New Release: Tor Browser 8.0

Update (09/07 10:15 UTC): We received reports of Tor Browser 8.0 crashing during start-up on older (10.9.x) macOS systems. This is tracked in bug 27482. The current Tor stable version, 0.3.3.9, is missing a patch to make it compatible with that old and unsupported (by Apple) macOS version. This will be fixed in the planned Tor Browser 8.0.1 release. Meanwhile, users affected by this bug can try the almost identical alpha release, 8.5a1, which is shipping a newer Tor version with this bug fixed. Sorry for the inconvenience.
For the past year, we have been collecting feedback on how we can make Tor Browser work better for you.
Tor Browser 8.0, our first stable release based on Firefox 60 ESR, is now available from the Tor Browser Project page and also from our distribution directory. This release is all about users first.
Tor Browser 8.0 comes with a series of user experience improvements that address a set of long-term Tor Browser issues you’ve told us about. To meet our users' needs, Tor Browser has a new user onboarding experience; an updated landing page that follows our styleguide; additional language support; and new behaviors for bridge fetching, displaying a circuit, and visiting .onion sites.
New User Onboarding
For the most part, using Tor is like using any other browser (and it is based on Firefox), but there are some usage differences and cool things happening behind the scenes that users should be aware of. Our new onboarding experience aims to better let you know about unique aspects of Tor Browser and how to maximize those for your best browsing experience.
Improved Bridge Fetching
For users where Tor is blocked, we have previously offered a handful of bridges in the browser to bypass censorship. But to receive additional bridges, you had to send an email or visit a website, which posed a set of problems. To simplify how you request bridges, we now have a new bridge configuration flow when you when you launch Tor. Now all you have to do is solve a captcha in Tor Launcher, and you’ll get a bridge IP. We hope this simplification will allow more people to bypass censorship and browse the internet freely and privately.
Better Language Support
Millions of people around the world use Tor, but not everyone has been able to use Tor in their language. In Tor Browser 8, we’ve added resources and support for nine previously unsupported languages: Catalan, Irish, Indonesian, Icelandic, Norwegian, Danish, Hebrew, Swedish, and Traditional Chinese.
Apart from those highlights, a number of other component and toolchains got an update for this major release. In particular, we now ship Tor 0.3.3.9 with OpenSSL 1.0.2p and Libevent 2.1.8. Moreover, we switched to the pure WebExtension version of NoScript (version 10.1.9.1) which we still need to provide the security slider functionality. Additionally, we start shipping 64bit builds for Windows users which should enhance Tor Browser stability compared to the 32bit bundles.
Providing this many improvements for our users could only be possible with collaboration between the Tor Browser team and Tor's UX team, Community team, Services Admin team, and our volunteers. We would like to thank everyone for working hard over the past year to bring all these new features to our users.
Known Issues
We already collected a number of unresolved bugs since Tor Browser 7.5.6 and tagged them with our ff60-esr keyword to keep them on our radar. The most important ones are listed below:
- WebGL is broken right now.
- We disable Stylo on macOS due to reproducibility issues we need to investigate and fix. This will likely not get fixed for Tor Browser 8, as we need some baking time on our nightly/alpha channel before we are sure there are no reproducibility/stability regressions. The tentative plan is to get it ready for Tor Browser 8.5.
Note: This release is signed with a new GPG subkey as the old one expired a couple of days ago. You might need to refresh your copy of the public part of the Tor Browser signing key before doing the verification. The fingerprint of the new subkey is 1107 75B5 D101 FB36 BC6C 911B EB77 4491 D9FF 06E2.
Give Feedback
This is only the beginning of our efforts to put users first. If you find a bug or have a suggestion for how we could improve this release, please let us know.
Changelog
The full changelog since Tor Browser 7.5.6 is:
- All platforms
- Update Firefox to 60.2.0esr
- Update Tor to 0.3.3.9
- Update OpenSSL to 1.0.2p
- Update Libevent to 2.1.8
- Update Torbutton to 2.0.6
- Bug 26960: Implement new about:tor start page
- Bug 26961: Implement new user onboarding
- Bug 26962: Circuit display onboarding
- Bug 27301: Improve about:tor behavior and appearance
- Bug 27214: Improve the onboarding text
- Bug 26321: Move 'New Identity', 'New Circuit' to File, hamburger menus
- Bug 26100: Adapt Torbutton to Firefox 60 ESR
- Bug 26520: Fix sec slider/NoScript for TOR_SKIP_LAUNCH=1
- Bug 27401: Start listening for NoScript before it loads
- Bug 26430: New Torbutton icon
- Bug 24309: Move circuit display to the identity popup
- Bug 26884: Use Torbutton to provide security slider on mobile
- Bug 26128: Adapt security slider to the WebExtensions version of NoScript
- Bug 27276: Adapt to new NoScript messaging protocol
- Bug 23247: Show security state of .onions
- Bug 26129: Show our about:tor page on startup
- Bug 26235: Hide new unusable items from help menu
- Bug 26058: Remove workaround for hiding 'sign in to sync' button
- Bug 26590: Use new svg.disabled pref in security slider
- Bug 26655: Adjust color and size of onion button
- Bug 26500: Reposition circuit display relay icon for RTL locales
- Bug 26409: Remove spoofed locale implementation
- Bug 26189: Remove content-policy.js
- Bug 26544: Images are not centered anymore
- Bug 26490: Remove the security slider notification
- Bug 25126: Make about:tor layout responsive
- Bug 27097: Add text for Tor News signup widget
- Bug 21245: Add da translation to Torbutton and keep track of it
- Bug 27129+20628: Add locales ca, ga, id, is, nb, da, he, sv, and zh-TW
- Translations update
- Update Tor Launcher to 0.2.16.3
- Bug 23136: Moat integration (fetch bridges for the user)
- Bug 25750: Update Tor Launcher to make it compatible with Firefox 60 ESR
- Bug 26985: Help button icons missing
- Bug 25509: Improve the proxy help text
- Bug 26466: Remove sv-SE from tracking for releases
- Bug 27129+20628: Add locales ca, ga, id, is, nb, da, he, sv, and zh-TW
- Translations update
- Update HTTPS Everywhere to 2018.8.22
- Update NoScript to 10.1.9.1
- Update meek to 0.31
- Bug 26477: Make meek extension compatible with ESR 60
- Update obfs4proxy to v0.0.7 (bug 25356)
- Bug 27082: Enable a limited UITour for user onboarding
- Bug 26961: New user onboarding
- Bug 26962: New feature onboarding
- Bug 27403: The onboarding bubble is not always displayed
- Bug 27283: Fix first-party isolation for UI tour
- Bug 27213: Update about:tbupdate to new (about:tor) layout
- Bug 14952+24553: Enable HTTP2 and AltSvc
- Bug 25735: Tor Browser stalls while loading Facebook login page
- Bug 17252: Enable TLS session identifiers with first-party isolation
- Bug 26353: Prevent speculative connects that violate first-party isolation
- Bug 26670: Make canvas permission prompt respect first-party isolation
- Bug 24056: Use en-US strings in HTML forms if locale is spoofed to english
- Bug 26456: HTTP .onion sites inherit previous page's certificate information
- Bug 26561: .onion images are not displayed
- Bug 26321: Move 'New Identity', 'New Circuit' to File, hamburger menus
- Bug 26833: Backport Mozilla's bug 1473247
- Bug 26628: Backport Mozilla's bug 1470156
- Bug 26237: Clean up toolbar for ESR60-based Tor Browser
- Bug 26519: Avoid Firefox icons in ESR60
- Bug 26039: Load our preferences that modify extensions (fixup)
- Bug 26515: Update Tor Browser blog post URLs
- Bug 26216: Fix broken MAR file generation
- Bug 26409: Remove spoofed locale implementation
- Bug 25543: Rebase Tor Browser patches for ESR60
- Bug 23247: Show security state of .onions
- Bug 26039: Load our preferences that modify extensions
- Bug 17965: Isolate HPKP and HSTS to URL bar domain
- Bug 21787: Spoof en-US for date picker
- Bug 21607: Disable WebVR for now until it is properly audited
- Bug 21549: Disable wasm for now until it is properly audited
- Bug 26614: Disable Web Authentication API until it is properly audited
- Bug 27281: Enable Reader View mode again
- Bug 26114: Don't expose navigator.mozAddonManager to websites
- Bug 21850: Update about:tbupdate handling for e10s
- Bug 26048: Fix potentially confusing "restart to update" message
- Bug 27221: Purge startup cache if Tor Browser version changed
- Bug 26049: Reduce delay for showing update prompt to 1 hour
- Bug 26365: Add potential AltSvc support
- Bug 9145: Fix broken hardware acceleration on Windows and enable it
- Bug 26045: Add new MAR signing keys
- Bug 25215: Revert bug 18619 (we are not disabling IndexedDB any longer)
- Bug 19910: Rip out optimistic data socks handshake variant (#3875)
- Bug 22564: Hide Firefox Sync
- Bug 25090: Disable updater telemetry
- Bug 26127: Make sure Torbutton and Tor Launcher are not treated as legacy extensions
- Bug 13575: Disable randomised Firefox HTTP cache decay user tests
- Bug 22548: Firefox downgrades VP9 videos to VP8 for some users
- Bug 24995: Include git hash in tor --version
- Bug 27268+27257+27262+26603 : Preferences clean-up
- Bug 26073: Migrate general.useragent.locale to intl.locale.requested
- Bug 27129+20628: Make Tor Browser available in ca, ga, id, is, nb, da, he, sv, and zh-TW
- Windows
- Bug 20636+10026: Create 64bit Tor Browser for Windows
- Bug 26381: Work around endless loop during page load and about:tor not loading
- Bug 27411: Fix broken security slider and NoScript interaction on Windows
- Bug 22581: Fix shutdown crash
- Bug 25266: PT config should include full names of executable files
- Bug 26304: Update zlib to version 1.2.11
- Update tbb-windows-installer to 0.4
- Bug 26355: Update tbb-windows-installer to check for Windows7+
- Bug 26355: Require Windows7+ for updates to Tor Browser 8
- OS X
- Bug 24136: After loading file:// URLs clicking on links is broken on OS X
- Bug 24243: Tor Browser only renders HTML for local pages via file://
- Bug 24263: Tor Browser does not run extension scripts if loaded via about:debugging
- Bug 22794: Don't open AF_INET/AF_INET6 sockets when AF_LOCAL is configured
- Linux
- Bug 22794: Don't open AF_INET/AF_INET6 sockets when AF_LOCAL is configured
- Bug 25485: Unbreak Tor Browser on systems with newer libstdc++
- Bug 20866: Fix OpenGL software rendering on systems with newer libstdc++
- Bug 26951+18022: Fix execdesktop argument passing
- Bug 24136: After loading file:// URLs clicking on links is broken on Linux
- Bug 24243: Tor Browser only renders HTML for local pages via file://
- Bug 24263: Tor Browser does not run extension scripts if loaded via about:debugging
- Bug 20283: Tor Browser should run without a `/proc` filesystem.
- Bug 26354: Set SSE2 support as minimal requirement for Tor Browser 8
- Build System
- All
- Bug 26362+26410: Use old MAR format for first ESR60-based stable
- Bug 27020: RBM build fails with runc version 1.0.1
- Bug 26949: Use GitHub repository for STIX
- Bug 26773: Add --verbose to the ./mach build flag for firefox
- Bug 26319: Don't package up Tor Browser in the `mach package` step
- Bug 27178: add support for xz compression in mar files
- Clean up
- Windows
- Bug 26203: Adapt tor-browser-build/tor-browser for Windows
- Bug 26204: Bundle d3dcompiler_47.dll for Tor Browser 8
- Bug 26205: Don't build the uninstaller for Windows during Firefox compilation
- Bug 26206: Ship pthread related dll where needed
- Bug 26396: Build libwinpthread reproducible
- Bug 25837: Integrate fxc2 into our build setup for Windows builds
- Bug 27152: Use mozilla/fxc2.git for the fxc2 repository
- Bug 25894: Get a rust cross-compiler for Windows
- Bug 25554: Bump mingw-w64 version for ESR 60
- Bug 23561: Fix nsis builds for Windows 64
- Bug 13469: Windows installer is missing many languages from NSIS file
- Bug 23231: Remove our STL Wrappers workaround for Windows 64bit
- Bug 26370: Don't copy msvcr100.dll and libssp-0.dll twice
- Bug 26476: Work around Tor Browser crashes due to fix for bug 1467041
- Bug 18287: Use SHA-2 signature for Tor Browser setup executables
- Bug 25420: Update GCC to 6.4.0
- Bug 16472: Update Binutils to 2.26.1
- Bug 20302: Fix FTE compilation for Windows with GCC 6.4.0
- Bug 25111: Don't compile Yasm on our own anymore for Windows Tor Browser
- Bug 18691: Switch Windows builds from precise to jessie
- OS X
- Bug 24632: Update macOS toolchain for ESR 60
- Bug 9711: Build our own cctools for macOS cross-compilation
- Bug 25548: Update macOS SDK for Tor Browser builds to 10.11
- Bug 26003: Clean up our mozconfig-osx-x86_64 file
- Bug 26195: Use new cctools in our macosx-toolchain project
- Bug 25975: Get a rust cross-compiler for macOS
- Bug 26475: Disable Stylo to make macOS build reproducible
- Bug 26489: Fix .app directory name in tools/dmg2mar
- Linux
- All
Comments
Please note that the comment area below has been archived.
I know the User-Agent…
I know the User-Agent spoofing is imperfect, but an imperfect mask is better than no mask! The actual OS in the User-Agent string will only further distinguish and deanonymize the user-base.
Otherwise thanks for your work!
I'm glad the first comment…
I'm glad the first comment notes about the UA change, which is actually a privacy *regression* since for users with JS disabled the real OS will be leaked vs. the situation in the previous Tor releases (7.x). Also not everyone does JS based OS detection (only a few do it) but *most* do log the UA. One can imagine that the UA is all it takes to correlate between two users with similar traits in a low volume site (example writing patterns, social graph, ...) [and even a high volume one like Twitter with some more work].
Please Tor Browser devs fix this issue since it's really the only bad thing in an otherwise almost perfect stable release.
Here's a real life example:…
Here's a real life example: Leaker 1 uses securedrop to send a leak from an organization A where he work and his Mac user agent leaks. Organization A finds everyone has access to the leaked docs and finds the ones who have a Mac. Depending on the situation they may actually narrow it down to a few people or just one, all because the browser doesn't even try to spoof the OS.
Hi, Agree. In addition: not…
Hi,
Agree.
In addition: not masking the UA also has big usability implications on sites that mistakenly or over-cautiously believe they only supports Windows, MAC, iOS and Android. On *many* such sites a TorBrowser that pretends it is running on Windows works just fine. If you reveal another rare OS in the UA the site says that it only support iOS and Android or other such nonsense. They just do not know that Firefox on a rare OS is a Firefox.
If one is to enter a fake UA in TorBrowser 8.0 so that the site accepts one as running on a popular Windows OS, which string should one currently use?
Thanx for the great work!
The string value in general…
The string value in general.useragent.override has no effect in TBB 8.0, so the hard coded value is revealed.
I just checked my UserAgent…
I just checked my UserAgent and it seems fine, the current one is:
Mozilla/5.0 (Windows NT 6.1; rv:60.0) Gecko/20100101 Firefox/60.0
Back in version 7.5.6 it was:
Mozilla/5.0 (Windows NT 6.1; rv:52.0) Gecko/20100101 Firefox/52.0
I believe it shows your system as being Windows NT 6.1 regardless of what system you're using. Correct me if I am wrong.
Unfortunately, it shows the…
Unfortunately, it shows the actual OS in the user-agent string.
does hiding the title bar…
does hiding the title bar under Appearances affect anonymity?
No, but changing the density…
No, but changing the density will.
Happy to finally see a TAILS…
Happy to finally see a TAILS announcement on the Blog!
However, unlike most other entries, I notice the TAILS announcements here are not open for comments. Why not? What a shame.
Congrats on Tor Browser 8.0! Thanks for posting the changelog here. <3
> I notice the TAILS…
> I notice the TAILS announcements here are not open for comments.
Yes.
> Why not?
Speculation:
1. Years ago, Tails, which is mostly based in Western Europe, had its own blog. But Tails Project is a small org and over time the blog became too hard to moderate. It was discontinued when some posters tried to describe specific abuses by intelligence agencies of Western Europe and USA. (Later confirmed in all respects by the Snowden leaks.)
2. Tails Project is separate from Tor Project, although closely allied, and for security reasons it may be best not to try to have them respond to comments on their posts here, whereas for clarity it is clearly best that Tor Project people not try to respond to questions asking about Tails.
> What a shame
Yes.
But compared to USG attempts to "kill" (their word) UNCHR and ICC (and maybe also Riseup, Boum, Tails Project, Tor Project, HRW, Amnesty, RSF, CPJ, ACLU, EFF...) "by any means necessary" (thus the reliably revolting John Bolton), this is a minor issue.
After applying the update to…
After applying the update to version 8, the browser will not start anymore...
I was more or less expecting this could happen (same problem with an alpha version; don't remember witch one), so I made a backup of the last version 7.
It is of course unsafe to continue using that one...
System:
Linux Mint 17.3, 64bit
16GB RAM
Kernel 4.4.0.134
What happens when you…
What happens when you restart the browser? Do you have some error message?
Does it work if you download a new Tor Browser 8.0 tarball?
I restarted when prompted,…
I restarted when prompted, and nothing happened after that, not even an error message.
I tried with a new tarball (tor-browser-linux64-8.0_nl.tar.xz); clicked on the setup icon and that changed into an icon named "tor browser" that looked like a sheet of paper...
Clicking on that one did nothing at all.
Short answer: You need to…
Short answer: You need to install "libgtk3". Please ask in a Mint forum for exact package name and how to install it.
Long answer: I had the same issue on a different Linux distribution. Starting the embedded Firefox browser manually, I got this error message:
After installing the package that offers the
libgtk-3.so.0file, Tor browser worked as expected.I actually have libgtk-3-0 …
I actually have libgtk-3-0 (3.10.8-0ubuntu1.6) installed...
Could it be that I have a wrong version of libstdc (libstdc++.so.6.0.24)?
(See my other reply, that is still awaiting moderation)
You need to install libgtk-3
You need to install libgtk-3
[Edit] Opening a terminal in…
[Edit]
Opening a terminal in the "Browser" directory and give the command:
./start-tor-browser --verbosethrows this error:
./firefox.real: relocation error: ./firefox.real: symbol _ZTTNSt7__cxx1119basic_ostringstreamIcSt11char_traitsIcESaIcEEE, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time referenceHm. Could you make sure you…
Hm. Could you make sure you install the Tor Browser to a new location and try again starting it? Do you get the same error message?
I have the exact same error…
I have the exact same error.
OS: Mint 17.3 rosa
Kernel: x86_64 Linux 4.4.0-131-generic
Worked for me in ubuntu 14…
Worked for me in ubuntu 14.
1 open file /Browser/firefox
2 comment line 10,12( if and fi) to use custom libstdc++
#if [ $? -ne 0 ]; then
LD_LIBRARY_PATH="$LD_LIBRARY_PATH:$basedir/TorBrowser/Tor/libstdc++/"
#fi
All should work.
I tested the update from 7.5…
I tested the update from 7.5.6 on Ubuntu 14.04 and it worked fine. Are you saying you hit the same issue as the reporter on Ubuntu 14.04?
Yes, on Ubuntu 14.04.5 LTS…
Yes, on Ubuntu 14.04.5 LTS same problem.
The problem is in reloc functions. To check use this:
$ ldd -r firefox.real
linux-vdso.so.1 => (0x00007ffe30ffb000)
libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007fb7454bb000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007fb7452b7000)
librt.so.1 => /lib/x86_64-linux-gnu/librt.so.1 (0x00007fb7450af000)
libstdc++.so.6 => /usr/lib/x86_64-linux-gnu/libstdc++.so.6 (0x00007fb744d9b000)
libm.so.6 => /lib/x86_64-linux-gnu/libm.so.6 (0x00007fb744a95000)
libgcc_s.so.1 => /lib/x86_64-linux-gnu/libgcc_s.so.1 (0x00007fb74487e000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fb7444b4000)
/lib64/ld-linux-x86-64.so.2 (0x0000560938ac7000)
symbol _ZTTNSt7__cxx1119basic_ostringstreamIcSt11char_traitsIcESaIcEEE, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZTVNSt7__cxx1119basic_ostringstreamIcSt11char_traitsIcESaIcEEE, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZTVNSt7__cxx1115basic_stringbufIcSt11char_traitsIcESaIcEEE, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE9_M_createERmm, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE9_M_assignERKS4_, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE9_M_mutateEmmPKcm, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE9_M_appendEPKcm, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZNSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE9push_backEc, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
symbol _ZNKSt7__cxx1112basic_stringIcSt11char_traitsIcESaIcEE4copyEPcmm, version GLIBCXX_3.4.21 not defined in file libstdc++.so.6 with link time reference (./firefox.real)
Thanks. I've opened https:/…
Thanks. I've opened https://trac.torproject.org/projects/tor/ticket/27508 and we are investigating the problem.
Thanks! That did the trick. …
Thanks!
That did the trick.
I hope this will be fixed in the next version.
how exactly do you edit…
how exactly do you edit binary file?
firefox is just a shell…
firefoxis just a shell script, the binary file isfirefox.real.Would it be possible for you…
Would it be possible for you to paste the output of
./Browser/abicheck? Thanks.I presume you asked me? The…
I presume you asked me?
The layout of this blog makes it rather difficult to see...
The output is :
This is the same with or without the unofficial patch of the "firefox" shell script.
> This is the same with or…
This part is especially helpful, thanks. We will continue to debug in #27508.
I have the same problem with…
I have the same problem with Mint 17 (uncommenting those lines solved it). Abicheck says:
Exception thrown
~Foo() called during stack unwinding
Exception caught: test exception
~Foo() called normally
<br />$ ./abicheck<br /…
Questions: 1. NoScript on…
Questions:
1. NoScript on Tor Browser 7.5.6 can block javascript (and other resources) in "file:" URLs. Can NoScript in Tor Browser 8 do that as well?
2. On Firefox, NoScript 10 treats some Mozilla-owned domains as "privileged" and is unable to disable javascript (or other resources) in those URLs. Firefox ESR 52 and Tor Browser 7.5.6 do not have that problem. What's the status in Tor Browser 8? See "src/noscript/upstream/src/lib/restricted.js" in NoScript's source tree and https://bugzilla.mozilla.org/show_bug.cgi?id=1415644.
3. This is an important regression in Firefox ESR 60: https://bugzilla.mozilla.org/show_bug.cgi?id=1487856. What's the status in Tor Browser 8?
2. On Firefox, NoScript 10…
I only went through the bug report superficially but isn't Firefox Account disabled in Tor Browser and thus this doesn't apply?
Nevertheless, I guess it should be made harder to install extension. The FAQ already states that extensions should not be installed but I doubt many read that.
3. This is an important regression in Firefox ESR 60: https://bugzilla.mozilla.org/show_bug.cgi?id=1487856. What's the status in Tor Browser 8?
Looking at the bug report, I don't understand how that's an issue for Tor Browser. Perhaps I just don't get the connection somehow. Does this introduce a privacy or security issue or something like that?
I only went through the bug…
You're missing the point, which was clearly stated:
It is an important usability issue, especially for those who disable javascript.
You're missing the point,…
You're missing the point, which was clearly stated:
...NoScript 10 treats some Mozilla-owned domains as "privileged" and is unable to disable javascript (or other resources) in those URLs.
Guess I got a bit distracted by the bug report you linked. Just to clarify, you talking about an arbitrary page being able to execute any JavaScript hosted on these domains, right? I definitely see how that could be an issue.
I recommend you open a ticket on https://ticket.torproject.org (if there is none yet) to have this looked into.
Does this introduce a privacy or security issue or something like that?
It is an important usability issue, especially for those who disable javascript
I see, opening a ticket would seem the right way to go then. Perhaps you could add an example in the ticket that shows how this bug in combination with JS being disabled leads to an unusable page. In my experience bug reports that clearly show that they are a real-world issue are fixed faster.
Answer to 1: Yes (at least…
Answer to 1: Yes (at least it blocked for me media files loaded via file:///, I'd assume it would be the same for HTML file:///).
Answer to 1: No, NoScript…
Answer to 1: No, NoScript doesn't block JS in file:///
And NoScript in TBB7.5.6 has…
And NoScript in TBB7.5.6 has had a ....very strange bug, can't block JSON .Bug was sold from zerodium to governments. *WTF*
It's good to have stong nerves and don't believe in conspiracy theories(-:
Answer to 2): That's fixed…
Answer to 2): That's fixed in Tor Browser by https://trac.torproject.org/projects/tor/ticket/26114.
Answer to 3): It's not fixed.
Thank you. Could you say…
Thank you. Could you say something about 1 too?
thank for this huge update!…
thank for this huge update! but how can you see your entry/exit node (IP). before update it was tor button, but now...?
Click the ! Point next to…
Click the ! Point next to the URL bar. ?
We'll need to click the …
We'll need to click the "Show site information" icon in the address bar.
Tor plus Quantum is working…
Tor plus Quantum is working perfectly well ! Bravo !
haven't checked on a non…
haven't checked on a non-Linux OS, but the user agent reported by this new Tor Browser is actually Linux, and not Windows, as on previous versions. Is this intended?
https://trac.torproject.org…
https://trac.torproject.org/projects/tor/ticket/26146
This isn't really intended…
This isn't really intended but known. See ticket 26146 for details.
There are still many open issues with higher priority related to the Firefox 60 upgrade. Thus, figuring out how to deal with this is likely going to take some time.
So why releasing now? It's…
So why releasing now? It's months late anyway. If security vulnerabilities were the concern it should have gone out together with ESR 60,
Have ESR 52 vulnerabilities been observed being exploited in the wild now?
ESR52 was still supported,…
ESR52 was still supported, until now.
Mozilla still backported all…
Mozilla still backported all security fixes to 52 ESR until now. As of the most recent release (60.2.0 on 2018-09-04) this is no longer the case. Thus, Firefox 60 ESR now contains bugfixes for security issues that won't be fixed in 52 ESR and since the fixes have been released the security vulnerabilities are now known publicly making 52 ESR an easy target.
Yes.
Yes.
I don't want to tell every…
I don't want to tell every website "Hey, look at me, I'm using OS with ~2% market share!", even with disabled JS while using TBB. What I should do? Why you so hate Linux users and make them 30 times more unique than Windows users?
Couldn't agree with you more…
Couldn't agree with you more. What a stupid mistake of TorProject. User Agent/operating system should be spoofed. Even with javascript totally disabled, Tor Browser still shows "linux64". What a mistake to make.
Hello Tor developers. Can u…
Hello Tor developers. Can u please fix the "bookmarks not showing" problem? Thank you in advance.
For someone wondering what…
For someone wondering what it is: https://trac.torproject.org/projects/tor/ticket/27264. Patches are welcome!
In the Tor Browser 8.0…
In the Tor Browser 8.0 customize panel, select the "⭑ Bookmarks Toolbar Items" icon and drag/drop it into the horizontal bookmarks toolbar space near the top of the customize panel.
The bookmark bar is not…
The bookmark bar is not working. It's blank and dragging bookmarks to it only gives you a cross symbol. The bookmark bar is broke. Never had an issue with it before this version.
If you right click the menu…
If you right click the menu bar and check the "Bookmark tool bar", no, not the way.
Amazing, was waiting for…
Amazing, was waiting for this ^w^!
how can I see my tor network…
how can I see my tor network circuite (entry/exit node) it is no more by clicking on tor button... thanks
Yeah i want to see that too…
Yeah i want to see that too...
tor network circuite (entry…
tor network circuite (entry/exit node) now see in the green padlock in the url bar
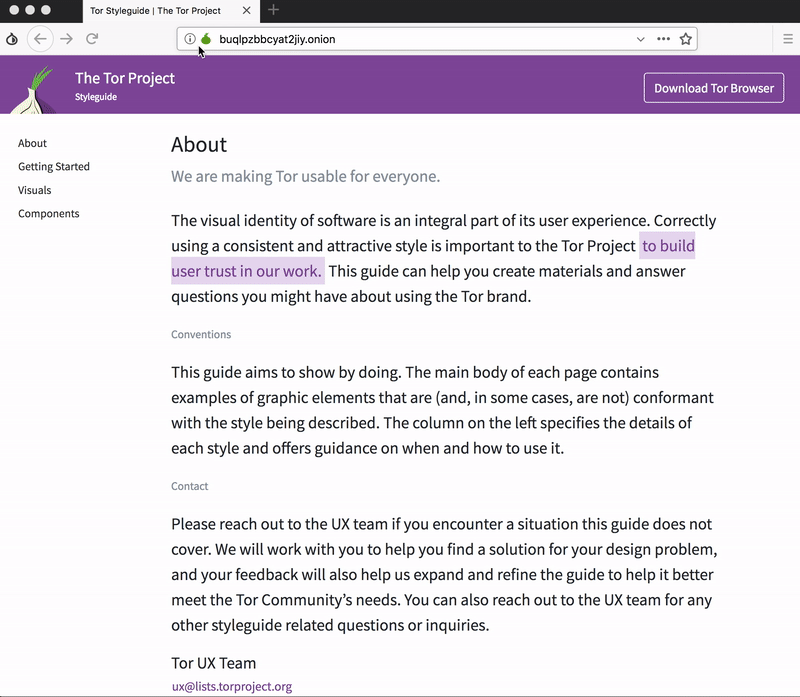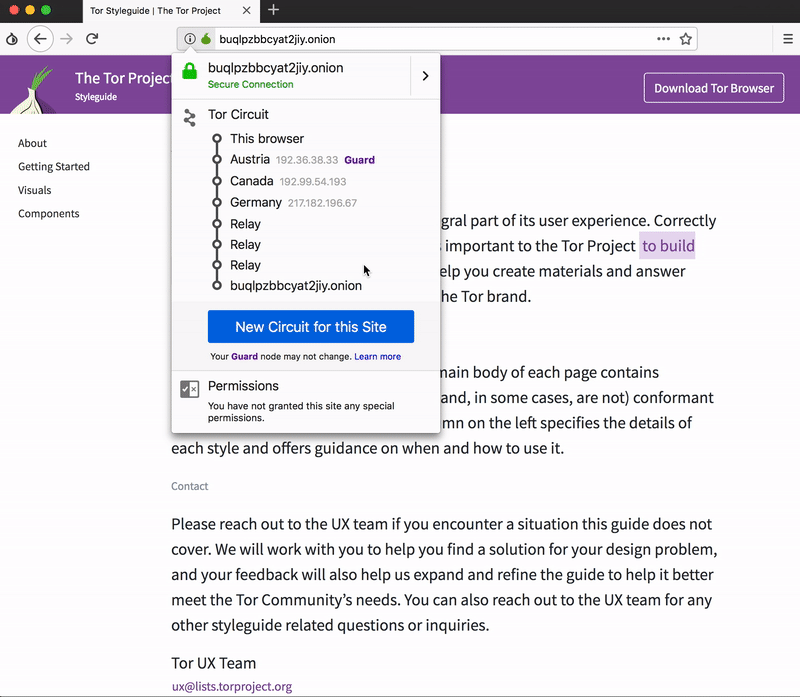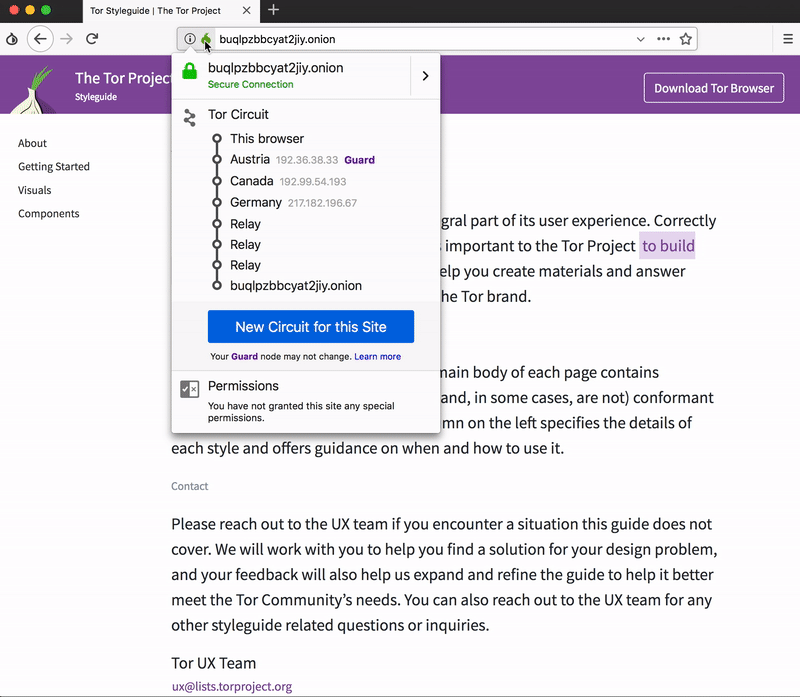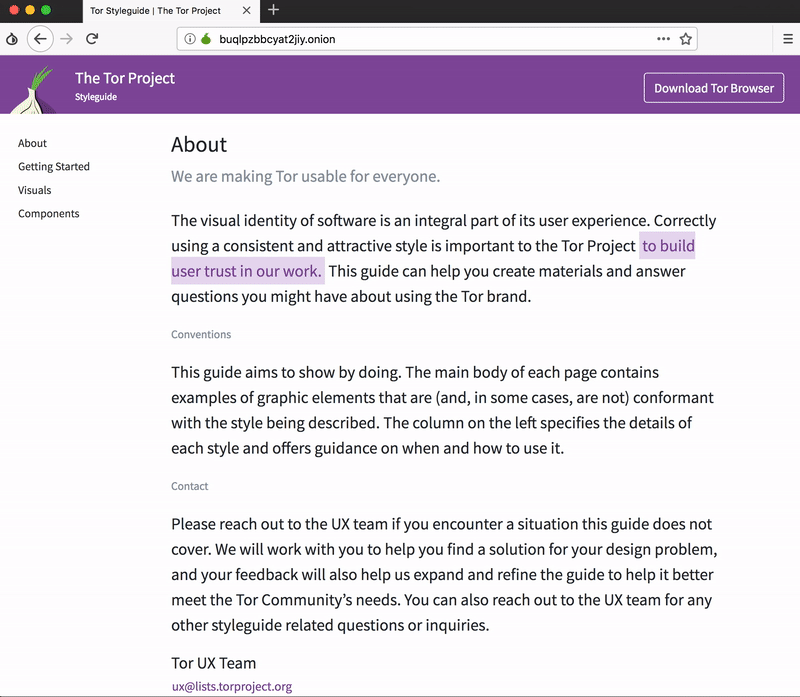
Second screencast in this…
Second screencast in this blog shows where the Circuit Display is placed now.
Tor browser 8.0 is …
Tor browser 8.0 is unavailable for Nvda[screen reader] in windows system. Please fix it.
Previous version works fine.
Blind users they can not use this version.
Yes, we had to disable…
Yes, we had to disable accessibility support on Windows system, alas. :( The problem is that mingw-w64 lacks some fixes which are probably not so easy to write. We have a bug open for now with further links to the underlying problem: https://trac.torproject.org/projects/tor/ticket/27503.
Thank you for your answer…
Thank you for your answer. How long does it take to fix this problem?
At once I can not use it tbb.
We don't know yet. :(
We don't know yet. :(
The debian package…
The debian package torbrowser-launcher ships an apparmor profile which is incompatible with this version. It prevents the browser to launch because ./firefox is not allowed to access /usr/bin/dirname or ./firefox.real.
Also i think that the window size is not standardized as before (window.geometry says it's 712x900), but it could be a problem with my window manager
I see a debian bug has been…
I see a debian bug has been opened for this issue:
https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=908068
Same issues as Tor 7. OBS4…
Same issues as Tor 7.
OBS4 sits idle at establishing encrypted connection, all the time... no matter how long you wait?
FTE still does not work. Missing pluggable transport error?
Same as version 7...only OBS3 transport works.
Is there a SIMPLE way that Tor can be configured besides the default download?
Aren't there other transports that you can add to Tor that aren't default???
This browser has not worked well, or very incompletely since around 7.5.
Never ending Cloudfare issues since version 4 of Tor?
Please advise.
The usability and constant blocking of this browser is reaching a point to where I'm ready to switch to a new browser. I've also donated quite a bit of money for about 7 years now which these issues should not continue to deteriorate the browser as it ages. It should be better, not trending in reverse.
Does meek work for you? In…
Does meek work for you? In case you are living/using Tor in a censored environment it can be that the default obfs4 bridges get blocked. Try getting fresh ones with our new Moat feature (see the above introduction in the blog post).
That said, yes, the censorship arms race is tricky. We need better strategies and newer pluggable transports. We are working on that but it is no easy task. If you are using Linux or macOS you could try the alpha series and check whether the snowflake pluggable transport is working for you.
where is the circuite info…
where is the circuite info and reconnect option? so the version 8 feels unsecure, switch back to 7 till things get fixed.
As the onboarding, this blog…
As the onboarding, this blog post and a note during the update shows that moved to the identity box (the lock icon) in the URL bar. Once you open a website, click on it and you'll see the circuit and the option to get a new one.
For those of us who aren't…
For those of us who aren't techies, better to upgrade now or wait?
This new version is fixing…
This new version is fixing some security issues, so you should upgrade.
Bookmark bar does not work…
Bookmark bar does not work.
https://imgur.com/wjSsY5A
Windows 7 Thin PC x86
See: https://trac.torproject…
See: https://trac.torproject.org/projects/tor/ticket/27264 and the first comment for a workaround.
This is not good. I can not…
This is not good. I can not access some sites
Could you give me an example?
Could you give me an example?
Any chance we could get an…
Any chance we could get an option to revert to the old UI and retain the grannular control we had in previous versions of noscript?
No. That version of NoScript…
No. That version of NoScript is not working in ESR 60 anymore.
Looks like DuckDuckGo…
Looks like DuckDuckGo searches doesn't work if Tor Browser Security Settings is set to Safest. Trisquel 7 Belenos x86 BTW.
Indeed, thanks for reporting…
Indeed, thanks for reporting. I opened https://trac.torproject.org/projects/tor/ticket/27507.
https://superuser.com…
https://superuser.com/questions/732513/get-duckduckgo-non-javascript-ve…
this condition isn't new. I added the nojs ddg years ago.
you can add custom search engines. in any ff
1.) delete search.json.mozlz4
2.) ff regenerates search.json.mozlz4 based on your xml in searchplugins folder
the above is true as of esr 52. Did quantum broke the workaround?
replying here, because no form for logged-in cypherpunks on trac.
So that's the end of Tor…
So that's the end of Tor Browser on XP now.... R.I.P. my beloved XP. ;-(
For TOR team, to throw XP…
For TOR team, to throw XP users overboard is not the best decision.
I regret it very much. I can't afford myself to upgrade my XP to any higher release, since (i) my hardware shall not bear newer OS and, (ii) I have a lot of 'old good' software which shall not run even at Windows 7.
So the only choice which remains for me is to wait patiently until TOR shall change its upgrade policy, considering the demands of old people running XP on older HW. I shall not change my operational system -> I shall not upgrade TOR from the current 7.5.6 release, and the last thing remaining for me is to find out, how to switch off all the automatic upgrades to TOR
Unusable! It's a shame!…
Unusable! It's a shame! Until now TB always worked fine.
Oh, same problem reported by…
Oh, same problem reported by Nico, anyway. Nevertheless, thank you for your job.
New version sucks, why are…
New version sucks, why are bookmarks hidden that you need to spend time to search for them6
Maybe that's https://trac…
Maybe that's https://trac.torproject.org/projects/tor/ticket/27264? (see comment:1 for a workaround).
How does TB interact with…
How does TB interact with the container feature?
It uses a partially related…
It uses a partially related one "OriginAttributes" to provide the first-party isolation we need for preventing user tracking.
So can I use, if I install…
So can I use, if I install the extension, the containers or are they disabled?
Tor Browser should not mess…
Tor Browser should not mess with that feature.
It is utterly ridiculous…
It is utterly ridiculous that you've decided to expose your users' OSes in their user agents. As has been pointed out previously, alternative OS detection methods only work with JS on, and some obfuscation is still better than none. Instead of decreasing your users' OS privacy, how about you try to fix any lingering OS fingerprinting issues while leaving the protections that are already there in place?
Coupled with your longstanding insistence on leaving JS on by default and constantly simplifying and "streamlining" Tor to make it more and more difficult for intelligent people who understand its design to use it properly, I am seriously beginning to wonder if the Tor team hasn't been compromised by people who want its users to be exploited. Leave JS on by default and now make sure to expose their OS easily and transparently so that any nefarious actors know exactly which version of which obscure memory exploit and so on to use against them. It's highly suspicious.
Given this issue, I'm seriously wondering what other insanity is lurking in the design of this Tor Browser version and if I should even update.
Can anyone post the Windows UA of Tor Browser 8.0?
Thanks for your post. I'm…
Thanks for your post. I'm afraid I get the same feeling about someone or a group trying to undermine the tor project. I have read similar voices as yours on other message boards. I hope there are honest developers left at the tor project. Something is odd.
My virus program doesn't…
My virus program doesn't like your new Tor Update, it gave me a restart the computer. I believe it said xui. was the treat, I restarted the computer Trend Micro had removed Tor Browser. I haven't had this happen before. I reinstalled Tor it seems to be okay. I am using it now. Why would Tor Update scare my virus protection so badly? What is this xui? Why is it a serious virus warning from my virus protection?
How can I enable flash?…
How can I enable flash? please spare me the flash is bad sermon. In the past there used to be a preference option to distinguish tor browser from other users. I can't find this option in this version, what's it about:config value?
privacy.resistFingerprinting…
privacy.resistFingerprinting
privacy.resistFingerprinting.block_mozAddonManager
It worked! Thanks.
It worked! Thanks.
On Mac 10.9.5 today's update…
On MacOS 10.9.5 today's update gets me a crashed Tor browser upon startup every time. I had to revert to the previous version.
This is probably this bug…
This is probably this bug:
https://trac.torproject.org/projects/tor/ticket/27482
You can use the alpha version 8.5a1, until this is fixed in 8.0.1.
Automatic update just…
Automatic update just updated to this version.
With all the updated features, it looks like alot of heart and soul was put into a major remodeling. The added features are kind of cool.
but...
You can no longer can see circuits you are on :(. Vidalia was the most perfect expression of this, and since it was taken away, at least we could see the circuits. Now we see nothing. Threre are times I do not want a certain country code or tor node in the circuit (i.e. Liberia, Nigeria, Ukraine) and when so, I reset it. Until now.
You can no longer change fingerprint from the onion dropdown :(. I have to restart Tor for that now.
I tried the alpha version before this release and ran back to the 7.56 for the reasons above and because of update issues. Please stop taking away useful functionality when adding new stuff and bring the circuit view and change fingerprint back if only as selectable options.
Hej Ranger, couldn't say it…
Hej Ranger,
couldn't say it any better.
I also stepped back to 7.56 because of the missing visibility of circuits and possibility of resetting it.
I absolutely agree.
Yes, you can see your…
Yes, you can see your circuits and get a new Tor circuit for a website. As the blog post, the note after the update and the new user onboarding says: it moved to the "identity box" in the URL bar (the "lock" icon). That way it fits much better into the toolbar as it is making site-specific options available for the particular site you currently have open.
Well be that way then.... :…
Well be that way then.... :).
Thanks for the clarification on where and how that can now be done. That will work okay.
so first firefox fuzzing up…
so first firefox fuzzing up all there extensions with quantum. and now you are doing the same. al my fucking extensions has become legacy. sigh im so sick and tired of this shiz
No more updates on XP and…
No more updates on XP and Vista? Are you serious?? Do you know how many people will no longer be able to use Tor at work since many businesses, including government/military/banks, STILL use XP and Vista?? Is there any way to fix this??
No, Firefox cut out all XP…
No, Firefox cut out all XP and Vista support with Firefox 60 ESR.
Will Tor still conceal my IP…
Will Tor still conceal my IP even if I continue using TBB 7.5.6 on Windows Vista? Vista is what my job uses still and concealing my IP is what I'm more concerned about now until I can think of what to do next.
Tor working in Tor Browser 7…
Tor working in Tor Browser 7.5.6 should still be working as expected. The risk here is that both Firefox and Vista (now) contain known security vulnerabilities that don't get fixed and which probably allow to bypass Tor's protections.
Tor Browser 7.5.6 has a big…
Tor Browser 7.5.6 has a big bug in NoScript which makes Javascript-blocking very useless.
OMG please revert back to…
OMG please revert back to old style. Where's the advanced settings to turn off plugins, even the about:config page is different. DuckDuckGo does not work, and of course when you're on full secure lock down, neither does Google.
I used to go security settings, HIGH, advanced, turn off all plugins, then about:config and turn off JAVA proper. Now I'm unsafe.
The new about:tor page is…
The new about:tor page is really nice, but I miss the "am I on tor?" link.
And I agree with the others about the User Agent. If you don't fix this at least give us a tip to fix it in about:config
That link is gone as we had…
That link is gone as we had numerous false negatives in the past and Tor shipped in Tor Browser does a check whether it is working correctly anyway.
There would be no false…
There would be no false negatives with an onion mirror of check.torproject.org.
No Script has a mind of its…
No Script has a mind of its own now. New Tor circuit for site is gone too. And know matter how many years go by, no one is going to fix the incessant cloudfare problem? The fact that websites know that an incoming request is from a Tor user is something that should've been solved long ago as well. We aren't free to do simple internet searches anonymously.
I wish all of you the very best! I mean that! But the Tor infrastructure is hand-cuffed somewhere, and the primitive versions of Tor worked the best! Goodbye Tor! Hopefully we can re-enage one day, but this is getting far to fragmented and disorganized for the average user with ambiguous scalability for the ones who support you
Chill out dude. Install Tor…
Chill out dude.
Install Tor on your computer or network, and use it with Firefox ESR edition.
And for Cloudflare thing, check this out
https://notabug.org/themusicgod1/cloudflare-tor/
No, the New Tor circuit is…
No, the New Tor circuit is not gone, it moved where it better belongs to: the URL bar, more specifcially behind the "lock" icon/identity box showing information about the website. See our new onboarding and blog post.
"No, the New Tor circuit is…
"No, the New Tor circuit is not gone, it moved where it better belongs to: the URL bar, more specifcially behind the "lock" icon/identity box showing information about the website."
I'm not bothered by the new icon but I don't know why you think it "belongs" so much to the URL bar. IMO it wasn't worth losing so much time coding and developing a new icon when the Tor Button was doing the job perfectly.
The problem is/was that the…
The problem is/was that the icons on the toolbar are not for specific tabs but for the whole browsing session. For instance the update status (the blinking Torbutton icon if you run an outdated version) is not dependent on a particular tab. Yet the circuit display makes only sense with respect to a URL loaded in a particular tab. The mixing of tab-specific/non-tab-specific items in Torbutton was very confusing. We solved that for the circuit display by putting it directly into the identity box which is collecting all the site-specific information anyway.
Can I remove the "flexible…
Can I remove the "flexible space" on either side of the address+search bar without compromising anonymity? I hate not being able to visually confirm the ends of URLs. Version 8.0 fades and hides the ends from view, so you have to click and scroll sideways each time.
Yes, that should be fine.
Yes, that should be fine.
Tor borwser przestał działać…
Tor browser przestał działać z czytnikami ekranu na systemie Windows takimi jak Nvda. Teraz aplikacja jest nie możliwa do używania przez osoby niewidome. Proszę o naprawienie.
We have this bug open:https:…
We have this bug open:
https://trac.torproject.org/projects/tor/ticket/27503
You reveal the IP, port,…
You reveal the IP, port, transport protocol, and most of the fingerprint of a bridge in the large GIF in the post under "Improved Bridge Fetching". Outing that bridge means its metadata is almost as quickly discoverable as those of the bundled bridges unless it was one before. Please consider that.
All bridges be blocked, need…
All bridges be blocked, need more dostributed, better with everyone could be a entry node, no law issue like exit node.
My system is Vista and I use…
My system is Vista and I use chrome+ff. it said I cant get the updates anymore from Tor. I cant afford to buy new system and i still stick to my old fashion one i got used to for up to10 years. please let me know if it is possible. I use Tor to be anonymous for some websites I most visit per day. I really want it back. I am not that young to learn the new thing and new systems :( please help me out of this :( make some exception for those old ones like me who can not change their habits.
If you cannot change the…
If you cannot change the operating system on your machine, one option is to boot on a Tails usb key when you want to use Tor Browser:
https://tails.boum.org/
By the way, Windows Vista is not supported by Microsoft anymore, so it is not receiving security updates.
"option is to boot on a…
"option is to boot on a Tails"
OK, but Tails has no (editable ) persistent Entry Guard?
An essential Tor security standard.
My initial thoughts: …
My initial thoughts:
sandboxed-tor-browser now doesn't work (and I imagine it probably never will again.) That's not unexpected, but it is sad.
I don't like the new about:tor. It feels like an advertisement, and I don't particularly want to be advertised to every time I start my browser. "Explore. Privately." is just plain tacky. As for "the world’s most private browsing experience", it feels like you're trying to draw a comparison to other software - but given that there isn't any other software in Tor's class, all that does is bring you down to their level.
It's hard to explain, but the old about:tor screen was friendly and calming. This one is much less so.
The tutorial obviously isn't meant for me, but I would point out that the word "onboarding" also feels like marketing-speak.
I don't like that the onion icon is not brightly colored. I spend a lot of time using both Tor Browser and Firefox, and I want to have an obvious visual cue to tell them apart. Like about:tor, the bright green onion was comforting. The new onion icon is quite hard to see, at least with the dark desktop theme I'm using.
The new NoScript menu consists entirely of cryptic icons. Well, as wonderful as NoScript is, it's never been a paragon of UI design, but this seems worse than before.
With all that said: *thank you* to everyone working on Tor Browser. I'm only griping because of how well-constructed the old UI was, and I hope and expect that in time, the new UI will be even better.
I agree about the "about:tor…
I agree about the "about:tor" page. It's now like those ridiculous Apple ads full of empty advertising jargon. Anonymity as a consumer good is a trend that Tor project should resist and not follow. It gives a sense of trickery and of constant changes for the sake of increasing market share.
The first page you see should be simple, informative - and as boring as bureaucracy. "You're connected to Tor, you're using this version, here's some links to more info." That gives the user more confidence that the Browser itself is an ordinary and boring (reliable!) tool.
Just want to say a MASSIVE…
Just want to say a MASSIVE THANK YOU to everybody who works on these browsers and tor in general, those out front and behind the scenes. The unsung heroes and heroines (and whatever such label a non-binary person might use), you are LOVED. xo
whoer.net now correctly…
whoer.net now correctly detects my real OS no matter how many times I choose a New Identity; this never happened before!
https://trac.torproject.org…
https://trac.torproject.org/projects/tor/ticket/26146
Can I see my chain of nodes…
Can I see my chain of nodes in the new TB?
Yes, click on the left of…
Yes, click on the left of the URL.
Please make this compatible…
Please make this compatible with Vista. Plz.
We don't have resources to…
We don't have resources to keep supporting it. By the way Vista is not supported by Microsoft anymore, so it is not a good idea to keep using it as it is not receiving security updates.
hi, can't use it in china, I…
hi, can't use it in china, I can't open any dot onion website using 8.0 version, and when I click request a bridge from tor project, it shows unable to obtain a bridge from bridgeBD 0x805a2ff4, does anyone can tell me what to do? Im a little confused, thanks
The bug obtaining a bridge…
The bug obtaining a bridge directly from BridgeDB should be fixed by now. Does it work better for you now? That said, dealing with China is tough. Last we heard the meek-azure transport is still working. Maybe that could be an option for you as well?
All of the functions…
All of the functions relating to Tor used to be in one place, the attention-grabbing TorButton icon, but in this version they are scattered in three or more places. It is less intuitive. "New Identity" and "New Circuit" are mixed in with the jumble of Firefox options in the hamburger menu (that we aren't supposed to touch lest our anonymity be jeopardized) and appear as if they have the same worth, i.e. to just ignore them rather than understand their importance and purposely use them.
That's only partly true. Yes…
That's only partly true. Yes, those options are available on the hamburger menu but only as "fallbacks". You have "New Circuit" option with the circuit display on the left site of the URL bar (clicking on the "i" icon) indicating that what you and choose for an option is directly tied to the URL you have open. "New Identity" will get an own button on the toolbar soon, we were not able to finish that item before Tor Browser 8 got out.
Is the user agent spoofing…
Is the user agent spoofing broken in 8.0? Type user agent into duckduckgo and it is no longer showing Windows NT 6.1 but
https://trac.torproject.org…
https://trac.torproject.org/projects/tor/ticket/26146
Mind sharing the useragent…
Mind sharing the useragent string of TorBrowser 8 :)
It depends on the platform. …
It depends on the platform. :) https://hg.mozilla.org/mozilla-central/rev/9c586454144b has all the possible four options.
Too many bugs. I'm listing…
Too many bugs. I'm listing up all issues, please do something!
1. There's so many "Firefox" word in about:preferences which you failed to replace them properly,
2. You forgot to check "Prevent accessibility service from accesing your browser"(IIRC) by default,
3. You forgot to disable "View Firefox Studies" link and its contents (Firefox Data collection and use section),
4. Just remove "Firefox Data Collection and Use" section because it is creepy,
5. In Permissions, Location/Camera/Microphone should have "Block new requests asking to access" checked-on by default,
6. When the user changed the search engine to other provider, Tor Browser forcefully changed it to DuckDuckgo,
7. When I visit https: .onion, the URL bar shows green onion + pad lock icon, but the browser complain about self-sign certificate. Can't you just ignore this already??
8. And your updater still deliver Windows 32bit version. Why I can't reveive 64-bit of TBB?
That's a long list. Let me…
That's a long list. Let me answer you in reverse order:
8) Because your Tor Browser is asking for a 32bit update. Once you start with a 64bit Tor Browser that one will ask for a 64bit update. We have https://trac.torproject.org/projects/tor/ticket/24196 for updating 64bit capable Tor Browser users that use a 32bit build to 64bit.
7) Maybe? It seems to be a misconfiguration on the sever-side, though, to me. We have https://trac.torproject.org/projects/tor/ticket/13410 for that.
6) Could you give me steps to reproduce this bug?
5) I think we take care of that by not compiling WebRTC in and flipping related preferences.
re 4)-3) and 1): yes there is clean-up to be done on the about:preferenecs page see: e.g. https://trac.torproject.org/projects/tor/ticket/26504
2) I don't think we want to check that checkbox by default. That leaves users that depend on those tools with a broken Tor Browser.
Hey, and when I open about…
Hey, and when I open about:config, I can see many https: link to .mozilla.org.
Why you can't replace them to empty string?
We could. However, some we…
We could. However, some we need and some we don't need. It seems easier to focus on particular features that are harmful and make sure they are disabled than just removing any URL that has "mozilla.org" in it.
Sorry, though I see the…
Sorry, though I see the effort you spent, I'm not happy with 8.0
Where is the am I on tor button?
Where is the change channel for this page button?
Where is it displayed which countries are used for my internet access?
My impression is that we loose control and anonymity with the latest version of tor.
I hope you will turn it back.
No. The latter two items…
No. The latter two items moved into the URL bar, behind the "i" icon showing information about the currently visited URL. It feels much more natural having that information there than in a generic Torbutton menu that is for the whole browser and not just a particular tab.
The link to check.torproject.org got removed as in the past we got a bunch of false negative reports that scared users and Torbutton is automatically checking whether you are connected to Tor anyway and indicating if not. Thus, this check is redundant and error-prone.
The Bing translation tool at…
The Bing translation tool at https://www.bing.com/translator completely breaks under 8.0. I can get it working by disabling restrictions from the tab. Simply "trusting" each of the referenced domains is NOT enough to restore the function.
What are the additional permissions that disabling restrictions on the tab is enabling that trusting domains alone does not do?
What restrictions are you…
What restrictions are you disabling? Are you setting the security slider away from the standard level?
For Bing Translator I …
For Bing Translator I "Disable Restrictions for This Tab" and then it works. But I don't understand what I need to change permanently.
I actually think that#s…
I actually think that's https://trac.torproject.org/projects/tor/ticket/26624.
in older versions about…
in older versions about:config listed 300+ configurable noscript options.
in v8.0 it does not list even one, and the options in in noscript itself have vastly been reduced.
more regression!
That's not a regression…
That's not a regression. That's due to the new NoScript. WebExtensions don't have access to preferences anymore, thus the new NoScript does not have those anymore either.
152 bugs! If the new Firefox…
152 bugs!
If the new Firefox looks like as stable and secure as Adobe Flash, what can we expect from Torbrowser then?
I really appreciate the hard work but will it be worth to try fix and fix over and over again this new mozilla colander style browser that is creating problems over and over again with new fashionable unnecessary functionality?
Modifying a bad product costs many ours of people working to make it work with no guarantee because of troublemaker mozilla, and that is sad, because Tordevelopers and their users deserve better.
However, given the situation, thank you for your hard work and efforts and hopefully this fashionable long term damage that mozilla is creating will not cost lives or will unnecessary fill jails with innocent people.
SEVERE BUG. about…
SEVERE BUG.
about:preferences#privacy
Cookies and Site Data
Selected: "Block cookies and site data"
[ Exceptions... ] -> [https://example.com Allow for session]
But it seems Tor Browser is not eating cookies so I can't login to example.com!
HELP!
I tried to login to https://trac.torproject.org/projects/tor/newticket
with "https://trac.torproject.org Allow for session" settings, SAME RESULT.
WTF is going on!?
I had to use Firefox Extended Support Release version 60 with Tor
to login to example.com. I feel VERY insecure.
I was fine with TBB 52 era, but now this!?
Please fix TBB ASAP!
Could you give me steps to…
Could you give me steps to reproduce your problem as this seems to be a non-standard Tor Browser configuration?
It's not possible to start…
It's not possible to start the navigator.
The error message is: "Tor unexpectedly exited.This might be due to a bug in Tor itself, another program on your system, or faulty hardware. Until you restart Tor, the Tor Browser will not able to reach any websites. If the problem persists, please send a copy of your Tor log to the support team"
What operating system and…
What operating system and version are you using?
i have the same issue. i'm…
i have the same issue.
i'm on osx 10.9.5
OSX version10.9.5
OSX version10.9.5
This is https://trac…
This is https://trac.torproject.org/projects/tor/ticket/27482. This will be fixed in Tor Browser 8.0.1 by a patch to tor or a newer tor version. Meanwhile using the latest alpha release, 8.5a1 (https://decvnxytmk.oedi.net/projects/torbrowser.html.en#downloads-alpha), which is almost the same, should be solving your issue. Sorry for the inconvenience.
Your welcome…
Your welcome…
No more Vista support ????…
No more Vista support ????.
I do not want (or can afford) to upgrade to a more sophisticated version of Windows spyware.
Can I still use the old version of TOR ?
In my opinion you are moving backwards with TOR , too many "features"
But I must thank you whole heartedly for providing this program.
Thanks for the new release…
Thanks for the new release. Apparently it is not compatible with the use of FireJail and Firetools for sandboxing it (always get a message: "Your tab crashed, restart...."). Too bad.
Otherwise, the experience is cool, so far.
Yes, we have https://trac…
Yes, we have https://trac.torproject.org/projects/tor/ticket/27407 for that. We actually think this is a Firefox bug as this got reproduced with a vanilla Firefox, too. Thus, we have https://bugzilla.mozilla.org/show_bug.cgi?id=1488078. They might have problems reproducing the bug. So, if you could help them with that, then that would be the first step getting it properly solved. :)
Noscript does not save the…
Noscript does not save the whitelist settings(in `Per-site Permissions`), they only remain there for as long as the browser is running. If I restart the browser all entries I made there are gone.
Steps to reproduce:
- Download Tor Browser Bundle 8.0
- Run `./start-tor-browser.desktop` in the terminal
- Under `Per-site Permissions` in the noscript options, add any site and set it to trusted
- Close the browser
- Open it
- Go to `Per-site Permissions` in the noscript options
- The entry is not there anymore
I'm on fedora 28, 64 bit.
Yep, that's https://trac…
Yep, that's https://trac.torproject.org/projects/tor/ticket/27175.
Thanks for the fast reply!…
Thanks for the fast reply!
Looks like nothing from noscript will be saved, then. I assume there isn't any workaround to that at the moment?
We need to investigate but…
We need to investigate but right now, I know of none. Interacting with the new NoScript has been quite... challenging.
I see, thanks for your time…
I see, thanks for your time.
First of all, I would…
First of all, I would encourage every one check Tor Browser "fingerprintability" before updating to 8.0 and after the update. For me, using Panopticlick, it went from non-unique (on 7.5.6) to nearly-unique (on 8.0). oO
Now, I got a couple of issues with 8.0:
Thanks for your efforts in making privacy available!
Thanks, in advance, for your answers!
First of all it's not…
First of all it's not surprising that Panopticlick is reporting that for you. I mean how many Tor Browser 8 versions does it have seen so far, compared to *all* the browser fingerprintings over the years? Right, essentially none, hence the result: Panopticlick is heavily biased and not a good test for measuring Tor Browser fingerprintability.
Regarding issue 1) canvas extraction is not allowed by default. You can test that on one of our test sites: https://people.torproject.org/~brade/tests/canvasTest.html. What we did though, is greatly reducing the "prompt-fatigue" by using a Mozilla patch https://bugzilla.mozilla.org/show_bug.cgi?id=967895 and sending white noise for all users.
Regarding issue 2) This is https://trac.torproject.org/projects/tor/ticket/27175 and we are looking into it.
Thanks for your answers, I…
Thanks for your answers, I've got a couple new questions though:
You should get a popup (see…
You should get a popup (see the tests I linked above) which should allow you to enable canvas.
Regarding 2) there are, alas, no good tools for that yet. We try to make our FPCentral Google Summer of Code project into such one (a beta can be found at: http://ngp5wfw5z6ms3ynx.onion/) but we did not have as much time to maintain and develop it as necessary yet. :(
— Platform macOS, Tor…
— Platform macOS, Tor Browser 8.0 —
Regarding 2)...In Tor Browser 7.5.6 and earlier versions, fingerprint tests consistently revealed screen resolution '1000X1000'. FPCentral Google Summer of Code project: http://ngp5wfw5z6ms3ynx.onion/tor shows 'SCREEN RESOLUTION 1000X998. Your Tor browser is not at the recommended size. It should be either at 1000x1000 or at a multiple of 200x100.' With Tor Browser 8.0, this issue, '1000X998', or '1000x998x24' persists in all other fingerprint test results, including Panopticlick, whoer.net, amiunique.org, more... Please fix this issue so that when Tor Browser opens, the screen resolution is 1000x1000, and not 1000X998. Thanks
Which operating system is…
Which operating system is that? And this is with a default, unmodified Tor Browser 8?
1) Can you please add an…
1) Can you please add an extension to the Tor browser that has the same features as Self-Destructing Cookies with it enabled by default on all sites. This would go a long way to prevent unintentional tracking along with it being officially added to the browser we don't have to worry about the extension suddenly becoming malicious, harvesting user data or making people less anonymous by having to install it themselves.
2) Please put a priority on fixing User Agent issue this can have detrimental consequences for people who need it.
On Linux, the "see my path"…
On Linux, the "see my path" button in the new onboarding wizard opens a new tab with the ddg onion, and then opens the box that normally opens when the site name is clicked on (the box that says "secure connection" and "permissions" etc). I assume it is trying to open the Tor Button circuit display but finding the wrong ui element? I thought it was because i'd reordered my toolbar, but changing the order of the widgets doesn't seem to change the behavior: i always get to the site info box from the wizard's "see my path" button.
Bedroom Chinese users, built…
Bedroom Chinese users, built-in meek-azure has been blocked by China, the next is the log
9/6/18, 14:51:02.531 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
9/6/18, 14:51:02.531 [NOTICE] Opening Socks listener on 127.0.0.1:9150
9/6/18, 14:51:04.743 [NOTICE] Closing no-longer-configured Socks listener on 127.0.0.1:9150
9/6/18, 14:51:04.743 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
9/6/18, 14:51:04.743 [NOTICE] Closing old Socks listener on 127.0.0.1:9150
9/6/18, 14:51:22.314 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
9/6/18, 14:51:22.315 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
9/6/18, 14:51:22.315 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
9/6/18, 14:51:22.315 [NOTICE] Opening Socks listener on 127.0.0.1:9150
9/6/18, 14:51:26.127 [NOTICE] Bootstrapped 5%: Connecting to directory server
9/6/18, 14:51:26.129 [NOTICE] Bootstrapped 10%: Finishing handshake with directory server
9/6/18, 14:52:26.148 [WARN] Problem bootstrapping. Stuck at 10%: Finishing handshake with directory server. (DONE; DONE; count 1; recommendation warn; host 97700DFE9F483596DDA6264C4D7DF7641E1E39CE at 0.0.2.0:2)
9/6/18, 14:52:26.149 [WARN] 1 connections have failed:
9/6/18, 14:52:26.151 [WARN] 1 connections died in state handshaking (TLS) with SSL state SSLv2/v3 read server hello A in HANDSHAKE
9/6/18, 14:52:26.191 [NOTICE] Closing no-longer-configured Socks listener on 127.0.0.1:9150
9/6/18, 14:52:26.191 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
9/6/18, 14:52:26.191 [NOTICE] Closing old Socks listener on 127.0.0.1:9150
9/6/18, 14:52:27.111 [NOTICE] Delaying directory fetches: DisableNetwork is set.
Which tools would you advise…
Which tools would you advise as a replacement of Panopticlick for measuring Tor Browser fingerprintability?
Hello, i have a question…
Hello, i have a question regarding the renaming of the Tor Browser folder.
I like to have older TBB versions and i rename the folders with an added version number. Before this new version 8.0, i was able to rename the folders after each update (for example from "Tor Browser 7.2" to "Tor Browser 7.3" and then after starting the shortcut "Start Tor Browser", it still worked.
Now after i updated to 8.0 and then changing my folder name from "Tor Browser 7.5" to "Tor Browser 8.0" it doesn't work anymore. After clicking the shortcut "Start Tor Browser", it opens the firefox.exe, but Tor itself is not loaded before that and also the onion symbol in the toolbar is not there. Also no site seems to work. Renaming it back to "Tor Browser 7.5" is making it work again.
Is there a workaround to rename the folder while functionality is still given? Thanks in advance.
Not that I know. Might be…
Not that I know of. Might be interesting to understand why this happens, though. Let us know what you find!
Hi, is it only me or is…
Hi,
is it only me or is NoScript no longer saving any changed presets? I normally start with "Default - everything off (nothing is allowed)". But the changes made in the add-on setting page is gone after every start of the browser.
This is probably https:/…
This is probably https://trac.torproject.org/projects/tor/ticket/27175 and we are looking into it.
With the release of 8.0 i…
With the release of 8.0 i have issues with HTML5 video playback. To reproduce the issue and rule out an error in the settings, i used a fresh install, with default settings.
Videos are no longer click-to-play. With Security Level on Standard videos automatically start to play. With Security Levels on Safer and Safest videos don't play at all. To play videos with the higher Security Levels the site needs to be trusted in NoScript. Trusted sites however play videos automatically.
This should not happen, especially since Safer and Safest clearly say "Audio and video (HTML5 media) are click-to-play."
I just tried with Youtube on…
I just tried with Youtube on a Linux system and it worked for me as expected (the video is click to play on the safer level). Could you give me a link that worked previously but does not in Tor Browser 8 anymore?
The default user agent is…
The default user agent is broken in Tor 8.0. The string is set correctly at general.useragent.override;Mozilla/5.0 (Windows NT 6.1; rv:60.0) Gecko/20100101 Firefox/60.0 but is not passed through. See http://ip-check.info/index.php
Funfact: privacy…
Funfact: privacy.resistFingerprinting(about:config) blocks general.useragent.override.
Where is java button enable…
In 8.0 new version..
Where is java button enable/disable?? diaspear?? It was very useful.
Why there is no ne Tor for Windows Xp and vista..still many using!!
also 32 bit version is necessery too.
Good Job!
Good Job!
HOW CAN I DOWNGRADE TO 7…
HOW CAN I DOWNGRADE TO 7 PLEASE ?
THE 8 DESTROYED MY CLASSIC DISPLAY, MY FLASH, MY DOWNLOADS FROM YOUTUBE, EVERYTHING
I HATE THIS INTERMINABLE COURSE TO FALSE IMPROVING'S, AGAINST FALSE ENEMY'S, ETC.,
AFTER SO MANY YEARS WHEN WILL YOU UNDERSTAND THAT YOUR EXTRAORDINARY WORK, UNFORTUNATELY REMAINS A TOOL FOR US HELPING FOR SOME OTHER ACTIVITY
ITS A TOOL FOR US, NOT A MUST BE "IN", A LETS CHANGE THE TOOLBAR IN AN INAPPROPRIATE PLACE :
EXAMPLE OF STUPIDITY :
1)
THE NAVIGATION BAR IS STATIC, DOES NOT CONTAIN THE INFORMATION WE USE TOR FOR. WE DON'T EAT ADRESSES, BUT CONTENTS.
2)
THE BOOKMARKS EITHER. THOSE ARE STATIC THINGS WE DO NOT USE TOT TO READ BOOKMARKS BUT CONTENTS
3)
THE ONLY THING IN TOUCH WITH THE CONTENTS IS THE TAB CONTAINING THE NECESSARY, THE GOAL OF TOR, THE CONTENT.
OR, SOME IDIOT HAS SEPARATE THE TAB FROM THE CONTENT. INCREDIBLE. STUPID.
ITS COMPLETELY CRAZY
THE REALTIME WORK
I stopped using Firefox…
I stopped using Firefox because the new version had a lot of addons-related efficiency problems. Now I see this Tor is the same but I can't stop it from updating, I try to install the older version without any success.
I wish you could let the user decide which version they want to use at their own risk. For some of us, this update means we have to stop using Tor altogether.
Giving away the user agent…
Giving away the user agent is dangerous! Many people told you already. Please fix the user agent!
Hi, Tor Browser 8.0 is not…
Hi,
Tor Browser 8.0 is not usable by a user who is blind. I'm using NVDA screen reader on Windows 10, and I cannot use Tor Browser at all. Please test by installing NVDA and then running Tor Browser.
Thanks.
I am sorry for that. This is…
I am sorry for that. This is tracked in https://trac.torproject.org/projects/tor/ticket/27503. Alas, there is no easy way to fix that. :(
Is it safe to set 'dom.ipc…
Is it safe to set 'dom.ipc.processCount' to '-1'? It would be really nice to have one process per tab, providing more isolation between different sites.
Problems saving websites…
Problems saving websites locally. Pictures and layout of websites are lost.
Thanks, I filed https://trac…
Thanks, I filed https://trac.torproject.org/projects/tor/ticket/27542 for that.
first you took away the…
first you took away the option to choose the country of the exit node when phasing out vidalia. now you take out even the option to SEE which exit country you are using with version 8. why do tor developers need to hide important information from users like in which countries the tor nodes are you are connecting to? is it because lately all tor nodes happen to be on the same country which is a huge security risk? is the tor browser no longer secure? i'll not donate any more money to the tor project until i see a change to transparency and give the users back the control and information we always had before. and i'm rolling back to version 7 obviously since i want to see if i'm using a node in the USA or in my own country. SHAME ON YOU. really. i'm speechless....
Please calm down. We have…
Please calm down. We have announced the changes on our blog post to this release (just scroll above and read it), we gave an explanation you would get after starting the new version after the update and we included an onboarding (upper left corner) that is explaining the (new) features. In short: the circuit display and other related functionality moved to the "i" (identity) box to the left in your URL bar as it is site-specific. We think if fits there way better than in the Torbutton menu.
Thanks for this stable…
Thanks for this stable release! All working fine. Must have been a tremendous job to get all to work properly.
One question: Will adding some minor cosmetic changes using a userChrome.css script compromise anonymity?
Hard to say. It might depend…
Hard to say. It might depend on the exact changes you make.
Like replacing the tab…
Like replacing the tab throbber and changing colors of bookmark folders. Understand this is not high priority to say the least, but would anyway be interesting to know.
Thanks for your time.
Why TLS 1.3 still disabled?…
Why TLS 1.3 still disabled? 000-tor-browser.js pref security.tls.version.max;3 contains legacy description ("Enable TLS 1.1 and 1.2")
Good point, I opened https:/…
Good point, I opened https://trac.torproject.org/projects/tor/ticket/27535.
Ditto, leaking OS…
Ditto, leaking OS information in UA when JS is disabled is not nice.
What is the JavaScript…
What is the JavaScript argument here? You leak OS information as well if you have JS disabled, even if the UA is the same as the font whitelist we ship is OS specific.
When previewing/submitting a…
When previewing/submitting a comment here with security settings set to safest, TB8.0 started to reload continuously and memory usage increased until my virtual memory was all used. If stopping the repeated loading, the site was broken. In Windows event log there was an error message of some program specific local authorization problem DistributedCOM.
Tested again with security settings set to safer and the problem is now gone.
Yes, that's an old bug which…
Yes, that's an old bug which we still don't have fixed: https://trac.torproject.org/projects/tor/ticket/22530.
Thanks for the info!
Thanks for the info!
As expected, Quantum era FX…
As expected, Quantum era FX has disabled security and usage features.
Specifically, pre-Quantum noscript addon (by Maone at informaction) had options/prefs that chose whether to show or disable noscript elements in html.
For example of usage on the web, twitter shows no content except a notice "We've detected that JavaScript is disabled in your browser. Would you like to proceed to legacy Twitter?" with a "Yes" button.
Clicking the "Yes" button sends page to the same content but on mobile.twitter.com/ instead of on twitter.com/
This is "Yes" button is useless, because the mobile.twitter.com/ page also shows the same ".. JavaScript is disabled.. proceed to legacy Twitter" message.
Workaround:
via Firefox's text menu, "Page Style", "No style" will show Twitter page content.
Long-term "hack" is to edit userContent.css:
I haven't reviewed userContent.css syntax but Developer Mode and view-source of a twitter page should rapidly find the css that needs editing.
I assume userContent.css can apply these styles of noscript elements to all web domains. Must find regarding userContent.css, whether styles applied generally precede or if they follow styles restricted to domains.
Relevance to Firefox and Tor Browser:
This confirms the value of pre-quantum noscript addon's options/prefs
If someone (?) eventually restores lost addon functionality, I foresee further divergence of tor browser from Firefox, but expect that will require an increase in coding workload )*:
@namespace url(http://www.w3…
@namespace url(http://www.w3.org/1999/xhtml);
@-moz-document domain("twitter.com") {
form[class=NoScriptForm] { display: none !important; }
}
on userContent.css
I wonder how I missed your…
I wonder how I missed your reply two days later... (according to dates shown here)
Your css rule worked.
I first only added your rule to my rules, but that had no effect.
I then removed all other rules in
@-moz-document domain("twitter.com")
and your rule worked.
I also had somehow lost the initial
@namespace url(http://www.w3.org/1999/xhtml);
line.
So my userContent file had been ****ed up
Sometime in the future, I'll add my other twitter fixes back into userContent (one of my rules had been very close to yours... possibly a child element of yours)
Thanks
Also for lurkers, this is the 'traditional' way to write the rule:
form.NoScriptForm{display:none!important;}
Reading Twitter in tbb8 is …
Reading Twitter in tbb8 is 'incurable' mess. I have returned to tbb7 (for.... how long?)
Problem: Copying tbb8 bookmarks to tbb7 isn't straightforward.
Quantum (Firefox in tbb8) uses a different places.sqlite, and pre-quantum (Firefox in tbb7) rejects my attempt to copy places.sqlite from tbb8. Instead, tbb7 renames places.sqlite to places.sqlite.corrupt, then loads its automatic backup into its bookmarks.
Background:
My Options/Preferences>Advanced>Update is
(.) "Check for updates, but let choose whether to install them"
I saved a copy of tbb7 folder before tbb's upgrade to tbb8
__Workaround:__
Start tbb8.
Open bookmarks manager.
Backup to .json file.
Shutdown tbb8
Start tbb7.
Open bookmarks manager.
(Choose whether to manually delete everything in bookmarks menu and in bookmarks toolbar. I did.)
Restore, select the .json file created by Backup in tbb8.
2 or 3 "unresponsive script... Continue" popups. Procedure consumed (guess) 4 minutes on 2012 i5 PC running Windows 7 Pro x64
Result:
Bookmarklets and creating new bookmarks appear to be working during about 15 minutes of using tbb7 with the .json "restored" from tbb8 backup.
Notes:
tbb = tor browser bundle
I intend to report anything else that seems related to this 'workaround'.
I hope to experiment with "fixing" Quantum using a "throwaway install" of PortableApps Firefox.
What is the issue for you…
What is the issue for you here? Regarding bookmarks, can't you export the bookmarks in Tor Browser 7 with the bookmarks menu and import them in Tor Browser 8 the same way (in the latter with Ctrl + Shift + O and there Import and Backup)?
sorry for late revisit. Web…
sorry for late revisit.
Web searches found people using regular non-tbb firefox who fell into the same predicament. They disliked quantum after trying, then wanted to use their newest bookmarks in (pre-quantum) ESR.
------
Overview of predicament:
tbb7 updated to tbb8, which changed something in the sqlite file.
I used tbb8 for a while, accumulating additional bookmarks.
I then decided to return to tbb7.
I wanted tbb7 to use my most recent bookmarks
tbb7 couldn't accept the places.sqlite file that I dragged from tbb8 profile.
Thus the need for a workaround.
tl;dr workaround:
In tbb8, "backup" to .json file
In tbb7, restore from same .json file
During restoring, click "Continue" button in "unresponsive script..." alerts
-------
Almost 4 weeks (more than 30 accumulated hours) since this json workaround, nothing odd has occurred in tbb7.
------
about Ctrl + Shift + O - for the lurkers:
While in normal window of Firefox:
ctrl+shift+o opens bookmarks manager in Linux.
ctrl+shift+b opens bookmarks manager in Windows.
NoScript Extension: I…
NoScript Extension:
I noticed in tbb8 that noscript has very few options, and none are the "Hide noscript elements" or "Forbid meta redirections.." options as in pre-Quantum NoScript extension.
I keep setting NEVER CHECK…
I keep setting NEVER CHECK FOR UPDATES but you keep updating to 8.0 Why? I don't want that update cause it disables 2 important add ons making TOR useless to me
Why new Tor isn't working on…
Why new Tor isn't working on Win Vista anymore? It is possible to make version of new TBB for Vista? Please help me in this if You can, Thanks.
System: Tor Browser 8.0…
System: Tor Browser 8.0 using obfs4 bridge on macOS. Please implement the following modifications: (1) In the Circuit Display, replace the word 'Bridge' with an actual country name. (2) Move 'Show history', 'Toggle reader view', and 'Page actions' from the address bar to the Toolbar. (3) Include the 'New Identity' toolbutton in the Toolbar, Circuit Display, or Torbutton. (4) Implement a common User Agent string uniformly across all platforms so that the UA string will reveal 'Windows NT 6.1' (or another os). Tor Browser, the teams, and the volunteers are outstanding! Thank you.
I'm hearing that user agent…
I'm hearing that user agent spoofing is broken for this release. Unfortunately I use Linux so that makes me stand out even more. Is there going to be work on fixing this or should I not upgrade?
https://trac.torproject.org/projects/tor/ticket/26146
Will you guys fix the broken user agent spoofing on Linux and OSX?
If you update to Tor Browser…
If you update to Tor Browser 8 you'll stand out because you don't use a mainstream OS.
If you proceed to use the previous version you'll stand out because you'll be one of the few that keep using an outdated version of Firefox.
Pick your poison.
Please support Vista users…
Please support Vista users again, I know that Microsoft left supporting it but still many of us using this system.
Maybe some special edition of new TBB with a little bit older Firefox?
In the previous version of…
In the previous version of Tor I could set my scripts to block globally now with the new NoScript I go into settings set the default to uncheck everything so nothing is allowed, but when I restart Tor the settings are forgotten so the Default goes back to allowing almost everything. Very disappointing that it wont remember my settings on something as important as this, I want to go back to my old Tor version. Please fix Tor land.
We are on it: https://trac…
We are on it: https://trac.torproject.org/projects/tor/ticket/27175
How can i UNPACK torbrowser…
How can i UNPACK
torbrowser-install-win64-8.0_en-US.exe
manually?
Unpacker says "[0] no archive".
Thanks to Tor devs for all…
Thanks to Tor devs for all their hard work.
I do have an issue with TBB 8.0 but it is likely to be Mozilla that are to blame for this frustration..
TBB8 is the first to be based on a version of FF which disables 'legacy addons'. Which would be fine if they put as much effort into getting the various WebExt APIs working and supported as they've put into forcing everyone onto WebExts.
Unfortunately the API I will need to get my 'legacy' addon working isn't in FF60, and it will be a long while until we see a TBB based on the next FF ESR.
In the meantime, my heart leapt to see there is are 'extensions.legacy.enabled' and 'extensions.legacy.exceptions' prefs.
However, though it seemed the nightmare was over, in fact neither of these prefs seems to get my addon working; it is still listed as 'disabled'.
I will do some testing to determine whether there is particular functionality that is causing that addon to be disabled in spite of the prefs, or whether those prefs are a tantalising lie.
In the meantime, what experiences have others had with this so far?
(And before anyone starts with well-meaning warnings about the security risks of using addons in TBB, I wrote it myself, it's a relatively simple addon, I understand what it does, I need this functionality and I accept the calculated risk).
Hello Tor developers, …
Hello Tor developers,
Firstly, I would like to thank you for your hard work for making this excellent anonymity & anti-censorship tools for everyone. I'm relatively new to Tor Browser & Tor in general nor am I a tech savvy person. I've been using Tor Browser since TB 7.5.4 and this new release TB 8.0 is rock solid. However I'd like to express a concern about User Agent Spoofing (which other people have already said).
I've tested my fingerprint in Panopticlick and Whoer. Panopticlick shows that I have strong protection against fingerprinting (I usually use "Safer" on security slider), but it shows my operating system which is Linux x86_64, same with whoer.net.
I read your explanation as to why Tor developers decided to ditch UA Spoofing as there are many variables that webmasters can detect users' OS by other means, not to mention mobile users which can give negative impact to their browsing experience (i.e. getting desktop site instead of mobile version). I usually browse normal clearnet, nothing shady or illegal. However my concerns lie on the mindset of this decision.
While I can understand a lot of web technologies can break users' anonymity, I fear if this "the web standards mandate this new/old tech that can break anonymity, obfuscating it will result in little impact on users' anonymity while heavily impacting user experience, we might as well give up" mentality, this will result in weaker tools such as Tor & Tor Browser. I'm even disappointed when Mozilla started to add "features" that may lessen users privacy such as Pocket and other stuff.
As other users have suggested, maybe it would be better to enforce UA Spoofing to Windows UA regardless of their Desktop OS only, while keeping mobile to their UA. If you fear new users will likely quit using TBB altogether just because one of their favourite sites give them bad UX, maybe you can educate these users in Tor Browser User Manual when they first fired up TBB. I feel like educating users and giving them understanding and the solutions are much better than unmasking everyone. These days and age, people just don't like to learn nor do their research beforehand and if we keep following these people, it will weaken the only tools that us normal people have to having basic privacy & anonymity.
This is just my opinion & criticism and by no means an attack to Tor devs, so I hope you take it as such. Once again thank you to all Tor devs and congrats on the new TB 8.0 release :)
The problem is not bad UX…
The problem is not bad UX. The problem is that spoofing the UA for macOS for instance breaks things for users as there are (big) websites out there that assume OS specific functionality based on the User Agent. See: https://bugzilla.mozilla.org/show_bug.cgi?id=1405810 and similar bug reports.
Then give users a choice to…
Then give users a choice to select the user agent. You can show an icon having a drop down menu to select the user agent. If the user goes on one of such websites that you mention the user can switch to the appropriate user agent. You are compromising security for convenience. Give us a choice.
Are you serious? First, no…
Are you serious?
First, no websites should never do any "OS specific functionality" or "Browser specific functionality" for that matter. Don't you remember why the W3C was created for ?
Second, we're talking about TBB, a browser meant to be used without JS. People who care about "specific functionality" shouldn't use TBB, that's all.
What is your goal? Are you seriously trying to increase the TBB user base? What's your point?
Noticed differences between…
Noticed differences between Tor v7.5.6 and Tor v8.0
1) Tor v8.0 win 32bit from Torproject, the Tor button options new identity and new Tor circuit for this site is unavailable, not listed as an option.
2)Do not track option shoud be a separate check box
3)Using same settings on Tor v7.5.6 and Tor 8.0 security safest, no cookies, do not track strict protection my signiture revealed firefox version tested using http://ip-check.info/?lang=en/
Hello guys! I have a problem…
Hello guys! I have a problem. Big problem. After the update my Tor stopped to open.
my os - Mac OS 10.9.5
Update from previous version to 8. Logs are empty. There is only message what I see:
https://files.fm/u/vb8g3n78#/view/Screen+Shot+2018-09-07+at+10.28.36+AM…
I need to find my bookmarks because of it big problem what I have wtih this update.
Waiting for the answer. Thanks a lot.
Yes, that#s https://trac…
Yes, that's https://trac.torproject.org/projects/tor/ticket/27482 and cause by a missing patch in the tor version we ship. This will be fixed in the 8.0.1 point release. Meanwhile you could use the recent alpha version, 8.5a1 (https://archive.torproject.org/tor-package-archive/torbrowser/8.5a1/) which ships a tor version that contains the fix. Sorry for the inconvenience.
Is that network.ftp.enabled…
Is that
network.ftp.enabled;true
network.http.altsvc.enabled;true
network.http.altsvc.oe;true
network.http.spdy.enabled;true
network.http.spdy.enabled.http2;true
really save?
unfortunately my computer is…
unfortunately my computer is always freezing with the new update.
but it installs itself again and again.
so it has become worthless. sorry
Could you try starting fresh…
Could you try starting fresh over to check whether it works better for you? On which operating system are you on?