders, in addition to those ubiquitous surveillance cameras? Video of rapt riders gazing into their smart phones might not seem very intrusive to those addicted to social media. But do we really want the transit company knowing not only that we are talking to another rider--- which someone could in principle notice on a video feed--- but even what we are talking about? Which prompts questions such as this: is Bluetooth being abused by mass transit operators in Our City to covertly track individual riders in real time? (Note that we know that precisely this was done in Barcelona almost a decade ago; we've heard nothing since, but does that really mean that Our City decided not to engage in a covert and potentially highly lucrative dragnet surveillance of transit riders, under cover of a secret counter-terror program? After all, there is no law against their selling the data not only to interested governments but also to companies such as Google or Amazon, so... it's legal, it's very profitable, no investigative reporter is looking for it... so they'll probably do it, yes?)
One question developers of counter-surveillance technology should bear in mind: how could this thing be abused? Because just like current Tor is sometimes abused, bad actors--- likely including both corporate and state sponsored bad actors--- will want to abuse anything abusable, in order to spy even more intrusively on even more ordinary lives.
Example: the above mentioned Ugly Telco network of fake open APs functioning as dragnet tracking and surveillance is essentially a WiFi net owned and operated by one of Our Enemies. We need a WiFi mesh owned and operated by The People for The People... but we somehow need to keep out the bad guys. This is the kind of issue we need to address before even beginning to look for funding or putting together a development team to design the mesh.
I want to donate not just a…
I want to donate not just a little, but I need to been anonymously through.
I definitely tell you guys. My money is legally to earn and lifetime harvest through an opportunity
and want help human justice and rights.You guys system not allow secure on donator . Please let me know
how to contact you in person?
Thanks so much for your…
Thanks so much for your support! You can email me directly at giving at torproject.org.
When you say you want to…
When you say you want to contribute a large sum "anonymously", do you mean that you do not wish your identity to be known to TP (that might be possible) or that you do not wish your name to be known to anyone but your confidantes (which probably would not be possible)?
It seems to be very difficult to donate pan-anonymously to human rights NGOs; governments have thrown up too many legal and technical obstacles even while looking the other way as their wealthiest citizens rather openly engage in rampant tax-evasion, money-laundering, influence-peddling, and myriad other forms of public corruption. In practice wealthy people/families can and often do act anonymously with complete impunity from any government, but ordinary citizens cannot act anonymously without running the risk of severe retaliation from their own or another government.
There are proposals for cryptocurrencies which would be more anonymous than Bitcoin (which is not anonymous to "the authorities", for technical reasons), but for now standard money laundering evasions (multiple offshore front companies, etc) would appear to be your best bet for anonymous transfers of funds. (This somewhat cynical suggestion--- which most probably will never result in a significant increase in TP's meager budget--- might at least have the beneficial side effect of possibly causing some USG politicians to decide they are so terrified by the prospect of large anonymous donations to TP that they would be willing to risk calling for a serious crackdown on money-laundering and tax-evasion by the American oligarchs.)
But in any case I am not sure NGOs subject to US law can even legally accept large anonymous donations, or whether this might be inadvisable even if technically legal in some circumstances. TP needs a GC, methinks. Who might want to know: what is the source of the money? Can TP prove upon demand (from USG) that it does not represent criminal proceeds? Because our political enemies will be happy to pretend to believe that all large donations to a human rights NGO come from ill-gotten gains. This has long been a common tactic in Russia, for example, and as everyone knows, more and more politicians in the US (which has legal authority over TP because TP is based in the US) are increasingly adopting the RU model of political corruption.
(By rights, FBI Director Wray should of course be loudly demanding legal authorities and funding to enable the FBI to crack down on tax evasion, offshoring, and money-laundering by the US upper class, instead of screaming for new legal authorities and funding to crack down on corruption-exposing journalists such as Glenn Greenwald and human rights NGOs like Tor. But of course, just as late Director Hoover insisted for decades that the American Mafia did not even exist, Director Wray is pretending that journalism and human rights activism somehow represent a far greater threat to democracy [sic] than offshoring, tax evasion and money laundering, by wealthy Americans and corrupt campaign financing. Which appears to me to represent extremist hypocrisy, but FBI has never come close to shucking off the loathsome Hoover's vision of FBI's core mission--- cracking down on political dissent--- which means FBI remains an authoritarian extremist organization which is not, unfortunately, yet illegal under US law. Although the Drumpists appear to be preparing to challenge FBI's legal right to existence. Now wouldn't that be a kick?)
If your money does not come from some clearly illegal source--- you said it doesn't, and I believe you, but you must acknowledge that "the authorities" will demand proof that the money comes from legal activity--- I would encourage you to think about forming a foundation in manner consistent with US law (talk to a good lawyer) and to donate to NGOs like TP through your foundation. That won't be anonymous and you'll become pestered by other groups seeking large donations, but you'll feel just as good about helping those who are defending the ordinary citizens who would otherwise be defenseless against predatory corporations seeking ownership of their lives, and against genocidal governments plotting to extinguish entire communities.
So what about stealth mode…
So what about stealth mode for smartphones?
How does Tor Project differ…
How does Tor Project differ from Startpage.com for security and anonymity?
Startpage.com is a search…
Startpage.com is a search engine. Tor Project develops software based on onion routing. The services each of them provides are in totally different genres. Compare Startpage.com to DuckDuckGo rather than Tor Project. Compare Tor Project to I2P or IPFS rather than Startpage.com.
Suggestion for a possible…
Suggestion for a possible topic for a future meetup: how can Tor Project do more to assist endangered journalists covering such as the activities of the Mexixan drug cartels?
truth-out.org
The War on Drugs in Mexico Is Also a War on Journalists
Susie Day, Truthout
27 Jul 2019
> What is press freedom and how do we know what it looks like? While we in the United States are absorbed in Julian Assange-related quandaries about just who is a journalist, and whether leaked information can or should compromise national security, reporters in Mexico are harassed and killed daily for covering a “drug war” launched in 2006 by President Felipe Calderón, but abetted by the U.S. government.
>
> Marcela Turati is one of those reporters. She is an internationally respected investigative journalist, who, for over a decade, has covered the poverty and violence wreaked by this ongoing conflict, which has disappeared or killed tens of thousands. She has seen colleagues and friends murdered by drug cartels or police or government forces — it is difficult to know, in this devastating chaos, just where danger lies. She herself lives in danger. On May 21, I spoke to Turati in New York City, at Hunter College, where she had come to address a symposium entitled “Crisis for Mexican Journalists.” In this interview, Turati discusses how the drug war fueled attacks on journalists in Mexico, the role of the U.S., and how journalists are responding to threats on their lives.
>...
> Q: What would you ask of people in the U.S.?
> A: Once, I had to speak in front of some American journalists. They asked me that. I told them, “Don’t abandon us.”
A message which I have taken to heart.
Can't tools like Onionshare be exploited with other tools to help highly anonymized blogs report on the violence? The threats are much like those encountered in war zones such as Syria because parts of the government are heavily infiltrated by the drug cartels. So anyone who wants to speak truth to the drug cartels's power is up against the full panoply of Cellebrite, Hacking Team, NSO, Gamma International type spyware, law enforcement powers (ironical because drug running is illegal in Mexico), militarized police raids, corrupt politicians with an ax to grind, amoral multinational corporations eager to buy protection from the cartels by proving information, etc.