New Release: Tor Browser 13.5

Tor Browser 13.5 is now available from the Tor Browser download page and our distribution directory.
Regular readers of our release posts will know that for the past two years we've been gradually increasing our capacity to not only maintain, but bring tangible improvements to Tor Browser for Android. In that respect, Tor Browser 13.5 feels like a milestone: in addition to the dozens of bug fixes and minor improvements noted in the changelog below, this release features major changes to Android's connection experience in preparation for the future addition of Connection Assist, including full access to Settings before connecting and a new, permanent home for Tor logs.
For desktop, we're continuing our efforts to improve the user experience of Tor Browser's fingerprinting protections. Following the changes we introduced to new window sizes in Tor Browser 13.0 for Desktop, this release features welcome design changes to letterboxing, including new options to remember your last used window size and adjust the alignment of the letterbox in General Settings. Bridge users will also discover a myriad of improvements to bridge settings, including a complete redesign of bridge cards with improved sharing features, and a new section designed to help you find more bridges elsewhere. Lastly, the design of onion site errors has received a visual refresh aimed at making them consistent with the other kinds of Network Errors you can find in Tor Browser.
What's new for Android?
New connection experience
We've completely replaced Tor Browser for Android's connection screens with a new, "native" implementation. This is a welcome and necessary first step in our longer-term efforts to bring Connection Assist – a feature which can circumvent censorship of the Tor network automatically – to Android in a future major release. However, while we await Connection Assist's arrival, Tor Browser's new connection screens already offer a series of small improvements for Android users.
In order to establish a firm foundation on which we can expand Android's connection features in future, these screens have also been made more consistent with desktop. Ultimately, it's our hope that a user who can successfully circumvent censorship on desktop will be able to pick Android up without needing to relearn how it works.
In addition to a visual refresh, you can now enable the option to connect automatically (based on your last used connection settings) when the app is launched. Plus, you can also access the full settings menu before connecting to Tor – either by tapping the settings icon, or via the new button to "Configure connection" – where you can find the new Tor logs too (more on that below!).
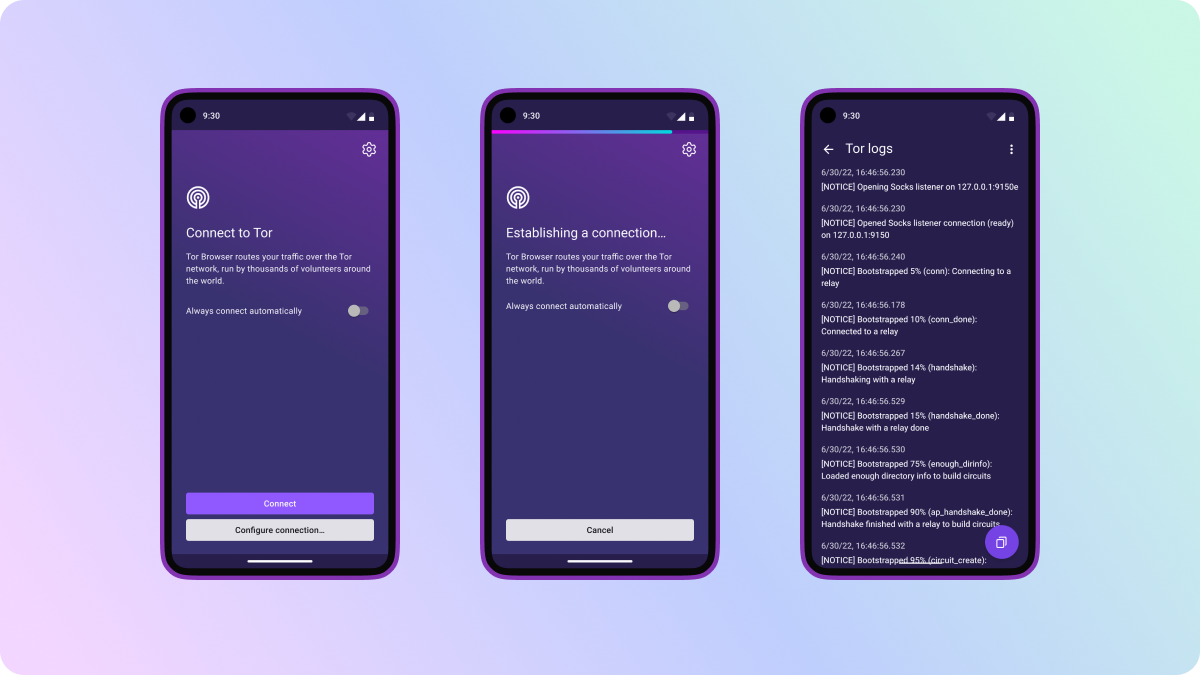
A permanent home for Tor logs
As many of you may know, Tor Browser maintains a log of Tor's background activity to help troubleshoot issues when they occur. Tor logs don't contain any sensitive information about your browsing activity, but simply reveal what Tor is trying to do behind the scenes – for example, these logs typically include a record of Tor's bootstrapping progress, plus any warnings or errors as they occur.
Should a user run into a problem and contact support, we may request a copy of your Tor logs to help them diagnose the issue. However, in previous versions of Tor Browser for Android, Tor logs could only be found by swiping to the side during the connection sequence. This meant that once Tor Browser had established a successful connection, users were unable to return to this screen to view and copy their Tor logs.
To address this issue, we've rebuilt and relocated Tor logs to a new section within Settings called "Connection Settings" – which is exactly where you can find Tor logs on desktop too. Given that the settings menu can now be accessed regardless of your connection status, this means that you can retrieve your Tor logs at any point while using Tor Browser. And finally, there's a handy button you can use to copy all logs without needing to fiddle around with selecting text.
What's new for desktop?
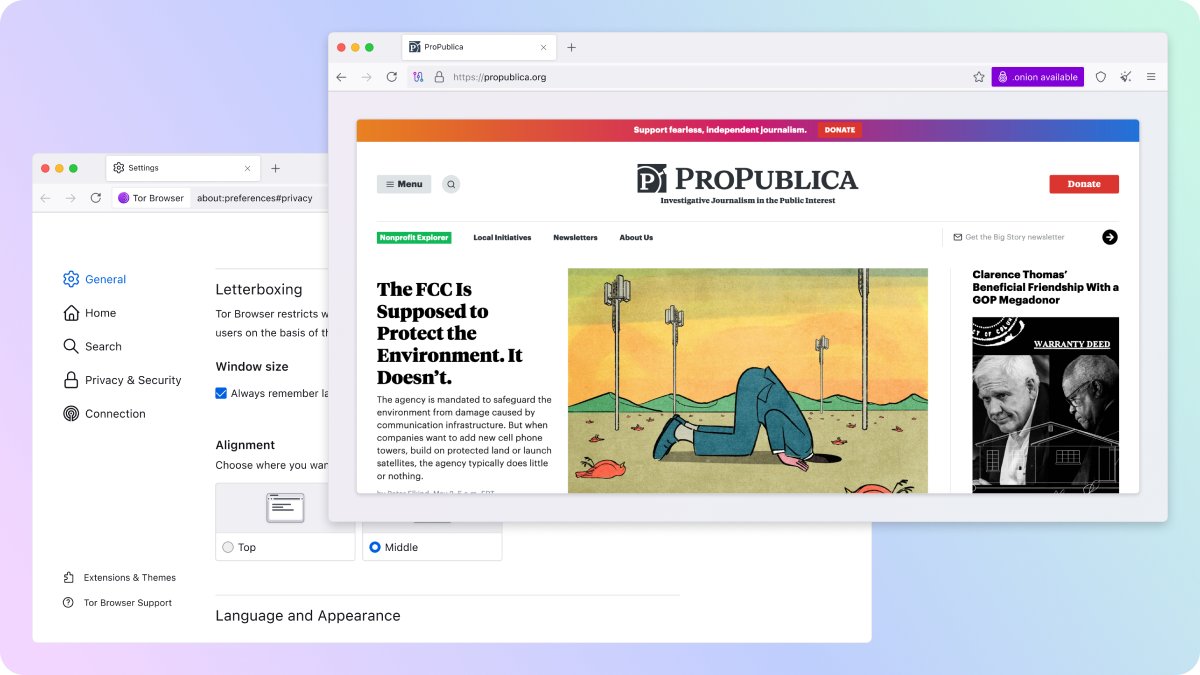
Introducing Betterboxing
"What are those gray bars?" is a question we get so frequently from new users, that it has its own entry on our support website. And the answer is: the letterbox!
To recap, letterboxing was introduced in Tor Browser 9.0 to allow users to resize their browser window without fear of being fingerprinted by rounding the inner content window (sometimes referred to as the "viewport") down to the nearest hundred pixels. This technique works by grouping the window sizes of most users into a series of common "buckets", protecting individual users within those buckets from being singled-out based on their window or screen size.
Although the existing implementation of letterboxing works excellently to protect you from fingerprinting, its visual design would often be misinterpreted by new users either as a bug with the browser or rendering issue with the website they're browsing. Based on the user feedback we've collected online, in our user research activities and during training sessions we've identified the following issues:
The design doesn't look very deliberate, hence users who misinterpret the letterbox as browser breakage instead. In response we've given the visual design of the letterbox a little polish – however the elements we've introduced have been kept deliberately subtle so as to avoid distracting you from the content you're actually trying to view.
Letterboxing as a feature isn't acknowledged anywhere in Settings, because in the past, there were no additional options to configure. Beginning in this release, you can now find a new letterboxing section in General Settings, including the options to remember your last known window size and choose whether you prefer the letterbox to be aligned to the top or middle of your browser window.
Pro tip: if, like me, you find yourself manually resizing Tor Browser to hide the margins letterboxing has introduced – you can now double-click within the letterbox margin to snap Tor Browser down to its next window size.
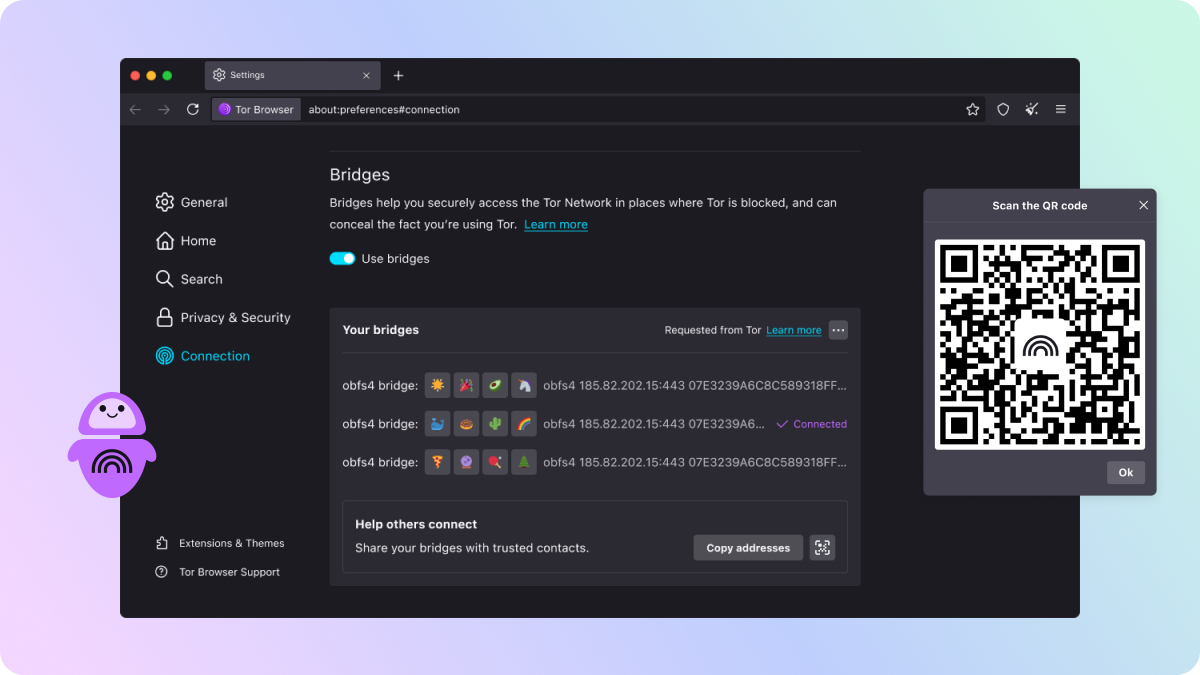
Even better bridge settings
Bridge users will notice a series of refinements coming to Connection Settings in this release, aimed at helping censored users find working bridges and improve the management of multiple bridges when added.
Bridge cards, first launched in Tor browser 11.5, are now displayed in a single, more compact card rather than the previous stacks of cards. To help you remember where your bridges came from, the new bridge cards also come pre-labelled with the source of your bridges, be they built in, requested from Tor, or added by you. Finally, when you have three or fewer bridge cards added, you can now share all of them at once instead of the previously fiddlesome process of sharing one at a time.
When Tor Browser's built-in options don't cut it, you can also find a new "Find more bridges" section which points the way to additional channels where censored users may retrieve bridges – including Telegram, the "Get Bridges" website, and via email. The existing ability to "Request a bridge" has been moved here too, allowing users to retrieve bridges from Tor Browser's built-in bridge bot without needing to connect to Tor first.
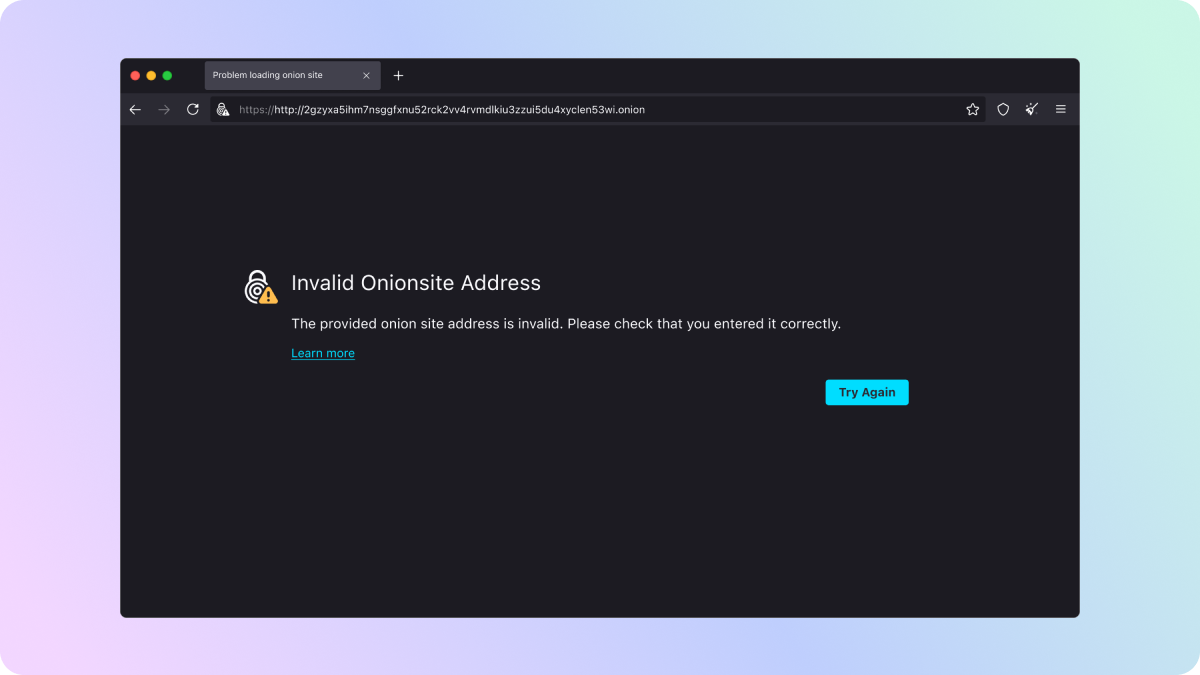
Simplified onion site errors
Unless you're perfect, you've probably misspelled a website's address at some point and landed on an error screen instead. The user-friendly messages you receive when you run into an issue like this are known as Network Errors, or neterrors for short, and were introduced to Firefox all the way back in version 1.5.
For the last few years onion site errors have appeared different from other types of neterrors in Tor Browser. Although the design decisions behind this change were well intentioned, they sometimes led to confusion about the source of the issue. In response, we've simplified the design of our onion site errors and made the user experience consistent with other types of neterrors you may encounter while you surf the onionverse.
Release notes
Due to Firefox ending support for older versions of Windows and macOS, Tor Browser 13.5 will be the final major version of Tor Browser to support Windows 8.1 and older, and macOS 10.14 and older.
Keeping Tor Browser up to date is critical to maintaining your privacy, security and anonymity. However following Tor Browser 14.0's release in Q4 this year, users of these platforms will no longer receive important updates. Therefore we strongly encourage affected users to update their systems to supported versions of Windows and macOS before the next release, and users running older versions of Windows and macOS will begin seeing messages to this effect in Tor Browser.
Contributors <3
Thanks to all of the teams across Tor, and the wider community, who contributed to this release. In particular we'd like to extend our gratitude to the following volunteers who have contributed their expertise, labour, and time to this release:
- guest475646844: tor-browser#42354
- Mynacol: tor-browser-build#41073
- NoisyCoil: tor-browser#42491, tor-browser#42501, tor-browser-build#41137, and tor-browser-build#41038
- ppisar: rbm!59
- RustyBird: tor-browser-build#41110
- thorin: too many to count <3
If you would like to contribute to a future release, please see our guide for new contributors to get started. Lastly, if you find a bug or have a suggestion for how we could improve this release, we'd love to hear your feedback.
Full changelog
The full changelog since Tor Browser 13.0.16 is:
- All Platforms
- Bug tor-browser#40856: Add a default for preferences in TorSettings
- Bug tor-browser#40919: Consider dropping protection against line-height introduced in #23104
- Bug tor-browser#41114: Fix no-async-promise-executor on TorConnect
- Bug tor-browser#41467: compat: beacon: re-enable the API but transform it to a no-op
- Bug tor-browser#42153: Drop dom.enable_resource_timing = false preference
- Bug tor-browser#42246: Migrate tor connection stuff from browser to toolkit
- Bug tor-browser#42290: "DuckDuckGoOnion" is a weird naming format for onion search engines
- Bug tor-browser#42302: The allowed ports string contains a typo
- Bug tor-browser#42308: Update README for tor browser
- Bug tor-browser#42315: compat: why is eventCounts undefined?
- Bug tor-browser#42336: Review the relationship between TorSettings and the TorProvider
- Bug tor-browser#42340: TorBridgeChanged notification sends out "[object Object]" as its data
- Bug tor-browser#42343: Consume pt_config.json in the browser
- Bug tor-browser#42354: Refactor exclusions in ShouldSanitizePreference() to the pref list.
- Bug tor-browser#42358: Separate the domain fronted requests from Moat
- Bug tor-browser#42359: Handle firewall and proxy in TorSettings.setSettings
- Bug tor-browser#42390: Betterboxing: make the decorator border disappear when the corners are flat
- Bug tor-browser#42397: Change RFP-spoofed Timezone from UTC to a real-world, less discriminable one
- Bug tor-browser#42437: Drop "torbrowser.version" preference
- Bug tor-browser#42466: Drop the "Onion Logo" from trademark statement
- Bug tor-browser#42479: Switch from localized strings to error codes in TorConnect errors
- Bug tor-browser#42481: Modularize SecurityLevel
- Bug tor-browser#42521: Remove unused onboarding strings
- Bug tor-browser#42529: Try not to spoof system-ui in contexts exempt from RFP
- Bug tor-browser#42537: Move Fluent files from "browser" to "toolkit"
- Bug tor-browser#42538: Move onion icons to toolkit
- Bug tor-browser#42549: Remove brand.dtd
- Bug tor-browser#42604: Add some debug logs about circuits
- Bug mullvad-browser#241: Move network.proxy.failover_direct=false pref to base-browser
- Bug tor-browser-build#41111: Use Lyrebird to provide WebTunnel PT Client
- Windows + macOS + Linux
- Bug tor-browser#40843: Add a working state to the Internet test button in connection settings
- Bug tor-browser#41621: Tweak about:torconnect styling
- Bug tor-browser#41622: Convert onion site errors to the new neterror template
- Bug tor-browser#41814: Change "vanilla bridge:" to "Tor bridge:" in bridge cards
- Bug tor-browser#41916: Letterboxing preferences UI
- Bug tor-browser#41917: Make the appearance of letterboxing look more intentional
- Bug tor-browser#41918: Add option to reuse last window size when letterboxing is enabled
- Bug tor-browser#41930: intl.accept_languages gets into a stuck modified state
- Bug tor-browser#41966: Cannot remove locales from the locale alternatives list
- Bug tor-browser#42036: Design and build a user interface for Lox
- Bug tor-browser#42192: Correctly round new windows when bookmarks toolbar is set to "Only Show on New Tab"
- Bug tor-browser#42202: Fluent migration: crypto safety
- Bug tor-browser#42203: Fluent migration: about dialog
- Bug tor-browser#42204: Drop unused aboutTor.dtd
- Bug tor-browser#42206: Fluent migration: about:rulesets
- Bug tor-browser#42207: Fluent migration: preferences
- Bug tor-browser#42209: Fluent migration: tor circuit
- Bug tor-browser#42210: Fluent migration: download warning
- Bug tor-browser#42211: Fluent migration: new identity
- Bug tor-browser#42214: Fluent migration: security level
- Bug tor-browser#42270: Implement design changes to QR code dialog
- Bug tor-browser#42303: Remove unused "help" button logic in tor dialogs
- Bug tor-browser#42319: Make all the wordmark of the same size
- Bug tor-browser#42387: Visual noise in 13.5a4 letterboxing
- Bug tor-browser#42389: Betterboxing: gradient is never shown
- Bug tor-browser#42398: Include Alpha and Nightly in MOZ_APP_DISPLAYNAME (and possibly in other places)
- Bug tor-browser#42405: Fix betterboxing + findbar horizontal bounce if the scrollbar is not an overlay
- Bug tor-browser#42414: Show ellipsis when the tor bridge address overflows
- Bug tor-browser#42415: Improve focus styling for forced focus in bridge settings
- Bug tor-browser#42421: Remove bridge option should be hidden for Lox bridges
- Bug tor-browser#42423: Move temporary Lox Fluent strings to new file
- Bug tor-browser#42425: Improve accessibility of the bridge emoji cells
- Bug tor-browser#42443: Shrink the window to match letterboxing size when the empty area is doble-clicked
- Bug tor-browser#42446: Improve accessible descriptions in built-in dialog
- Bug tor-browser#42457: Loading icon for bridge pass (Lox) invites
- Bug tor-browser#42458: Update the "Submit Feedback" link in "About Tor Browser"
- Bug tor-browser#42476: Only allow Lox (invites) in alpha and nightly builds
- Bug tor-browser#42489: Lox module notifications
- Bug tor-browser#42490: Install svg from branding theme to browser/chrome/icons/default
- Bug tor-browser#42496: Moat refresh bug
- Bug tor-browser#42500: When startup window is maximized per letterboxing.rememberSize on startup, the restore button shrinks it to its minimum size
- Bug tor-browser#42504: TB Bookmarks: Add the Tor forum .onion to the bookmarks
- Bug tor-browser#42510: SETCONF Tor control protocol command should not be used when system Tor is configured / TOR_SKIP_LAUNCH=1 is not honored
- Bug tor-browser#42511: false positive message: browser tab bar shows "Not connected" even though connected in a system Tor etc. context
- Bug tor-browser#42520: Correctly record new initial window size after auto-shrinking
- Bug tor-browser#42533: Add Lox notification for activeLoxId
- Bug tor-browser#42540: Fix gNetworkStatus.deinint typo
- Bug tor-browser#42541: Circuit Display does not work when using Conjure pluggable transport
- Bug tor-browser#42542: Quirks when onion authentication prompt is shared between two tabs
- Bug tor-browser#42573: Tweak language notification to avoid formatValue
- Bug tor-browser#42574: Exempt pdf.js from letterboxing
- Bug tor-browser#42583: Modify moz-support-link
- Bug mullvad-browser#262: Mouse-over long links causes the browser element to re-center relative to width of status tooltip
- Bug mullvad-browser#289: The Letterboxing>Content Alignment heading doesn't follow the Firefox design document capitalization
- Bug tor-browser-build#41149: Add be, bg and pt-PT translations to nightlies
- Windows + macOS
- Bug tor-browser#41405: Win ≤8.1 and macOS ≤10.14 not supported in ESR 128
- Bug tor-browser#42347: Add a banner warning users about the upcoming EOL for Win ≤8.1 and macOS ≤10.14
- Bug tor-browser#42586: Add support link to OS deprecation message
- Windows
- Bug tor-browser#41859: Font used for IPs in circuit display is illegible
- Bug tor-browser#41901: windows: FontSubstitutes can leak system locale
- Bug tor-browser#42163: Make the 3rd party DLL blocklist obey portable mode
- macOS
- Bug tor-browser-build#40569: Create build-specific installer for macOS
- Linux
- Bug tor-browser#42438: Adapt the data import wizard to use the original $HOME on Linux
- Bug tor-browser-build#41112: Fix indentation of projects/browser/RelativeLink/start-browser
- Bug tor-browser-build#41136: Include *.deb in the list of files to gpg sign
- Android
- Bug tor-browser#41187: Improve Android's bridge settings UI
- Bug tor-browser#41846: Disable new nimbus use in firefox-android 115
- Bug tor-browser#42017: TBA13: system/widget font tests: font-family not returned in getComputedStyle
- Bug tor-browser#42248: Allow GeckoView to launch tor
- Bug tor-browser#42249: Allow GeckoView to launch lyrebird
- Bug tor-browser#42250: Allow Moat.sys.mjs to invoke lyrebird on Android
- Bug tor-browser#42252: Plumb down TorConnect commands from firefox-android to GeckoView
- Bug tor-browser#42253: Remove "New private tab" action and widget
- Bug tor-browser#42259: Remove unused firefox branding from Tor Browser for Android
- Bug tor-browser#42260: Add TBB artifacts to .gitignore
- Bug tor-browser#42301: Make TorSettings interact with the old Android Settings
- Bug tor-browser#42317: Update "Security Settings" menu item
- Bug tor-browser#42323: Add a checkbox to enable the connect assist experiments on alpha
- Bug tor-browser#42409: TTP-03-011 WP3: Potential DoS due to Deep Link abuse
- Bug tor-browser#42427: Do not ship bridges as preferences anymore
- Bug tor-browser#42486: firefox-android bridge settings sometimes dont save
- Bug tor-browser#42522: The quick connect switch on Android seems too much on the right side
- Bug tor-browser#42552: TBA: formatting APIs are en-US only
- Bug tor-browser#42566: Remove 'Enable beta connection features' menu item in stable release channel
- Bug tor-browser#42567: Remove 'Enable beta connection features' toggle
- Bug tor-browser#42571: The new bootstrap on Android breaks if the browser goes in background
- Bug tor-browser#42576: Backport Bug 1885171: use the private keyboard for prompts on Android
- Bug tor-browser#42578: Reject Android "open in Tor Browser" intent
- Bug tor-browser#42582: Accepted languages should use id and he on Android
- Bug tor-browser#42593: Unable to disable bridges after they have been configured and successfully bootstrapped
- Bug tor-browser#42618: Addons on Android have a stale cache
- Bug tor-browser#42619: Cannot install Android addons from AMO
- Bug tor-browser#42632: Don't display builtin bridges in provide bridge popup
- Bug tor-browser#42636: A bad bridge line might get TBA stuck
- Bug tor-browser#42648: Don't cancel tor bootstrap when opening settings from bootstrap
- Bug tor-browser-build#41143: Enable multi-locales also on GeckoView
- Build System
- All Platforms
- Bug tor-browser#42331: tb-dev fetch command is missing repository argument
- Bug tor-browser#42516: Make tb-dev worktree-compatible
- Bug tor-browser#42594: Update mach to work with Python 3.12
- Bug tor-browser-build#40852: Reproducible build of the the lox client library to wasm
- Bug tor-browser-build#40983: Bump the various branches to 13.5 on main
- Bug tor-browser-build#41001: Create Release Prep MR generating script
- Bug tor-browser-build#41037: Set time on signing machine before starting signing
- Bug tor-browser-build#41038: Add RPM dependencies to README
- Bug tor-browser-build#41045: Dump more information about build times on Firefox
- Bug tor-browser-build#41048: Drop the kcp-go project
- Bug tor-browser-build#41073: Update documentation about required packages for container-less build
- Bug tor-browser-build#41081: Update detailsURL in tools/signing/nightly/update-responses-base-config.yml
- Bug tor-browser-build#41148: Update projects/browser/Bundle-Data/Docs/Licenses/NoScript.txt
- Bug tor-browser-build#41153: Update README for Ubuntu 24.04 unprivileged user namespace changes
- Bug tor-browser-build#41154: Update keyring/boklm.gpg for new subkeys
- Bug tor-browser-build#41161: Explicitly fetch tags in the release preparation script
- Bug rbm#40071: Add an option to create zip files using 7z
- Bug rbm#40073: We should remove ./ when using 7-zip for zip files
- Bug rbm#40076: Correctly refresh file when computing input_files_id and a file is set as refresh_input
- Windows + macOS + Linux
- Bug tor-browser#42305: (Semi-)Automatically merge translation resources across tor browser releases (desktop)
- Bug tor-browser#42501: Move
--disable-emeto OS- and architecture-specific mozconfigs - Bug tor-browser#42519: Update the profile directory patch to check both for
system-installand foris-packaged-appfile - Bug tor-browser-build#41057: make fetch is not fetching mullvad repo
- Bug tor-browser-build#41078: pt_config.json not touch'd before adding to omni.ja, resulting in build non-determinism
- Bug tor-browser-build#41088: Remove use of projects/browser/run_scripts
- Windows
- Bug tor-browser-build#40606: Use Clang to compile NSIS
- Bug tor-browser-build#40900: Update NSIS to 3.09
- Bug tor-browser-build#41065: Do a cleanup of the NSIS script
- Bug tor-browser-build#41076: Include the ShellLink plugin in NSIS
- Bug tor-browser-build#41097: authenticode-timestamping.sh fails to run again because tmp-timestamp already exists
- Bug tor-browser-build#41150: Do not check for SSE2 on the Windows installer
- macOS
- Bug tor-browser-build#41084: $app_bundle is missing the final .app in projects/firefox/build
- Bug tor-browser-build#41124: Since TB/MB 13.5a5 macos signed installers contain all .DS_Store
- Linux
- Bug tor-browser#42491: Add mozconfig-linux-aarch64
- Bug tor-browser-build#41046: Use the final path for Linux debug symbols
- Bug tor-browser-build#41126: Make deb and rpm packages for Tor Browser
- Bug tor-browser-build#41137: Build gcc-cross and tor-expert-bundle for linux-aarch64
- Bug tor-browser-build#41160: Enable build of Tor Browser rpm/deb packages for nightly only
- Android
- Bug tor-browser#40502: Do not recommend addons on Tor Browser
- Bug tor-browser#42399: Re-enable minimization of JS for Android
- Bug tor-browser#42568: Remove legacy tor dependencies from firefox-android
- Bug tor-browser#42569: Remove tor-onion-proxy-library and and tor-android-service deployment/ingestion steps from firefox-android dev tools/scripts
- Bug tor-browser#42570: Add tor-expert-bundle aar deployment/ingestion step to firefox-android dev tools/scripts
- Bug tor-browser#42581: Check if a file exists before trying to sign it in tools/tba-sign-devbuild.sh
- Bug tor-browser-build#41080: Re-pack omni.ja with 7-zip on Android
- Bug tor-browser-build#41082: Package tor expert bundle on android as .aar that firefox-android can use in lieu of tor-android-service with geckoview bootstrap
- Bug tor-browser-build#41092: Use an uncompressed omni.ja to improve final apk compression.
- Bug tor-browser-build#41093: Sign unsigned APKs instead of the QA-signed ones
- Bug tor-browser-build#41127: Android testbuilds fail because of the too early MOZ_BUILD_DATE
- Bug tor-browser-build#41139: Remove tor-android-service and tor-onion-proxy-library dependencies and ingestion steps from firefox-android config and build script
- Bug tor-browser-build#41140: Remove tor-onion-proxy-library and tor-android-service projects from tor-browser-build
- Bug tor-browser-build#41141: Add tor-expert-bundle aar dependency to firefox-android
- Bug tor-browser#42201: Make the script sign all the channels for local builds
- Bug tor-browser#42258: Replace the current boring "fiery android" icon we use for dev with the cool nightly icon
- All Platforms
Comments
We encourage respectful, on-topic comments. Comments that violate our Code of Conduct will be deleted. Off-topic comments may be deleted at the discretion of the moderators. Please do not comment as a way to receive support or to report bugs on a post unrelated to a release. If you are looking for support, please see our FAQ, user support forum or ways to get in touch with us.