Measuring Tor and Iran

I've been fielding some calls from the press about Tor and Iran. Someone quoted me as saying "double the clients from Iran over the past few days". We wondered, what are the real numbers? What does our network see from Iran? Is port 443 or https:// really blocked? Here's what we've discovered in the past day of working with the new metrics we've developed to be safe to collect without compromising anyone's anonymity.
This first dataset is from one of the Directory Authorities. We have six authorities, so a plausible scaling factor is 6, assuming all authorities are seeing equal requests (it could be more or less than 6, too). We don't know if the authorities are seeing equal requests, as they listen on different TCP ports, are located in different parts of the world, and clients will chose one randomly. This graph roughly shows the number of requests from new Tor clients coming from IP addresses that our geoip database reports as Iran.
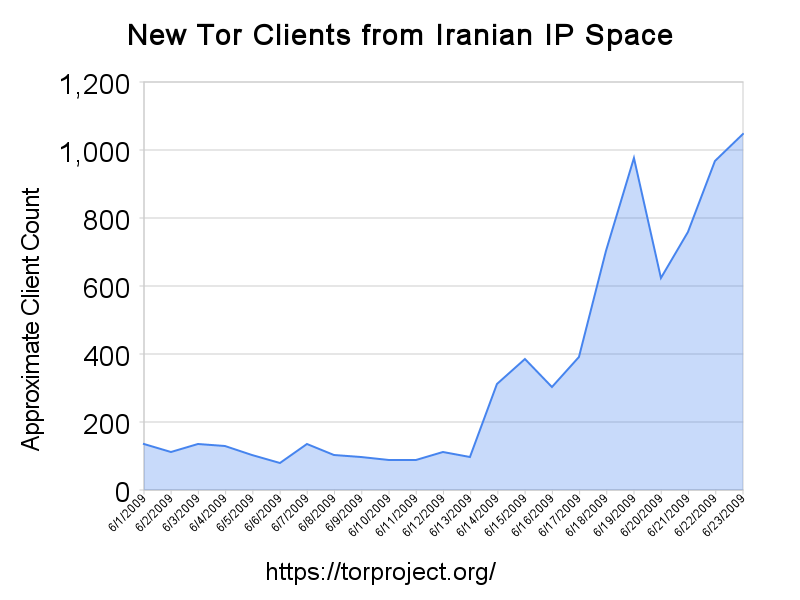
UPDATE 2009-06-24: Updated the graph with numbers through yesterday
The second dataset is from one Directory Mirror, of which there are hundreds. This mirror is only accessible on port 443, which is rumored to be blocked in parts of Iran over the past few days.
.png)
The data points in the second graph are very rough, since they're an estimate of the total number of Tor users in Iran based on numbers from only one relay. In addition, we looked at some other relays running on port 443, and they also didn't show anywhere near the spike that we see in the directory authority graph above. The authority isn't listening on 443 -- perhaps that means there's some truth to the rumors that port 443 has been blocked recently in Iran. We look forward to having more precise data later on.
Comments
Please note that the comment area below has been archived.
To the stars!
I love that skyrocketing line from the 17th to today :) Good stuff. Any pretty pictures of the increase in relays (assuming there has been one)?
Port 9001??
What if we have our relay set up on port 9001?? Should we switch to port 443? Is 9001 useful??
Re: Port 9001??
It's really too early to guess what ports are having problems, at least
based on the data we're seeing so far.
I might suggest that a safe answer for now is "anything but port 443".
Well nice to see the
Well nice to see the comparison , There is a good rise in the recent times. But it still needs a lot to improve.
church chairs
On which ground port 443 is
On which ground port 443 is unsafe?
Iran
I think Moussavi is not going to call for a march tomorow...He is part of the regime ...he is no different to Ahmadi Nejad...The young in Iran now need directions...Please help them MSKR
Join the Resistance
If you are interested in helping, consider joining the National Iranian Resistance - we will be street fighting the Basiji soon if Allah allows it
I'd love too but I'm in a
I'd love too but I'm in a different country.I wish you luck
I'd love too but I'm in a
I'd love too but I'm in a different country.I wish you luck
I guess it's blocked in
I guess it's blocked in iran.one day i saw the servers my tor will be connected are giving the error"no current certificate known for " in the valida message log.and today when i checked it all of them were not accessible.know the only program is being used here is "freegate"but that's shareware and only works for 1 month.So do something to solve the problem because we cannot use tor in iran now.that would be a big help for freedom in iran.
I should say all the sites and communication tools are blocked as:yahoo email and gmail , yahoo messenger,facebook,twetter and friendfeed .youtube also.
they are closing the doors to kill without a noise.
Re: I guess it's blocked in
I've heard from several people that Tor is still working fine in Iran.
But if it does get blocked one day, that's why we developed "bridges":
https://decvnxytmk.oedi.net/bridges
https://bridges.torproject.org/
Bridges function like proxies into the Tor network. One of the main advantages of bridges compared to proxies though is that you still get Tor's anonymity: even the operator of the bridge can't figure out what you're doing.
no bridge list on torproject.org
Its pretty dum for an ISP to block all tor nodes but left tor's front page open.
so what's the point of putting such a list on a forbidden page?
if the ISP is so interested in the bridges they wouldn't border refreshing the list page all day long, will they? :- )
Yes, make sure to read about
Yes, make sure to read about bridges. The Tor Project even offers an auto-reply service through which you can email them from a gmail account, and get a list of bridges you can use immediately. The documentation on this site is your friend!
i have change my port to Ort in 80 and Dir at 445 for Iran
Hello,
I have change my port Ort to 80 and 445 for the Dir and hope will help the peoples blocked with 445 in Ort.
i hope all will fine :)
my best
So do something to solve the
So do something to solve the problem because we cannot use tor in iran now.that would be a big help for freedom in iran.
Turkey Holidays 2010 || Dubai Holidays
Update
Greets -
(Someone there use Amar or Aram as IRC nick? FF crashed; killed my historycheers @bentrem.)
This data is 5 days old now ... can you update?
cheers
--bentrem
p.s. my link is to the resources page I cobbled together
p.s.2 http://asert.arbornetworks.com/2009/06/a-deeper-look-at-the-iranian-fir… "A Deeper Look at The Iranian Firewall" | "Iranian Traffic Engineering" > http://asert.arbornetworks.com/2009/06/iranian-traffic-engineering/ < (ArborNetworks)
Re: Update
"This data is 5 days old now ... can you update?"
I don't have any graphing tools nearby, but here are the next data points for that top graph above, one per day:
624
760
968
1048
So there was a dip, but now it's up even higher.
[Edit: the next two numbers are 1416 and 1280.]
Updated graph
The graph is now updated with current information.
NedaNet
see also: NedaNet, "a network of hackers formed to support the democratic revolution in Iran. [NedaNet's] mission is to help the Iranian people by setting up networks of proxy severs, anonymizers, and any other appropriate technologies that can enable them to communicate and organize -- a network beyond the censorship or control of the Iranian regime."
IRAN Company
buddy .. here is my problem..
i am working in a company we have Firewall and proxy.. i used Tor on them and it work with no problem ,, but the thing is i have to log in company domain to access everything and that will get my in big problem .. is there way to configure tor to log in without using the domain user name and password.. and just log on the pc as local machine user.
thanks
will Tor stop the DPI layer7 kit, i dont think so
the question that NEEDS answers ASAP is will ANY software such as Tor stop the DPI (Deep Packet Inspection) interception or at least protect the core packet data from being seen and decoded ?,
i dont think so, as it's hardware layer7 kit that can see and realtime process every single bit of data flow coming and going, and more so can infact inject anything they please into the streams dataflows without you realising their doing it to you....
https://nodpi.org/
Yes.
Unless the DPI can crack SSL/TLS on the fly, Tor shouldn't be affected. The TLS authentication built into Tor will ensure the client is talking to a real node.
DPI can crack SSL
DPI can crack SSL
I think that's not true. DPI
I think that's not true.
DPI approaches can recognize that a given flow is using SSL, but that's different from learning the session key for the SSL flow.
There are plenty of products out there that mitm SSL connections, but they do it by exploiting the certificate authority infrastructure, that is, the PKI. See e.g.
http://files.cloudprivacy.net/ssl-mitm.pdf
But the underlying SSL algorithm is still considered safe.
connecting from inside
connecting from inside ;-)
port 443 is not totally blocked , but it seems that 443 bandwidth is badly shaped to some minimum amount.
I personally can't connect to tor network , and I think it times out,while trying to connect.
Same phenomena happens when I try login to some SSL enabled services like yahoo mail.Need to wait for a long time to login page appear.
Is DPI possible if we are
Is DPI possible if we are NOT running our bridge/relay on 443, considering that 443 may be blocked? Similarly, is encryption in general compromised if the bridge/relay is not via 443? Thank for your help.
internal tor traffic is
internal tor traffic is still encrypted regardless of port. Even 80.
Don't post these numbers
Couldn't you have kept this under wraps for a little more time?
In this case I think you should have kept the actual numbers hidden, until perhaps, hopefully, the situation in Iran improves. No need to call attention and showing the Iranian gov., the actual numbers. Let them guess, or speculate.
As to all those helping out by providing relays, bridges,etc.. keep up the good work. I'm sure it's appreciated.
I agree with you, we needn't
I agree with you, we needn't call the attention from Iranian gov.
Seriously, I don't doubt
Seriously, I don't doubt your intentions, but I agree with the people who've suggested this informattion would've better gone unpublished (at least for now). Really just throwing my comment in to ask you to at least avoid providing updates on the situation.
I'm as interested as anyone to know the figures, but the feedback it provides to the Iranian government, is wholly counterproductive. Even more so, if you update the figures.
Anyway, said my bit.
Other than that, thanks for all the stuff you do.
can I setup Tor bridges for specific countries(IRAN)
I live in canad and I have just installed Tor on my apple,is there a way to help specificaly iranian clients use my relay-bridge services as opposed to being only a part of the global network.
looking forward to hear from u soon
thanks for your support
specific countries
http://iansbrain.com/
read carefully (article about Tor) and you will find
75.118.29.110:443
75.118.29.110:443 6F0DF98DE5718652D039D50214646A864B0374C2
Hmm, all of you seem to be
Hmm, all of you seem to be pretty sure that you are "helping the people" in Iran. But have you ever considered that those clients connecting also could be foreign (CIA, Mossad, etc.) agent provocateurs that were send to Iran in order to instill unrest? Because one thing is clear: THEY want to get Iran. This way or another. And THEY will get it sooner or later. All the things we hear recently are part of that operation. Why does no one wonder why we read so much about Iran lately, but never or rather seldom about the countless other places in the world, which undoubtly have issues as well? What makes Iran so special?
re: iran help
We're sure we're helping the people of Iran because we've heard from them directly. Yes, it's also possible that "iranian activists" are also CIA, Mossad, or Alien Life Forms from Alpha Centauri. We'll never know for sure.
We hear about Iran so much lately because the mainstream media caught on to the story. We also hear from people in other countries as well, such as: Burma, Sri Lanka, Saudi Arabia, Lebanon, USA, France, Germany, UK, South Africa, Ghana, Kenya, Tunisia, Morocco, Portugal, Italy, Australia, China, Moldova, South Korea, etc. The list goes on.
there is many possibility my
there is many possibility my friend but, when you block the real people from reaching news and communicating with each other your are doing something wicked. its our right to choose who to be a government of iran.
soon or late we will win :)
Just some randomly picked
Just some randomly picked incidents:
http://en.wikipedia.org/wiki/Gladio
http://en.wikipedia.org/wiki/Nayirah
http://en.wikipedia.org/wiki/Operation_Condor
i can't connect with tor
i can't connect with tor please help
we cant connect from Iran
we cant connect from Iran and bridge not work please help
TOR not working in iran
I this problem too, after Sep.19 when port 443 was blocked in iran I cannot connet to the network despite numerous bridges I've used. I can provide you with debug level log if you care.
Tor is not working for me
Tor is not working for me too since the same time. It seems after the killings, tortures, rapes they have gotten more serious to block the flow of information. Bridges doesn't work. For now I am using a proxy: Settings -> Network -> I use a proxy to access the Internet. However it is slower than before. You can also find other ways. But anyway please help.
Of course be careful about
Of course be careful about proxy you are using. It seems you lose anonymity at that proxy.
Government agent or supporter above !
The guy above is talking nonsense. CIA and Mosad can find other ways because of their sophistication if not Tor. But we Iranians need Tor just to speak things which is ordinary in most other countries. Without Tor we might get caught. We love our country, we just want more space to speak. That guy is a government agent or supporter. The recent events in Iran were by Iranians for a little more freedom. Of course CIA bastards may use anything but we don't shut up because you think CIA want this or that. The IRI has suppressed us for years by the same excuse. Whenever we want a right, they accuse us helping foreigners or even being their agents. It is one of their big weapons: "You are helping USA, so shut up and do what we want and respect what we respect, otherwise ...." Guess what: prison or deprivation from going to university and alike.
Tor Doesn't Work Since 19 September to Today 29 September 2009
Why Tor Project stopped on the step of "establishing an encrypted directory connection"?
I live in Iran. Feom 19 September 2009 to Today 29 September, I tried Tor and it stopped in the step of "establishing an encrypted directory connection" , Please tell me how can I fix this?
These errors are also related to the "establishing an encrypted directory connection" problem: "no route to host" "No current certificate known for authority ..."
The recent events in Iran
The recent events in Iran were by Iranians for a little more freedom. Of course CIA bastards may use anything but we don't shut up because you think CIA want this or that. The IRI has suppressed us for years by the same excuse. Whenever we want a right, they accuse us helping foreigners or even being their agents. It is one of their big weapons: "You are helping USA, so shut up and do what we want and respect what we respect, otherwise ...." Guess what: prison or deprivation from going to university and alike.
John,
watch alice in wonderland online
Yes, it is working today in
Yes, it is working today in Iran!
It is not very nice. It is a
It is not very nice. It is a pity that on the one hand it is declared that there is a freedom of press but the other hand we see such situations. Well, Iran is a very interesting country. It seems to me that we have stereotypes about Iranians. I've seen one documentary which proves it. Found it at the rapidshare SE http://rapidpedia.com .
italy: starting at 01:00 if
italy:
starting at 01:00 if 10 February 2010
tor is non accessible in Italy
i'm experiencing problem in connection
here's the last log:
Feb 10 04:20:54.944 [notice] Tor 0.2.1.22 opening log file.
Feb 10 04:20:54.944 [notice] Parsing GEOIP file.
Feb 10 04:20:55.341 [notice] No current certificate known for authority moria1; launching request.
Feb 10 04:20:55.341 [notice] No current certificate known for authority tor26; launching request.
Feb 10 04:20:55.341 [notice] No current certificate known for authority dizum; launching request.
Feb 10 04:20:55.341 [notice] No current certificate known for authority ides; launching request.
Feb 10 04:20:55.341 [notice] No current certificate known for authority gabelmoo; launching request.
Feb 10 04:20:55.341 [notice] No current certificate known for authority dannenberg; launching request.
Feb 10 04:20:55.341 [notice] No current certificate known for authority urras; launching request.
Feb 10 04:20:55.341 [notice] Bootstrapped 5%: Connecting to directory server.
Feb 10 04:20:55.341 [notice] I learned some more directory information, but not enough to build a circuit: We have no network-status consensus.
Feb 10 04:20:55.396 [notice] Bootstrapped 10%: Finishing handshake with directory server.
Feb 10 04:21:25.456 [notice] No current certificate known for authority moria1; launching request.
Feb 10 04:21:25.456 [notice] No current certificate known for authority tor26; launching request.
Feb 10 04:21:25.456 [notice] No current certificate known for authority dizum; launching request.
Feb 10 04:21:25.456 [notice] No current certificate known for authority ides; launching request.
Feb 10 04:21:25.456 [notice] No current certificate known for authority gabelmoo; launching request.
Feb 10 04:21:25.456 [notice] No current certificate known for authority dannenberg; launching request.
Feb 10 04:21:25.456 [notice] No current certificate known for authority urras; launching request.
Feb 10 04:22:57.783 [notice] No current certificate known for authority moria1; launching request.
Feb 10 04:22:57.783 [notice] No current certificate known for authority tor26; launching request.
Feb 10 04:22:57.783 [notice] No current certificate known for authority dizum; launching request.
Feb 10 04:22:57.783 [notice] No current certificate known for authority ides; launching request.
Feb 10 04:22:57.783 [notice] No current certificate known for authority gabelmoo; launching request.
Feb 10 04:22:57.784 [notice] No current certificate known for authority dannenberg; launching request.
Feb 10 04:22:57.784 [notice] No current certificate known for authority urras; launching request.
Feb 10 04:29:03.003 [notice] No current certificate known for authority moria1; launching request.
Feb 10 04:29:03.003 [notice] No current certificate known for authority tor26; launching request.
Feb 10 04:29:03.003 [notice] No current certificate known for authority dizum; launching request.
Feb 10 04:29:03.003 [notice] No current certificate known for authority ides; launching request.
Feb 10 04:29:03.003 [notice] No current certificate known for authority gabelmoo; launching request.
Feb 10 04:29:03.003 [notice] No current certificate known for authority dannenberg; launching request.
Feb 10 04:29:03.003 [notice] No current certificate known for authority urras; launching request.
Feb 10 04:40:14.202 [notice] No current certificate known for authority moria1; launching request.
Feb 10 04:40:14.203 [notice] No current certificate known for authority tor26; launching request.
Feb 10 04:40:14.203 [notice] No current certificate known for authority dizum; launching request.
Feb 10 04:40:14.203 [notice] No current certificate known for authority ides; launching request.
Feb 10 04:40:14.203 [notice] No current certificate known for authority gabelmoo; launching request.
Feb 10 04:40:14.203 [notice] No current certificate known for authority dannenberg; launching request.
Feb 10 04:40:14.203 [notice] No current certificate known for authority urras; launching request.
I used tor for years but now it's impossible
to post i'm temporaly using I2P
[edit]
i TRIED (5AM, Italian time) posting via I2P, but captcha didn't show up
now (3PM Italian time), tor is back and i can post
what happend?
[/edit]
could someone help?
where was the problem? how can avoid it to happen again?
is there a way to circumvent such a block?
The client "Finished handshake with directory server", but after that it do nothing more
any clue?
p.s. your captcha sucks ( LOL !!) it's so difficult to post here
thanks
Hi Tor doesn't work in Iran
Hi
Tor doesn't work in Iran at this time I add bridge but it doesn't work again
please HELP
Before am using tor without
Before am using tor without bridges but on june 19 2010 it stoped and i tried it with bridge but it coud'nt work is not even moving at all. Please i need help am from nigeria and we are using mtn network to connect and there ip: 10.199.212.2 port:8080. Please i need bridges.
69.169.160.185:1337
69.169.160.185:1337
A few questions and
A few questions and potential answers:
Bad Guys == Anyone blocking or monitoring a persons access to knowledge
Q: What is to stop operatives working for the bad guys from running tor proxies from 3rd party locations? Granted, they would only be able to sample a portion of the traffic, but traffic that they did sample could lead to identification of users. It doesn't seem like it would be that hard to match up the encrypted client side requests with the un-encrypted outgoing requests.
PA: The only solution I can think of here is centralized control of the proxy network provided by a press/media sponsorship model as opposed to the bandwidth volunteer model. It's to easy for bad guys to infiltrate the volunteer network. It would also be easier to swap in and out new proxies as they are blocked. runtime selection of alternative proxy networks would be a nice feature.
Q: I have noticed lists like: http://proxy.org/tor.shtml that appears to be a list of tor proxies. What's to stop the bad guys from blocking the entire proxy database? My understanding is that countries like Iran have the national ISP market under their thumb.
PA: There needs to be a way to deal out proxies to clients without the ability to easily reveal the entire network to anyone. Perhaps even semi-static assignments similar to DHCP. Of course, there is also the problem of 'blocking the dealer' similar to the P2P security issues with trackers. Ultimately, to really make this fool proof, there would need to be a way to communicate proxy dealers offline (verbally / off-network) in a concealable way.
Q: How can we address bad guys blocking port 443.
PA: Proxies should be able to hide behind other services such as 25,80,110. Also nice would be a 'spoof greeting' feature that would simulate a 'normal' service for that port before a magic code was sent. Of course, the magic code would need to be changeable (possibly dynamically by a proxy dealer).
Q: What about DPI which can provide encryption protocol info to the bad guys (if not the payload).
PA: plug-in packet obfuscation, possibly agreed upon between proxy and dealer and embedded in a magic code given by the dealer to the client then provided back to the proxy in the request header. This could be implemented by means of a tiny secure VM that ran small byte-code obfuscator programs shared between proxy and dealer and referenced by the magic code. Even though the bad guys could run the VM de-obfuscator, it would be challenging to implement at OSI levels 1-4 given current technology.
The ultimate idea would be to keep the Bad Guys busy chasing their tails and break them through over investment in competence. As they attempt to keep up with the changing methodologies they become victims of their own system of control, meanwhile they have less time to do their normal bad guy stuff. Basically, the circumvention tool itself becomes an agent provocateur.
--dbennett@bensoft.com
This would be a fine email
This would be a fine email to the or-talk mail list, but unfortunately you wrote it on our blog.
At a minimum, you should read our FAQ, where most of these questions are already answered. See https://trac.torproject.org/projects/tor/wiki/TheOnionRouter/TorFAQ
You may also want to read through the active project list, https://trac.torproject.org/projects/tor/wiki/projects, some of your PA's are already under way with a more advanced design than one can put into a FAQ style paragraph.
Agreed, sorry for the
Agreed, sorry for the laziness, I posted this on or-talk. If you feel it's better not to have this here, please feel free to delete this post.
thank you.
thank you.
http://archives.seul.org/or/t
http://archives.seul.org/or/talk/Sep-2010/msg00101.html
Hi At the time of this
Hi
At the time of this writing Tor is unaccessible here in iran and all of its ports are
blocked .
I was thinking can Tor ( privoxy ) use a well known port like 21 for FTP instead of
other ports like 8080 ? This is possible if Tor is not giving FTP service to users ,
that way they can't block port 21 , because FTP service will be blocked for all users .
However it's not a big deal for iranian regime to block FTP in the whole country .
Iranian users better know what i'm talking about . lol