New Release: Tor Browser 15.0

Tor Browser 15.0 is now available from the Tor Browser download page and distribution directory. This is our first stable release based on Firefox ESR 140, incorporating a year's worth of changes that have been shipped upstream in Firefox. As part of this process, we've also completed our annual ESR transition audit, where we reviewed and addressed around 200 Bugzilla issues for changes in Firefox that may negatively affect the privacy and security of Tor Browser users. Our final reports from this audit are now available in the tor-browser-spec repository on our GitLab instance.
The ongoing development of Tor Browser is made possible thanks to the support of our community. If Tor Browser is important to you, now is a great time to support our mission to FREE THE INTERNET, as all donations will be matched by Power Up Privacy through December 31, 2025.
What's new?
Desktop
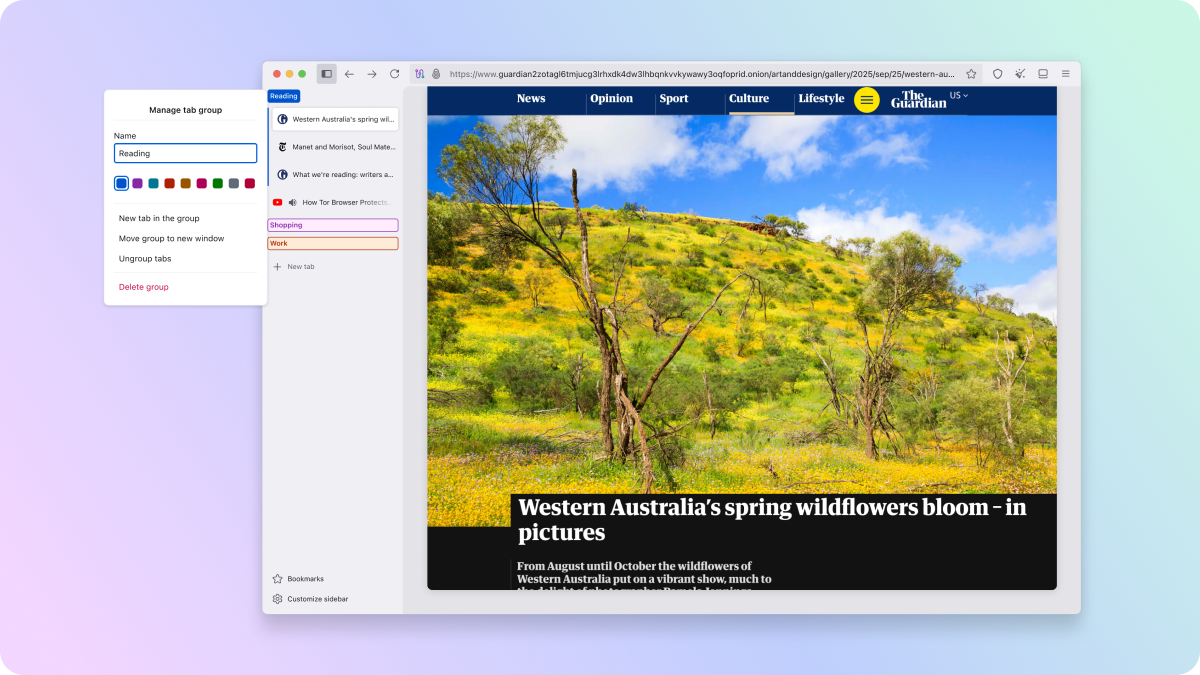
Tor Browser 15.0 inherits a multitude of useful new features and usability improvements from Firefox that have passed our audit. For desktop, these include vertical tabs: providing a more manageable, alternative layout with open and pinned tabs stacked in a sidebar rather than across the top of the window. For ease of access, Bookmarks can be retrieved directly from the sidebar when expanded too. However, regardless of whether you prefer horizontal or vertical tabs, everyone benefits from the addition of tab groups: helping you keep on top of the clutter by organizing tabs into collapsible groups that can be given names and color-coded. Tor Browser 15.0 also inherits elements of Firefox's recent address bar refresh, including a new unified search button that allows you to switch search engines on the fly, search bookmarks or tabs, and reference quick actions from the same menu.
Note that Tor Browser tabs are still private tabs, and will clear when you close the browser. This enforces a kind of natural tidiness in Tor Browser since each new session starts fresh – however for privacy-conscious power users, project managers, researchers, or anyone else who accumulates tabs frighteningly quickly, we hope these organizational improvements will give you a much needed productivity boost.
Android
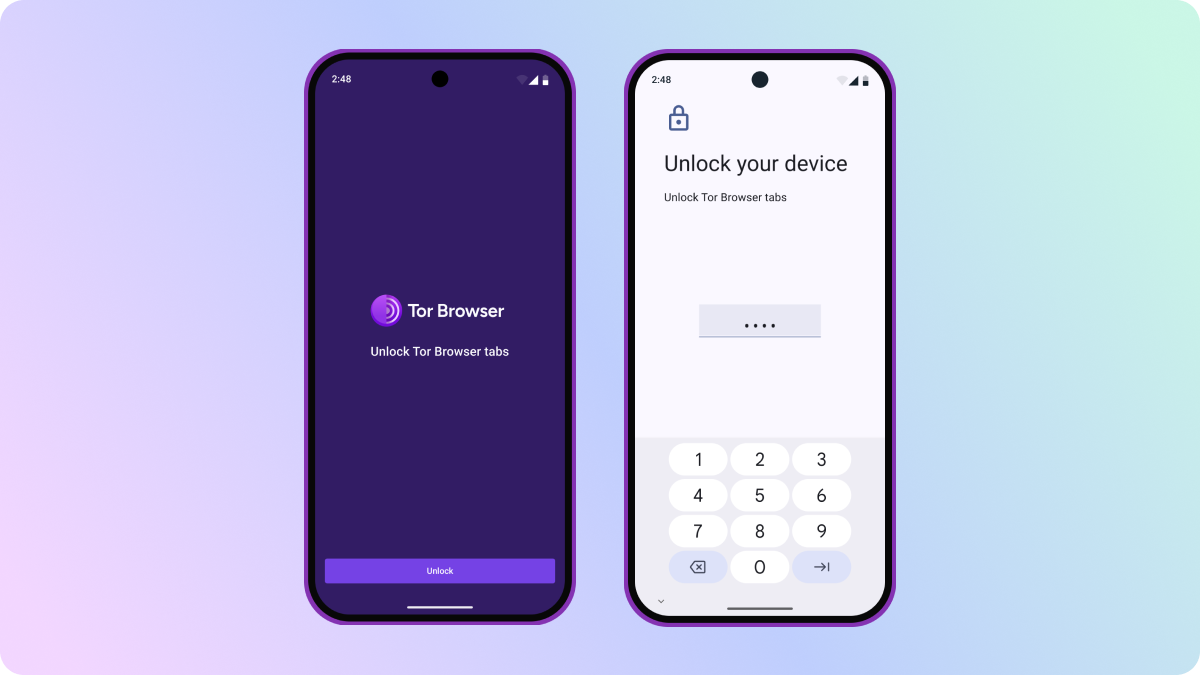
On Android, screen lock adds an extra layer of security to your browsing sessions. After enabling screen lock in Settings > Tabs, your tabs will lock automatically when you switch away from the browser without closing it. Upon returning to the app, you'll be prompted to unlock your tabs using your fingerprint, face, or pass code, depending on which option your device is configured to use.
Like Tor Browser for Desktop, your browsing session will still be cleared when Tor Browser is closed. However, this feature provides peace of mind in a specific scenario: by ensuring that your browsing remains private even if someone has gained temporary access to your unlocked phone with Tor Browser open in the background – whether you've handed it to a friend, or left your device sitting on a table.
What's changing?
Updates to Android and Linux device compatibility
At present, Firefox 140 and Tor Browser 15.0 support Android 5.0 or later, which was released almost 11 years ago. While Mozilla's commitment to support such an old version of Android is admirable, it introduces several technical and security challenges for developers. As a consequence, Firefox have announced their intention to increase the minimum support requirements to Android 8.0, and have also decided to drop support for x86 CPUs for Android and Linux. Sadly, it's not possible for the Tor Project to maintain support for these platforms on our own without official support from Mozilla.
While these changes won't impact Tor Browser users immediately, we expect them to take effect with the release of Tor Browser 16.0 mid-next year. This means that Tor Browser 15.0 will be the last major release to support x86 for Linux and Android, in addition to Android 5.0, 6.0, and 7.0. However, we will continue to release minor updates with security fixes for these platforms until Tor Browser 16.0's eventual release.
Although nobody wants to see support for their platform get dropped, it's an important step to maintain the stability and security of both Firefox and Tor Browser over time, and will allow developers to utilize newer technologies in both browsers. In addition, supporting x86 for Android has been particularly challenging for our developers due to the 100MB package size limit imposed by Google Play. While we have deployed several workarounds to stay within this limit in the recent past, these often come at a cost – such as x86 Android users missing out on the Conjure pluggable transport, for example.
Disabling of WebAssembly now managed by NoScript
WebAssembly (or Wasm) is a web technology that helps websites and web apps run faster. It allows web developers to write programs in languages like C, C++ or Rust, and compiles these into a special format that web browsers can run more efficiently.
As has been suggested in this meta-analysis from 2024, further investigation of Wasm's potential exploits is necessary – therefore Wasm is currently disabled in the Safer and Safest security levels in order to reduce Tor Browser's attack surface. Up until now, this was achieved by setting the global preference javascript.options.wasm to false – however this approach was no longer viable after Mozilla implemented part of their PDF reader in Wasm between versions 128 and 140. Consequently, we have decided to move control of Wasm to NoScript, which is bundled with Tor Browser, and already manages JavaScript and other security features. This means that Wasm now works on privileged browser pages such as the PDF renderer, but NoScript will continue blocking the technology on regular websites at the Safer and Safest security levels.
Users who have manually set javascript.options.wasm to "false" while in the Standard security level will see their security level represented as "Custom" instead. To mitigate any issues that may arise with the browser's PDF reader, we encourage those users to switch the preference back to "true", thereby passing management of Wasm over to NoScript. Furthermore, manually disabling Wasm at the Standard security level (either via NoScript or javascript.options/wasm) may also make your fingerprint more unique by deviating from Tor Browser's default configuration. To avoid this scenario, we recommend sticking with one of the pre-defined security levels and caution users against making further changes to individual preferences in about:config.
Alternatively, should you wish to keep Wasm disabled in future, we invite you to increase your security level to Safer or Safest going forward. Note that both Safer and Safest users may notice javascript.options.wasm switch to "true" automatically as management of Wasm is passed over to and blocked by NoScript, meaning that you are still protected regardless. In addition, Safest users in particular are not vulnerable to any potential vulnerabilities introduced by Wasm since the format requires JavaScript to work.
Known issues
Tor Browser 15.0 comes with a number of known issues that can be found in Tor Browser's issue tracker. In particular, we would like to highlight the following:
Desktop
The initial release of vertical tabs in Tor Browser includes a couple of quirks:
- When the sidebar is visible (such as when vertical tabs are enabled), the window may visibly resize when Tor Browser is launched.
- Due to variations in window size, Letterboxing may be visible. You still get the anti-fingerprinting protections provided by Letterboxing, but the default window size will be different than intended.
We are currently working to issue a fix for both of these bugs. Please see tor-browser#44096 for details.
Android
- Web pages may not load after updating Tor Browser on older versions of Android. This can be fixed by clearing your app cache manually in
Settings > Apps > Tor Browser > Storage & cache.
Get involved
If you find a bug or have a suggestion for how we could improve this release, we'd love to hear your feedback. If you would like to contribute to a future release, please see our guide for new contributors to get started.
Full changelog
The full changelog since Tor Browser 14.5.9 is:
- All Platforms
- Updated NoScript to 13.2.2
- Updated Lyrebird to 0.6.2
- Bug tor-browser#19741: Opensearch (contextual search) does not obey FPI
- Bug tor-browser#43009: Backport Bug 1973265 - Put WebCodecs API behind RFP Target
- Bug tor-browser#43093: Refactor the patch to disable LaterRun
- Bug tor-browser#43727: Update moz-toggle customisation for ESR 140
- Bug tor-browser#43745: Disable HEVC (H265) playback support
- Bug tor-browser#43772: Do not use official branding for BB/TB/MB
- Bug tor-browser#43784: Get confirmation from NoScript that settings are applied
- Bug tor-browser#43832: Drop eslint-env
- Bug tor-browser#43850: Modify the Contrast Control settings for RFP
- Bug tor-browser#43853: DomainFrontedRequests: setData is no longer a function
- Bug tor-browser#43864: Remove features from the unified search button
- Bug tor-browser#43869: Hide pens with RFP
- Bug tor-browser#43880: Update moat's domain front url
- Bug tor-browser#44045: Drop AI and machine learning components
- Bug tor-browser#44068: Handle migration from meek-azure to meek built-in bridge type
- Bug tor-browser#44069: Update
meek-azurerelated strings tomeek - Bug tor-browser#44140: Refactored patch to prevent writing temp PDF files to disk
- Bug tor-browser#44234: No images in PDF
- Bug tor-browser#44275: Reduce console noise on security level guess
- Bug tor-browser#44280: Test stream isolation
- Bug tor-browser-build#41429: Add a note about user safety to Tor Browser Alpha blog posts
- Bug tor-browser-build#41442: Update our audit CSVs to use the new Audit template
- Bug tor-browser-build#41502: Application services build is failing on isNetworkAllowed()
- Bug tor-browser-build#41609: Use new CDN77 fronts for snowflake
- Windows + macOS + Linux
- Updated Firefox to 140.4.0esr
- Bug tor-browser#42025: Purple elements (e.g. Tor buttons) need dark theme variants
- Bug tor-browser#42738: Tidy up the commit structure for browser updates UI
- Bug tor-browser#43111: Delete our webextensions for search engines when Bug 1885953 is fixed upstream
- Bug tor-browser#43519: Replace tor-loading.png with SVG
- Bug tor-browser#43525: Check if our search engine customization still works after ESR 140 transition
- Bug tor-browser#43590: Move letterboxing rules out of browser/base/content/browser.css
- Bug tor-browser#43610: Use newer CSS variable names for ESR 140
- Bug tor-browser#43629: All migrations in migrateUIBB are run for new profiles
- Bug tor-browser#43636: Tor exiting during startup with "connect automatically" leads to "Try a bridge" page
- Bug tor-browser#43638: Fix up our
<command>elements - Bug tor-browser#43664: Review Mozilla 1842832: Move the private browsing toggle to initial install dialog
- Bug tor-browser#43728: Update search engine icon sizes
- Bug tor-browser#43765: Temporarily disable Lox
- Bug tor-browser#43766: Only save the relevant TorSettings changes to preferences.
- Bug tor-browser#43770: Bugzilla 1958070: More BrowserGlue simplification/splitting
- Bug tor-browser#43776: Set branding files for l10n merging
- Bug tor-browser#43795: Restore the URL classifier XPCOM components.
- Bug tor-browser#43817: Write e2e test for verifying if the browser is connected to the Tor network
- Bug tor-browser#43844: Security level shield icon should be flipped for RTL locales
- Bug tor-browser#43874: Incorporate our unified extension button hiding logic into mozilla's changes for ESR 140
- Bug tor-browser#43879: tor-branding.css declarations are overwritten
- Bug tor-browser#43886: Fix new tab for ESR 140
- Bug tor-browser#43900: Open newtab rather than firefoxview when unloading the last tab
- Bug tor-browser#43901: Modify about:license for Tor Browser and drop about:rights
- Bug tor-browser#43902: Hide Sidebar buttons
- Bug tor-browser#43903: Report broken site is disabled rather than hidden
- Bug tor-browser#43905: base-browser.ftl missing from about:addons
- Bug tor-browser#43906: Extension.sys.mjs change in the wrong commit
- Bug tor-browser#43913: Context menu not properly populated
- Bug tor-browser#43929: two about:tor pages opened after update
- Bug tor-browser#43930: Onionize toggle not centre aligned in about:tor
- Bug tor-browser#43947: Console error from ContentBlockingPrefs.init
- Bug tor-browser#43966: Notify the user when they are in a custom security level (desktop)
- Bug tor-browser#43989: Switch off AI chatbot preference
- Bug tor-browser#44030: Security Level selector does not get confirmation before restarting
- Bug tor-browser#44034: Update string used for checkbox on New Identity confirmation dialog
- Bug tor-browser#44040: Modify nsIPrompt and the commonDialog code to allow destructive buttons
- Bug tor-browser#44090: Several of our XUL pages cause a crash because of missing CSP
- Bug tor-browser#44095: Rename connectionPane.xhtml and remove it from the jar
- Bug tor-browser#44101: Toolbar connection status is not visible when using vertical tabs
- Bug tor-browser#44106: Make sure background tasks are not used for shutdown cleanup
- Bug tor-browser#44107: Switch tab search action is missing an icon
- Bug tor-browser#44108: Fix the new history sidebar
- Bug tor-browser#44115: Make remove all bridges dialog use a destructive red button
- Bug tor-browser#44123: Do not trim protocol off of URLs ever
- Bug tor-browser#44125: Do not offer to save signatures by default in Private Browsing Mode
- Bug tor-browser#44141: Hide "Report broken site" items by default
- Bug tor-browser#44142: Missing document_pdf.svg from our branding directories
- Bug tor-browser#44145: Switch onion connection icons to use --icon-color-critical and --icon-color
- Bug tor-browser#44153: Test search engine customization
- Bug tor-browser#44159: Change or hide the sidebar settings description
- Bug tor-browser#44177: Remove more urlbar actions
- Bug tor-browser#44178: Search preservation does not work with duckduckgo in safest security level
- Bug tor-browser#44180: Clear YEC 2024 preference
- Bug tor-browser#44184: Duckduckgo Onion Lite search does not work properly in safest when added as a search engine
- Bug tor-browser#44187: TLS session tickets leak Private Browsing mode
- Bug tor-browser#44192: Hovering unloaded tab causes console error
- Bug tor-browser#44213: Reduce linkability concerns of the "Search with" contextual search action
- Bug tor-browser#44214: Update letterboxing to reflect changes in ESR 140
- Bug tor-browser#44215: Hide Firefox home settings in about:preferences
- Bug tor-browser#44221: Backport MozBug 1984333 Bump Spoofed Processor Count
- Bug tor-browser#44239: DDG HTML page and search results displayed incorrectly with Safest security setting
- Bug tor-browser#44262: Disable adding search engines from HTML forms
- Bug tor-browser#44270: Match Firefox's TLS fingerprint
- Bug tor-browser#44279: Disable contextual search install prompt
- Windows + Android
- Bug tor-browser#44062: Force touch enabled on Windows and Android
- Windows
- Bug tor-browser#44046: Replace BASE_BROWSER_UPDATE with BASE_BROWSER_VERSION in the font visibility list
- macOS
- Bug tor-browser#44127: Do not show macOS Privacy hint on network error pages
- Linux
- Bug tor-browser#43950: Review Mozilla 1894818: Support HEVC playback on Linux
- Bug tor-browser#43959: Make Noto Color Emoji the default emoji font on Linux
- Bug tor-browser#44227: Some CJK characters cannot be rendered by Tor which uses the Noto font family
- Bug tor-browser#44286: Hardcode GTK system font
- Bug tor-browser-build#41586: Replace Noto CJK with Jigmo on Linux
- Android
- Updated GeckoView to 140.4.0esr
- Bug tor-browser#43179: Make persistent 'private tabs' notification distinct from Firefox's
- Bug tor-browser#43401: Replace the constructor of Locale with a builder
- Bug tor-browser#43577: Flush settings fails on Android
- Bug tor-browser#43643: Clean out unused tor connect strings
- Bug tor-browser#43650: Survey banner behaves like a dialog on Android, rather than a card
- Bug tor-browser#43676: Preemptively disable unified trust panel by default so we are tracking for next ESR
- Bug tor-browser#43699: Dummy "about:" pages are not cleared from recently closed tabs (and possibly elsewhere) because they are normal tabs, not private tabs.
- Bug tor-browser#43755: Restore functionality of "switch to tab" urlbar suggestion
- Bug tor-browser#43757: Disable setting for trending search
- Bug tor-browser#43826: Review Mozilla 1960122: Use
MOZ_BUILD_DATEin Fenix build configuration - Bug tor-browser#43855: brand.properties merging on Android is broken in 140
- Bug tor-browser#43943: Review Mozilla 1928705: Ship Android Font Restrictions as part of FPP
- Bug tor-browser#44021: Android settings page colors are sometimes messed up (seems to be on the first launch)
- Bug tor-browser#44029: Search/url bar doesn't work on android after ESR 140
- Bug tor-browser#44036: Crash on opening "Search Settings" on android
- Bug tor-browser#44042: Debug crash when opening settings too quickly after launching app
- Bug tor-browser#44047: Tor Browser's home doesn't have the background at the first load on Android
- Bug tor-browser#44080: Further remove "Analytics data collection and usage"
- Bug tor-browser#44083: "snowflake" is lower case on Android
- Bug tor-browser#44098: Bookmarks offer a way to go to sync in 15.0a1
- Bug tor-browser#44133: Hide the "Allow in private browsing" checkboxes from WebExtension management UI
- Bug tor-browser#44139: Restore the (inactive) YouTube and Reddit search plugins on Android
- Bug tor-browser#44172: Fix crash in TorAndroidIntegration.handleMessage()
- Bug tor-browser#44196: Persistent notification sometimes does not clear
- Bug tor-browser#44237: Revoke access to all advertising ids available in Android
- Bug tor-browser#44293: Force immediate NoScript update checks after bootstrap
- Bug tor-browser-build#41494: Update GeckoView build scripts for ESR140
- Build System
- All Platforms
- Bug tor-browser#43615: Add Gitlab Issue and Merge request templates
- Bug tor-browser#43616: Customize Gitlab Issue and Merge templates
- Bug tor-browser#43891: Update the translation CI to use the new mozilla versions
- Bug tor-browser#43954: Update tb-dev to handle lightweight tags
- Bug tor-browser#43962: update tb-dev auto-fixup for git 2.50
- Bug tor-browser#44061: "Contributing" link is broken
- Bug tor-browser#44067: Move --enable-geckodriver only to Linux-only mozconfigs
- Bug tor-browser#44103: git's export-subst is a reproducibility problem
- Bug tor-browser#44104: Don't run linter when there are no overall changes
- Bug tor-browser-build#26408: Make MAR signature checks clearer when creating incremental MAR files
- Bug tor-browser-build#34434: Remove unused variables from rbm.conf
- Bug tor-browser-build#40551: Drop go reproducibility patches
- Bug tor-browser-build#40697: Delete repackage_browser.sh
- Bug tor-browser-build#40698: Update locale in tbb_version.json
- Bug tor-browser-build#41064: Update tools/signing/README and add a tools/signing/machines-setup/README
- Bug tor-browser-build#41227: Update projects/common/list_toolchain_updates-common-firefox-geckoview to include check for binutils
- Bug tor-browser-build#41434: Go updates shouldn't target all platforms until macOS is on legacy in the changelogs
- Bug tor-browser-build#41444: Build artifacts to support artifact builds of Tor/Muillvad/Base Browser
- Bug tor-browser-build#41448: Update toolchains for Firefox ESR 140
- Bug tor-browser-build#41459: Update taskcluster/ci paths in README and comments
- Bug tor-browser-build#41465: Disable development artifacts generation by default, keep it enabled for nightly builds
- Bug tor-browser-build#41474: update README to explain moat-settings project requires
jqto be installed - Bug tor-browser-build#41478: Add vim and others missing basic tools to base container image
- Bug tor-browser-build#41486: Track bundletool and osslicenses-plugin versions in list_toolchain_updates_checks
- Bug tor-browser-build#41496: Clean up unused projects
- Bug tor-browser-build#41501: cargo_vendor generated archive maintains timestamps
- Bug tor-browser-build#41514: Remove var/build_go_lib from projects/go/config
- Bug tor-browser-build#41532: Rename meek-azure to meek in pt_config.json
- Bug tor-browser-build#41534: Copy geckodriver only for Linux x86-64
- Bug tor-browser-build#41537: Add script to count mar downloads from web logs
- Bug tor-browser-build#41539: Update Ubuntu version used to run mmdebstrap to 24.04.3
- Bug tor-browser-build#41568: Update instructions for manually building 7zip
- Bug tor-browser-build#41576: Build expert bundles outside containers
- Bug tor-browser-build#41579: Add zip to the list of Tor Browser Build dependencies
- Bug tor-browser-build#41594: Remove version from tor-expert-bundle and tor-expert-bundle-aar filenames
- Bug tor-browser-build#41600: update lyrebird version to v0.6.2
- Bug tor-browser-build#41602: Update tools/changelog-format-blog-post
- Bug rbm#40084: Always use bash for the debug terminal
- Bug rbm#40087: Downloaded files getting stricter permissions than expected
- Windows + macOS + Linux
- Bug tor-browser#44131: Generate torrc-defaults and put it in objdir post-build
- Bug tor-browser-build#41373: Remove
_ALLfrom mar filenames - Bug tor-browser-build#41457: Set mar IDs as env variables in tor-browser-build
- Bug tor-browser-build#41604: Keep update-responses files from previous release
- Windows + Linux + Android
- Updated Go to 1.24.9
- Windows
- Bug tor-browser#44167: Move the nsis-uninstall.patch to tor-browser repository
- macOS
- Bug tor-browser-build#41503: Error 403 when downloading macOS SDK
- Bug tor-browser-build#41527: Update libdmg-hfsplus and enable LZMA compression on dmgs
- Bug tor-browser-build#41538: Bump macOS SDK to 15.5
- Bug tor-browser-build#41571: Work-around to prevent older 7z versions to break rcodesign.
- Linux
- Bug tor-browser-build#41458: Ship geckodriver only on Linux
- Bug tor-browser-build#41488: Disable sys/random.h for Node.js
- Bug tor-browser-build#41558: Share descriptions between Linux packages and archives
- Bug tor-browser-build#41561: Ship Noto Color Emoji on Linux
- Bug tor-browser-build#41569: Use var/display_name in .desktop files
- Android
- Bug tor-browser#43984: Update android build scripts and docs for ESR 140
- Bug tor-browser#43987: 140 Android is not reproducible
- Bug tor-browser#44078: Modify ./autopublish-settings.gradle for building a-s and glean with uniffi-bindgen no-op
- Bug tor-browser#44220: Disable the JS minifier as it produces invalid JS
- Bug tor-browser-build#41453: Update application-services and uniffi-rs for ESR140
- Bug tor-browser-build#41467: Remove list_toolchain_updates-firefox-android from Makefile
- Bug tor-browser-build#41483: geckoview_example-withGeckoBinaries-....apk doesn't exist anymore in Firefox 140
- Bug tor-browser-build#41484: Create a fork of application-services
- Bug tor-browser-build#41500: Optimize tor and its dependencies for size on Android
- Bug tor-browser-build#41506: Use appilcation-services branch for nightlies builds
- Bug tor-browser-build#41507: Single-arch build fails because artifacts don't have arch subdirectories
- Bug tor-browser-build#41523: Use custom built Glean package on Android
- Bug tor-browser-build#41548: Hide tor's symbols on Android and add other linker options to save space
- Bug tor-browser-build#41577: Minify JS with UglifyJS on Android x86
- Bug tor-browser-build#41583: Align tor and PTs to 16kB on Android
- Bug tor-browser-build#41605: Ignore incrementals if we're not building desktop
- All Platforms

Comments
We encourage respectful, on-topic comments. Comments that violate our Code of Conduct will be deleted. Off-topic comments may be deleted at the discretion of the moderators. Please do not comment as a way to receive support or to report bugs on a post unrelated to a release. If you are looking for support, please see our FAQ, user support forum or ways to get in touch with us.